0-Click Exploit Alert: Just Opening a Folder Can Trigger Remote Code Execution on Windows 🚨
A newly disclosed vulnerability in Windows LNK (shortcut) files has raised serious red flags — and Microsoft isn't planning to patch it.
Here’s what happened:
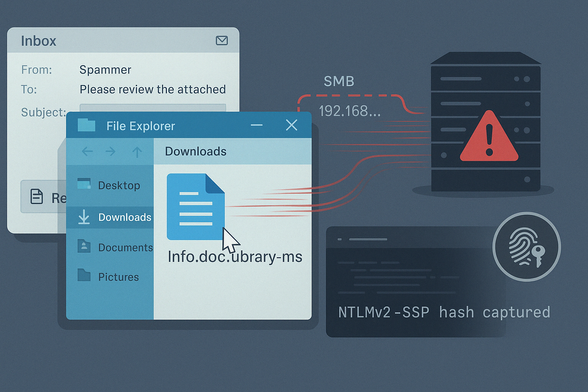
- A security researcher publicly dropped a working Proof-of-Concept that allows remote code execution just by getting a user to open a folder.
- No clicks. No prompts. Just browsing a directory is enough to trigger the attack.
- The exploit abuses the way Windows Explorer parses LNK files using COM interfaces like `IInitializeNetworkFolder` and `IShellFolder2`.
Microsoft's official response?
They say it “does not meet the security bar for servicing,” citing the Mark of the Web (MOTW) feature as sufficient protection.
But researchers disagree:
- MOTW can be bypassed — and has been, repeatedly.
- Similar LNK exploits have been abused in the wild since at least 2010.
- Now that a PoC is public, it’s only a matter of time before threat actors exploit it.
This is a classic example of a silent threat lurking inside everyday workflows — and it reinforces a harsh truth in cybersecurity:
Not all exploits need user interaction. Some just need you to look.
If your business relies on Windows systems and file sharing, now’s the time to rethink folder access, tighten segmentation, and review endpoint defenses.
Efani protects mobile communications — but threats like these remind us that endpoint security is a multi-layered game.