Here is a blog entry describing how the good old deposit/withdraw #RaceCondition occurred in real life. As many lecturers, I use this example in my lectures, so next time this gives me an opportunity to talk about the ethical aspects of such a discovery.
#RaceCondition
Watching #claude troubleshoot a #racecondition between #docker Containers is really fun to watch as the Code behaves Different every time it's run
"the REAL issue is..."
🤣🤣🤣
Invoice Sequence Race Lock
Guarantee unique invoice numbers under heavy load.
#php #python #invoices #locking #racecondition #payments #reliability #backendsafety #performance #viralcoding
"Bẫy đèn xanh" trong self-hosted: Dịch vụ "chạy" chưa chắc đã "sẵn sàng"!
🔍 Lỗi phổ biến: Container hiển thị "healthy" nhưng vẫn gặp sự cố ngầm do:
- Database nhận kết nối nhưng chưa khởi tạo xong
- Reverse proxy cache lỗi 502 khi upstream chưa sẵn sàng
- Ứng dụng khởi động trước khi mount volume
💡 Giải pháp: Thiết lập healthcheck chi tiết + điều kiện phụ thuộc (depends_on) để đảm bảo các service đã THỰC SỰ hoạt động.
#SelfHosted #DevOps #RaceCondition #CloudComputing
#TựHost #Q
Session Race Condition Charges 47,000 Cards TWICE?!
SESSION RACE DISASTER! Flash sale network lag creates 340ms race condition! 47K customers charged TWICE ($299.99 x 2)! $14.1M overcharged! Payment processor SUSPENDED account! CTO RESIGNED!
#php #phpdisaster #session #racecondition #doublecharge #paymentfailure #productionbug #phpshorts #phpwtf #financialdisaster #careerending #flashsale
Oto błąd, który pozwalał za darmo zamawiać jedzenie z cateringu “Kuchnia Vikinga” i z jeszcze jednego
Istotne błędy bezpieczeństwa można znaleźć nawet jeśli nie jest się zawodowym pentesterem. Przekonał się o tym nasz Czytelnik Tomek Stojanov, który przekonał aplikację do zamawiania dietetycznego cateringu by w nieskończoność zwiększała mu saldo. Tomek to jednak uczciwy klient, więc postanowił błąd ujawnić. I dobrze się stało, bo – jak wykazała analiza – z tego samego błędu korzystał ktoś jeszcze. Już nie taki etyczny.
Chcecie darmowy obiad, śniadanie i kolację od Vikinga?
W połowie listopada do naszej redakcji zgłosił się Tomek, który nie jest ani programistą ani specjalistą od bezpieczeństwa, ale jest człowiekiem spostrzegawczym. W czasie korzystania z aplikacji cateringu dietetycznego o nazwie “Kuchnia Vikinga” zauważył coś dziwnego… Aplikacja pozwalała na złożenie zamówienia i anulowanie go. Po anulowaniu użytkownikowi naliczały się punkty lojalnościowe o równowartości kwoty zamówienia. Punkty mogły być wykorzystywane do opłacenia kolejnych zamówień. I teraz ważna rzecz:
Proces anulowania trochę trwał, a użytkownik mógł w trakcie tego “trwania” anulować dostawę po raz kolejny. I kolejny. I kolejny, zanim to pierwsze anulowanie dobiegło końca.
Poniżej film z akcji nagrany przez Tomka:
Błąd jak widzicie poważny. Mógł powodować straty finansowe po stronie dostawcy cateringu.
Tomek błąd chciał zgłosić, ale miał z tym problem…
Odezwał się do firmy MasterLife Solutions, która jest dostawcą aplikacji mobilnej dla Kuchni Vikinga. Ta odesłała go do serwisu Intigriti (służącego do obsługi zgłoszeń typu bug bounty), który dla osoby [...]
#Aplikacje #Żabka #CateringDietetyczny #Intigriti #KuchniaVikinga #MasterLifeSolutions #RaceCondition #TomekStojanov
🎉 Wow, someone found a "race condition" in Aurora RDS! 🚀 Meanwhile, #Hightouch is busy throwing buzzwords at us like confetti at a tech wedding—Composable CDP! Reverse ETL! ISO 27001! 🤯 But apparently, AI can understand your brand now...so maybe it can explain what "race condition" means while it's at it? 🙄
https://hightouch.com/blog/uncovering-a-race-condition-in-aurora-rds #racecondition #AuroraRDS #ComposableCDP #AIunderstanding #techbuzzwords #HackerNews #ngated
We Uncovered a Race Condition in Aurora RDS
https://hightouch.com/blog/uncovering-a-race-condition-in-aurora-rds
#HackerNews #RaceCondition #AuroraRDS #TechNews #CyberSecurity #CloudComputing #DatabaseManagement
Gestion des accès concurrents en Node.js à l'aide d'un mutex, entre autres.
Et oui, le fait que Node tourne sur un seul thread n'empêche pas les *race conditions*.
🔗 https://nodejsdesignpatterns.com/blog/node-js-race-conditions/
CVE-2020-27786 ( Race Condition + Use-After-Free )
CC: @ii4gsp
I feel like the US – in terms technical folk would understand – is in a #raceCondition.
It's a question of whether the pain caused by a collapsing health/social system and the explosion of consumer prices due to irrational tariffs will cause an dethroning uprising before the authoritarianism goes into full martial-law mode.
CVE-2020-27786 ( Race Condition + Use-After-Free ):
https://ii4gsp.github.io/cve-2020-27786/
#cve #uaf #cybersecurity #exploitation #infosec #exploit #racecondition #vulnerability
CVE-2020-27786 ( Race Condition + Use-After-Free ):
https://ii4gsp.github.io/cve-2020-27786/
#cve #uaf #cybersecurity #exploitation #infosec #exploit #racecondition #vulnerability
RHEL 9 OpenSSH packages affected by remote code execution flaw
https://stackdiary.com/rhel-9-openssh-packages-affected-by-remote-code-execution-flaw/
#OpenSSH #Vulnerability #RHEL9 #Security #CyberSecurity #CVE20246409 #RemoteCodeExecution #Linux #Fedora #RaceCondition #SIGALRM #Exploit #PatchManagement #Mitigation #Infosec #Threat #Hackers #Bug #Malware #Glitch #Audit #Syslog #Update #Enterprise #LinuxSecurity #NetworkSecurity #ServerSecurity #CyberThreat #SystemAdmin #TechNews #CVE #Mitre #NIST #OpenSource #DevOps #regreSSHion
Found a #racecondition in a productivity tool for teams limits the number of members a team can have depending on the paid plan. I managed to bypass that limit and have many more users (than the imposed limit) join the same team. 🎉
RegreSSHion strikes again: CVE-2024-6387
Last night a PoC code released which exploits a race condition on OpenSSH. Vulnerable versions listed as from 8.5p1 to 9.7p1!
PoC code:
https://github.com/acrono/cve-2024-6387-poc
More on the topic: This exploit relies on a 18 year old issue: CVE-2006-5051
This vulnerability is believed to impact nearly 12-14 million OpenSSH instances.
Important notice: To get root from the target machine, this exploit code needs a continuous connection like 8 hours to achieve race condition. So don't expect shell in minutes!
#exploit #exploitation #openssh #racecondition #vulnerability #ssh
The current #OpenSSH #racecondition #vulnerability PoC exploit depends on bruteforcing the Address Space Layout Randomization (ASLR) to guess addresses used by the sshd. Thus #exploitation currently appears feasible only if the ASLR entropy is low enough (platforms with 32-bit addressing or systems where ASLR is for some reason completely disabled). Of course this is something you should not rely on and patching is highly recommended as soon as possible.
If for some reason you need to mitigate the vulnerability on systems that don't have security updates or the updates are delayed you can apply the mitigations from the excellent post from Damien Miller at oss-security mailing list: https://www.openwall.com/lists/oss-security/2024/07/01/2
regreSSHion: Remote Code Execution in OpenSSH Server (CVE-2024-6387)
Date: July 1, 2024
CVE: CVE-2024-6387
Vulnerability Type: Race Condition
CWE: [[CWE-362]], [[CWE-665]]
Sources: Qualys
Synopsis
A critical remote code execution (RCE) vulnerability has been identified in OpenSSH's server on glibc-based Linux systems, allowing unauthenticated attackers to execute arbitrary code as root.
Issue Summary
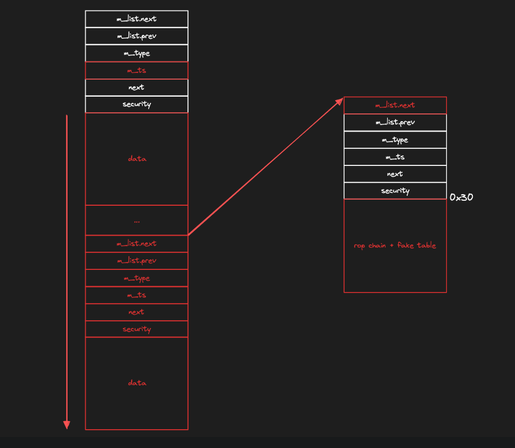
The vulnerability, identified as CVE-2024-6387, is a regression of a previously patched issue (CVE-2006-5051) and affects OpenSSH versions from 8.5p1 to 9.8p1. It arises from a signal handler race condition in the sshd server, leading to unsafe function calls within asynchronous signal handlers.
Technical Key Findings
The flaw involves sshd's SIGALRM handler, which calls non-async-signal-safe functions like syslog(), potentially leading to a heap corruption and enabling remote code execution. The exploit requires precise timing to interrupt specific code paths, leaving the system in an inconsistent state that can be exploited.
Vulnerable Products
- OpenSSH versions 8.5p1 to 9.8p1 on glibc-based Linux systems.
Impact Assessment
Exploitation of this vulnerability allows an attacker to execute arbitrary code as root on affected systems, potentially leading to complete system compromise.
Patches or Workaround
A fix has been implemented in OpenSSH by moving the async-signal-unsafe code to a synchronous context. Users are advised to update to the latest version or set LoginGraceTime to 0 as a temporary mitigation.
Tags
#OpenSSH #CVE-2024-6387 #RCE #RaceCondition #Linux #glibc #SecurityVulnerability #Exploit #Patch