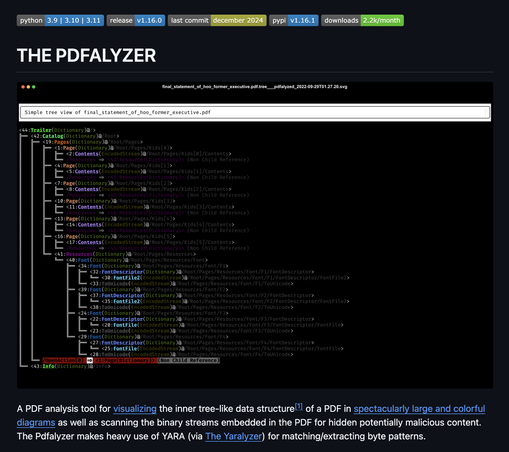
@evacide seeing as how it seems like the Paragon attack was executed via maldoc PDFs i'll just mention i created a (surprisingly popular) tool for analyzing (possibly malicious) PDFs after my own unpleasant encounter with such a creature
https://github.com/michelcrypt4d4mus/pdfalyzer
#paragon #infosec #Whatsapp #PDF #pdfalyzer #Malware #maldoc