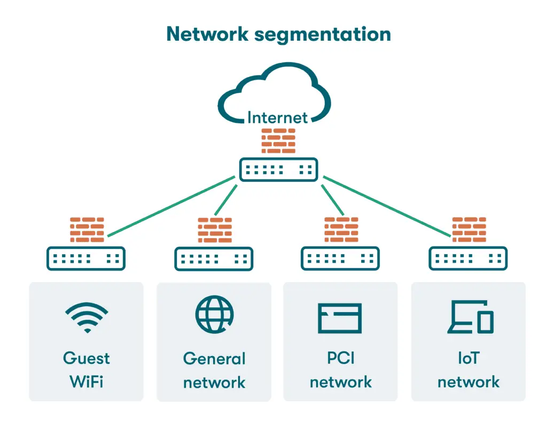
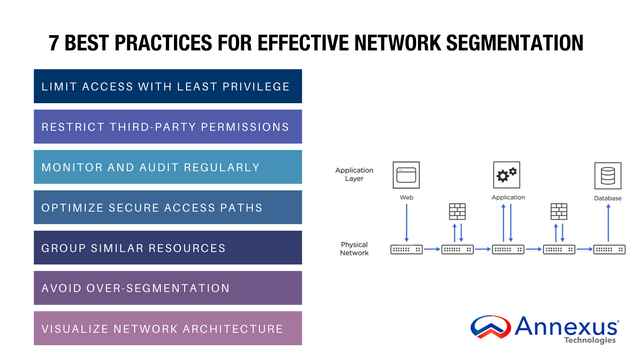
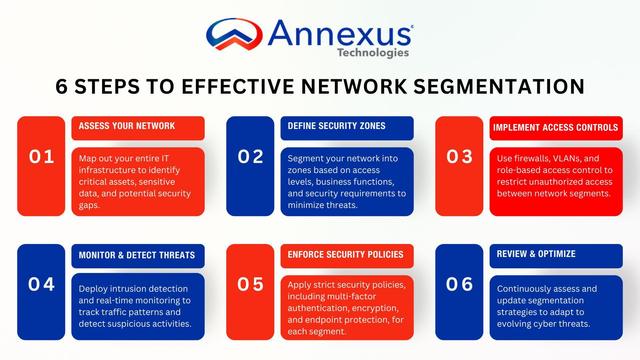
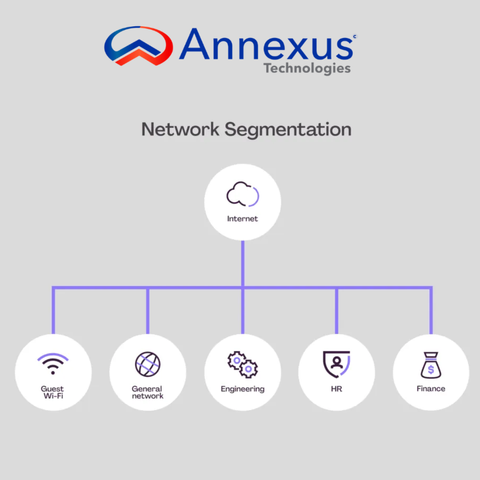
As digital transformation accelerates, the CPS that underpin #industrial organizations become increasingly interconnected with #IT and #OT networks, making it more difficult for organizations to enhance security, reduce cyber risk, comply with industry regulations and standards, and improve their overall operations.
By implementing OT industrial #NetworkSegmentation, organizations can begin to safeguard the security, resilience, and continuity of these operations — and ensure uninterrupted functioning of society and the economy. 🛡️ Read more: https://claroty.com/blog/how-to-accelerate-segmentation-alongside-the-xiot