Dự án tự động hóa CV + thư giới thiệu dựa trên URL việc làm từ LinkedIn. Hỗn hợp các công cụ như n8n, OpenAI, Supabase, Gotenberg để tạo PDF tự động. Quy trình gồm: thu thập thông tin việc làm, xử lý AI, kết hợp dữ liệu, chuyển đổi HTML>PDF và gửi kết quả. Thách thức: xử lý đa định dạng LinkedIn, luồng xử lý PDF và điều phối async. Độc giả có thể yêu cầu chia sẻ code hoặc mẫu prompt. #CôngNghệ #TựĐộngHóa #AI #LậpTrình #n8n #Supabase #Gotenberg #LinkedIn #CV #HướngĐếnAI
#supabase
Ứng dụng theo dõi công việc mới: Tải CV lên, chuyển thành dữ liệu cấu trúc, tạo thư xin việc & tin nhắn tự động thông minh. Hỗ trợ OCR ảnh/video ngay client, lưu trữ metadata để theo dõi dễ dàng. Thử miễn phí 3 credits khi đăng ký. Cần feedback từ mọi người! #CôngCụTuyểnDụng #AI #NextJS #TechViet #JobTracking #OCR #Supabase
https://www.reddit.com/r/SideProject/comments/1pj14p3/job_tracking_app/
🔍 #OpenScouts: Create #AI scouts that continuously search the web and notify you when they find what you're looking for #opensource #NextJS #React #TypeScript #Supabase #OpenAI #Firecrawl
⚡ Built with cutting-edge tech stack: #NextJS 16 with App Router & Turbopack, #React 19, #TypeScript, #TailwindCSS v4, #Supabase for database, auth & edge functions, #pgvector for vector embeddings and semantic search, #OpenAI API for AI agent & embeddings, and Resend for email notifications
🧵 👇
🔧 AI-powered features: automatic search query and strategy configuration, real-time updates via #Supabase Realtime subscriptions, AI-generated one-sentence summaries with semantic embeddings for each successful execution, manual "Run Now" button for immediate execution without waiting for cron
🔐 Authentication options: #Supabase Auth with email/password and #Google OAuth support, Row Level Security (RLS) policies ensure users only access their own scouts, messages, and executions
Cần ai giúp đỡ không? Mình đang gặp lỗi khi deploy trang web trên Vercel và muốn thiết lập Stripe, Supabase. Ai có kinh nghiệm chia sẻ mẹo để khắc phục lỗi và cấu hình đúng cách không? Chỉ cần chỉ dẫn để mình tự hiểu và điều chỉnh. Cảm ơn mọi người! #Vercel #Stripe #Supabase #LỗiKỹThuật #CầnHỗTrợ
https://www.reddit.com/r/SaaS/comments/1phu4fj/anyone_willing_to_help/
When using a backend-as-a-service like Supabase, you can only access the database through an HTTP API. Yet it is still possible to group queries into a transaction, without compromising on security. Read on to learn more. #database #security #NodeJS #supabase
https://marmelab.com/blog/2025/12/08/supabase-edge-function-transaction-rls.html
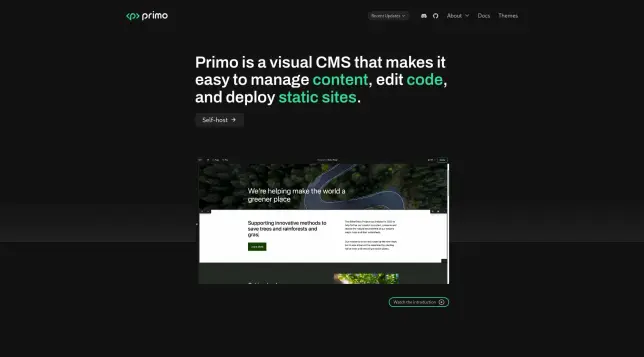
𝗣𝗿𝗶𝗺𝗼:
#Static #Github #Sveltekit #Supabase #PrimoCMS
https://thewhale.cc/posts/primo
Primo is a visual CMS that makes it a blast to build pages, manage content, and edit code - one block at a time.
Tìm forks Supabase tách Studio (UI quản lý PG) bị thiếu? Người dùng thử Poge nhưng không tương đồng Supabase Studio. Còn ý kiến nào? #Supabase #Poge #OpenSource #LậpTrình #NguồnMở
Self-hosted AI-платформа: полный стек для локального ИИ на Docker
Self-hosted AI-платформа на Docker: N8N, Ollama, Open WebUI, Qdrant, Whisper. Автоустановка, 152-ФЗ. Разбор архитектуры, benchmark топовых моделей декабря 2025 (DeepSeek-R1, Llama 3.3, Qwen 2.5), метрики на CPU/GPU, расчёт TCO.
https://habr.com/ru/articles/973456/
#ollama #dockercompose #open_source #supabase #postgresql #n8n #openwebui #redis #whisper #python3
Hướng dẫn tiết kiệm tiền khi phát triển ứng dụng di động đầu tiên:
1. V1 chỉ cần giải quyết 1 vấn đề cốt lõi & có 1 luồng người dùng chính.
2. Flutter là lựa chọn đa nền tảng hiệu quả, giảm chi phí & tăng tốc độ.
3. Backend nên dùng Firebase/Supabase cho MVP, tránh hệ thống phức tạp.
4. Ưu tiên tốc độ, lấy feedback nhanh, đừng cầu toàn.
#MobileApp #Startup #MVP #Flutter #Firebase #Supabase #TechTips #ỨngDụngDiĐộng #KhởiNghiệp #PhátTriểnỨngDụng #CôngNghệ
Một dev đã tạo tiện ích mở rộng Chrome để kiểm tra ứng dụng web tìm rò rỉ khóa API, đặc biệt là cấu hình Supabase DB và RLS bị lộ. Công cụ này tự động phát hiện lỗ hổng bảo mật và cho phép chia sẻ kết quả nhanh chóng, giúp các nhà phát triển dễ dàng sửa lỗi.
#DevTools #Security #WebSecurity #Supabase #APIKeys #ChromeExtension #BảoMật #CôngCụDev
I started setting up #Supabase for my project this weekend. I'm liking it so far, but MAN they don't make it easy to self-host, particularly the analytics module. Well, at least I got it done in the end, and now I have access to great admin tools for my project.
Dịch vụ SpeedMVP giúp xây dựng và triển khai MVP (Next.js + Supabase) chỉ trong 24-72 giờ! Các gói từ $119 (Landing Page) đến $699 (Full SaaS hoạt hình). Có 3 suất trống trong tuần này cho ai cần phát triển nhanh sản phẩm!
#MVP #SaaS #NextJS #Supabase #WebDevelopment #PhátTriểnPhầnMềm #Startup #WebDev #CôngNghệ
https://www.reddit.com/r/SaaS/comments/1paghlk/taking_3_speedmvp_slots_this_week_2472_hr_full/
Supabase hit $5B by turning down million-dollar contracts. Here’s why.
We have a great RSVP amount so far, but another quick reminder, we have a #Supabase meetup here in Berlin next week featuring our self-hosting lead speaking and others! And me serving you pizza :)
🛠️ Lỗi RLS trong Supabase khiến API key luôn trả “Invalid API key” vì không có session người dùng. Giải pháp: dùng service‑role key để xác thực API, tránh RLS, đồng bộ prefix và bỏ .single() khi query trả [] . Thêm logging để debug. #Supabase #RLS #API #SaaS #BảoMật #LậpTrình
https://www.reddit.com/r/SaaS/comments/1p6qxen/row_level_security_almost_broke_my_saas_api_heres/
So sánh chi phí hàng tháng: Vercel+Supabase vs AWS cho 2M yêu cầu/tháng.STACK 1: Vercel Pro + Supabase Pro. STACK 2: AWS Lambda + RDS PostgreSQL #Vercel #Supabase #AWS #ChiPhí #TínhToán #CloudComputing #ĐiệnToánĐámMây #SaaS #PhầnMềmLàmDịchVụ
https://www.reddit.com/r/SaaS/comments/1p5iqt9/need_help_calculating_monthly_costs/
Phát triển ứng dụng trò chuyện nhân vật tự lưu trữ và đồng bộ hóa đám mây. ng dụng này cho phép đồng bộ hóa cuộc trò chuyện và nhân vật trên các thiết bị, lưu trữ API key an toàn và hỗ trợ nhập dữ liệu từ Tavern PNG, Risu JSON và Character Card v3. #trò_chuyện_nhân_vật #đồng_bộ_hóa_đám_mây #tự_lưu_trữ #supabase #nextjs #AI #trợ_lý_tro_chuyen #cloud_sync #self_hosted #character_chat
Tuyển dụng Bolt.New @ SideProject: Ưu tiên ứng viên có kinh nghiệm GitHub, Vercel & Supabase.
#TuyểnDụng #BoltNew #GitHub #Vercel #Supabase
https://www.reddit.com/r/SideProject/comments/1p1zkvn/now_hiring/