SQL Injection (SQLi) 💉 – Everything You Need to Know
What is SQL Injection?
SQL Injection is a code injection technique that allows attackers to interfere with the queries an application makes to its database.
Types of SQLi:
1. In-band SQLi – Most common and easy to exploit.
2. Blind SQLi – Data isn’t visibly returned but can still be extracted through inference.
3. Out-of-band SQLi – Uses external servers to get results (less common but powerful).
4. Time-Based Blind SQLi – Server delay used to infer info from the database.
Attack Scenarios:
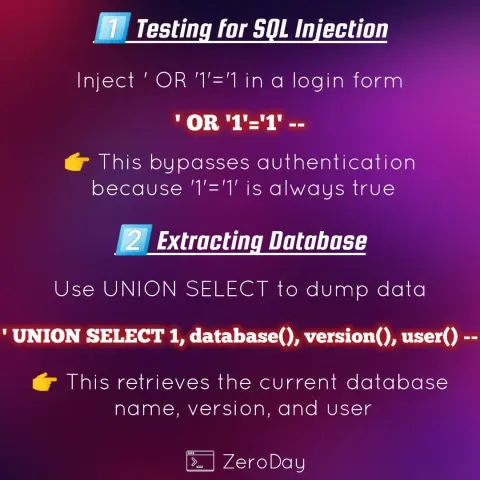
▫️Bypassing logins
▫️Dumping database contents
▫️Modifying or deleting data
▫️Escalating privileges
▫️Accessing admin panels
Common SQLi Targets:
🔹Login forms
🔹Search boxes
🔹URL parameters
🔹Cookies
🔹Contact or feedback forms
How to Prevent SQLi:
▪️Use parameterized queries
▪️Employ ORM frameworks
▪️Sanitize all user inputs
▪️Set least privilege for DB users
▪️Use Web Application Firewalls (WAF)
♦️Red Team Tip
Test all user input points, especially where data touches the database. Think beyond login forms—SQLi hides in unexpected places.
🔖Hashtags:
#SQLInjection #CyberSecurity #EthicalHacking #InfoSec #WebSecurity #RedTeam #BugBounty #Pentesting
⚠️Disclaimer:
This content is for educational purposes only. Always perform security testing with explicit permission. Unauthorized testing is illegal and unethical.