Leveling up your Microsoft Store on Windows experience | by Giorgio Sardo.
buff.ly/TPaciVo
#windowsdev #ai #microsoftstore #windows #appdev #msix #windev
Leveling up your Microsoft Sto...
#MSIX
Leveling up your Microsoft Store on Windows experience | by Giorgio Sardo.
#windowsdev #ai #microsoftstore #windows #appdev #msix #windev
Microsoft планирует обновлять через Windows Update все установленные приложения
Новая организованная платформа позволит разработчикам обновлять любые приложения напрямую из Windows Update.
https://tefida.com/microsoft-wants-windows-update-to-handle-all-apps/
#angiechen #appx #microsoft #msix #windowspacketmanager #windowsupdate #новостиit #tefidacom
Windows Update gestirà gli aggiornamenti di tutte le app
#Aggiornamenti #AppDiTerzeParti #Laptop #Microsoft #MSIX #Notizie #Novità #PC #SistemaOperativo #Software #Sviluppo #TechNews #Tecnologia #Update #Win32 #WindowsPackageManager #WindowsUpdate
https://www.ceotech.it/windows-update-gestira-gli-aggiornamenti-di-tutte-le-app/
Enhance your application security with administrator protection.
buff.ly/BY2bndy
#windows #security #msix #windows11 #windowsdev
Enhance your application secur...
Enhance your application security with administrator protection.
Автоматизация подписи кода в современных условиях
Подпись кода — это процесс проставления цифровой подписи на программном обеспечении. Цифровая подпись гарантирует пользователю, что программа является неподдельной и что её код не подвергся никаким изменениям в промежутке между созданием программы и выпуском. В старые времена для подписи билдов использовалась подписи GPG , а секретные ключи хранились где-нибудь на флэшке. Потом для приложений Windows появились система Authenticode . Сейчас для опенсорса и проприетарных ОС постепенно внедряются новые методы автоматизации подписи кода.
https://habr.com/ru/companies/globalsign/articles/904926/
#Mozilla #подпись_кода #Windows #Azure_Trusted_Signing #GitHub_Action #EVсертификат #GPG #Authenticode #signcode #Firefox_CI #Buildbot #Taskcluster #Autograph #Hardware_Security_Module #HSM #rcodesign #osslsigncode #MSIX #applecodesign #Apple_Code_Signing
10 reasons why application packaging isn't going anywhere.
https://buff.ly/4itaRPp
#windowsdev #msix #packaging #apps #msi #security #windows
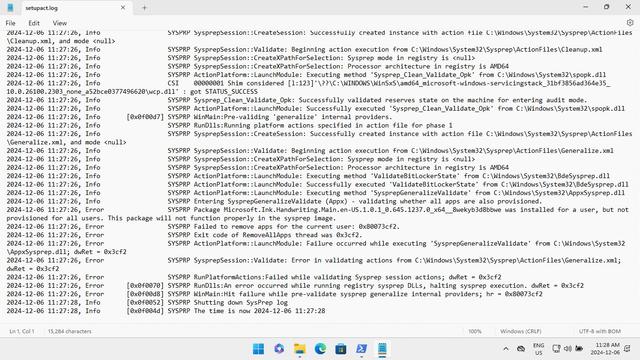
This is just ridiculous - if sysprep can fail validation because of those #MSIX packages, then Microsoft should just add a sysprep option to nuke all of them on sight. They break sysprep, and we need to remove them anyway to get a clean Windows image
Is there a #PowerShell one-liner that will nuke all the #MSIX per-user installations present in Windows 24H2 by default and that break sysprep? I just want to generalize my image and reset it back to OOBE
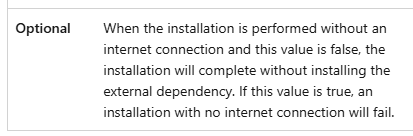
Can someone explain, why "Optional=true" should fail, and "Optional=false" not?
Create a Jenkins pipeline to deploy Desktop Apps as MSIX - Part 2: Packaging a Visual Studio solution.
#windowsdev #msix #dotnet #visualstudio #jenkins #deployment #windows
https://techcommunity.microsoft.com/t5/modern-work-app-consult-blog/create-a-jenkins-pipeline-to-deploy-desktop-apps-as-msix-part-2/ba-p/4157259
🥩🥩Mr T-Bone tip! Discover the latest updates in MSIX for May 2024! 🚀🌟 Check out the new features and enhancements now! 🙌📦
What is new in #MSIX Packaging Tool (v1.2024.405.0) for May 2024
https://www.elevenforum.com/t/what-is-new-in-msix-packaging-tool-v1-2024-405-0-for-may-2024.25423/
What is new in #MSIX for February 2024
https://www.elevenforum.com/t/what-is-new-in-msix-for-february-2024.22704/
#Microsoft nimmt erneut zum Schutz von Nutzern vor Trojanern eine einschneidende Änderung bei der #MSIX AppX-Installation vor. Dieses webbasierte App-Installationsprotokoll wird deaktiviert: https://winfuture.de/news,140364.html?utm_source=Mastodon&utm_medium=ManualStatus&utm_campaign=SocialMedia
"🚨 Windows App Installer Vulnerability: A New Twist in Cybersecurity 🚨"
Microsoft has temporarily disabled the MSIX ms-appinstaller protocol handler in Windows due to security concerns. This action was taken because malicious groups, like the Sangria Tempest group (also known as FIN7), were using it to distribute malware. This vulnerability, known as CVE-2021-43890, was exploited through phishing and malicious ads, often resulting in ransomware attacks. These attacks were able to bypass Defender SmartScreen and browser security warnings. Microsoft initially disabled this handler in February 2022 to counter Emotet attacks and has now decided to disable it again due to ongoing misuse by financially motivated threat groups.
The MSIX ms-appinstaller protocol handler is an important part of the MSIX package format. It simplifies the process of installing Windows applications directly from a URL, making it easier for developers and users. MSIX is a modern app package format for Windows that combines the best features of MSI, .appx, App-V, and ClickOnce installation technologies. Its main goal is to help developers package and distribute their applications efficiently and reliably, ensuring compatibility.
For more on CVE-2021-43890: Microsoft Advisory
For details on FIN7: MITRE - FIN7
Tags: #CyberSecurity #WindowsVulnerability #MSIX #ProtocolHandler #Malware #Ransomware #Phishing #ThreatIntelligence #SangriaTempest #FIN7 #MicrosoftSecurity
Sources:
- MSRC Blog: Microsoft addresses App Installer abuse
- BleepingComputer, Sergiu Gatlan: Microsoft disables MSIX protocol handler
MSIX, a Windows app package format, is a tool that developers can use to bundle, distribute, and install their applications for Windows users.
"👻 GHOSTPULSE: A New Evasion Technique in the Wild 🌐"
Elastic Security Labs has unveiled details of a new campaign named GHOSTPULSE. This campaign employs defense evasion capabilities to compromise victims using malicious MSIX executables. The stealthy loader, GHOSTPULSE, decrypts and injects its payload to dodge detection. MSIX, a Windows app package format, is being exploited by adversaries, especially those with above-average resources, as it requires access to code signing certificates. The campaign tricks users into downloading malicious MSIX packages, often masquerading as popular software installers like Chrome, Brave, and WebEx. Once executed, a covert PowerShell script activates GHOSTPULSE on the victim's system. 🚫🔍
The GHOSTPULSE loader operates in multiple stages, with the final payload typically being an information stealer. Notably, payloads like SectopRAT, Rhadamanthys, and Lumma have been observed. The malware also employs techniques like "module stomping" and "Process Doppelgänging" for its operations. 🕵️♂️💼
For those in the research community, Elastic Security has provided a configuration extractor to aid in further investigations of this campaign. 🛠️🔬
Source: Elastic Security Labs
Tags: #GHOSTPULSE #CyberSecurity #EvasionTechniques #MSIX #MalwareAnalysis #ElasticSecurityLabs
Authors: Salim Bitam, Joe Desimone. Twitter Reference