Mongolia's IDN TLD, мон., just switched from the very old algorithm 5 (RSA-SHA1) to elliptic curves \o/
#DNSSec
Identity digital rolling keys after delegation change. There’s no going back now.
#dns #dnssec
https://mastodns.net/@diffroot/114700759330727364
#DNS #DNSSEC Le Gabon est désormais signé.
https://dnsviz.net/d/www.nic.ga/aFFxSw/dnssec/
And we're also looking for a Go dev!
also available in English:
Extended DNS Errors used in DNS software and services -- Modern, standardised function call for user applications still needed
https://www.sidn.nl/en/news-and-blogs/extended-dns-errors-used-in-dns-software-and-services
The Extended DNS Errors (EDE) introduced by RFC 8914 seem to be a useful addition to the DNS protocol.
However, there’s still a need for a new or extended function call to enable (stub) resolvers to relay EDE error codes to user applications that send them queries.
op SIDN.nl:
Extended DNS Errors vinden toepassing in DNS-software en -diensten -- Moderne, gestandaardiseerde functie-call voor gebruikersapplicaties ontbreekt nog
https://www.sidn.nl/nieuws-en-blogs/extended-dns-errors-vinden-toepassing-in-dns-software-en-diensten
De Extended DNS Errors (EDE) die RFC 8914 introduceerde blijken een belangrijke toevoeging aan het DNS-protocol.
Wat nog ontbreekt is een nieuwe of uitgebreide functie-call waarmee (stub) resolvers EDE-foutcodes aan hun aanroepende gebruikersapplicatie kunnen doorgeven.
I've noticed that in recent days the `LI` domain has crept up over 10% errors when querying signed domains. It's about 10.2% which is significantly higher than other Top Level Domains
It isnt in my top ten list so I don't publish the results on my report page. I have the data tho.
If you're associated with the TLD I'd love to hear if you have any thoughts on why.
https://kalfeher.com/analysis/cds-charts/#7-dns-connection-error-rate-per-tld
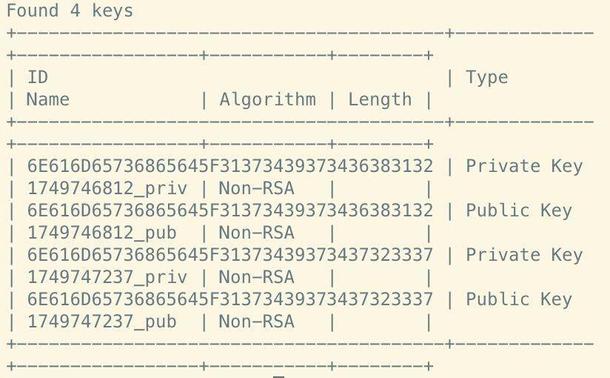
And yes, it works! Here are #DNSSEC keys in the YubiHSM, created via PKCS#11 using kmip2pkcs11 with KMIP queries sent by domain KMIP key code.
The goal for this approach is to shield an application against an untrusted PKCS#11 library.
Little Friday shout-out to @andreas for setting us up with a YubiHSM so we can test our KMIP and PKCS#11 code for our #DNSSEC signer Nameshed. 💚 Thanks a lot for supporting #OpenSource! #DNS #rustlang https://github.com/NLnetLabs/kmip2pkcs11
@jpmens We’d love to add more functionality to `dnst` by adding a drop-in replacement for `ldns-verify-zone` and include new functionality to make it comparable to validns, if desired.
As it stands, offering a prototype for Nameshed has our priority now, so that we can release a production grade #DNSSEC signer later in the year.
That being said, perhaps one of the developers needs to scratch an itch over the summer. 😉
#DNS #OpenSource #rustlang https://github.com/NLnetLabs/dnst
Philip explains Nameshed's #DNSSEC key management design at the ICANN83 DNSSEC And Security Workshop. Presentation starts at 58:32. #DNS #OpenSource #rustlang https://icann.zoom.us/rec/play/rZO4WQ43FXCBle-B2aMGbyuxoMqmt4-HU9PJVfjsZA4DYxv2k9X0IyhR8f0F_SSZwRbSgCIO3KxUtVuF.v4W-DaCIkkBU7JmJ?eagerLoadZvaPages=sidemenu.billing.plan_management&accessLevel=meeting&canPlayFromShare=true&from=share_recording_detail&startTime=1749475871000&componentName=rec-play&originRequestUrl=https%3A%2F%2Ficann.zoom.us%2Frec%2Fshare%2FnEPUGP0kRV04R3oQaAt0i2c_UQhxb2UHzg16VylkViD-EomNkaaPiiuSzWsWooUC.3ieFTG4o1XsG-TDW%3FstartTime%3D1749475871000
At the ICANN83 DNSSEC And Security Workshop, we presented the flexible key management we have designed for our new #DNSSEC signing solution Nameshed. Philip explains how we avoid loading an unknown shared library into the signer process and how we keep track of state. #DNS #OpenSource #rustlang Slides: https://static.sched.com/hosted_files/icann83/09/2.5%20Homburg%20-%20Flexible%20Key%20Management%20in%20Nameshed.pdf?_gl=1*36t2bs*_gcl_au*MjAzNDMxMTY4MS4xNzQ5NDc3NDU4
certbot on Debian Bookworm fails with: The peer didn't know the key we used
#LetsEncrypt #Debian #Challenge #Bookworm #Trixie #Certbot #Bind #RFC1918 #Encryption #DNSSEC #ACME #DNS
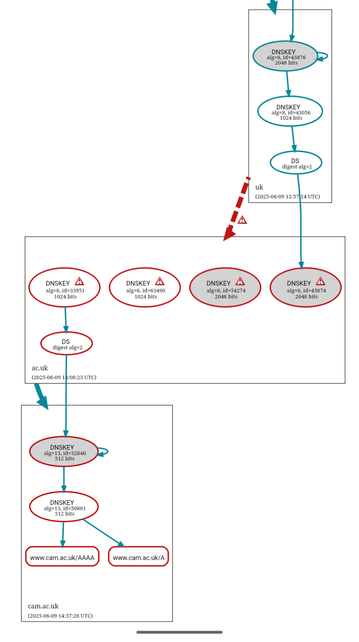
Anyone with more DNSSEC foo than me, is the delegation from `uk.` to `ac.uk.` broken right now?
@mnordhoff +1 IDK how @jerry does #DNSSEC. Personally I use #ClouDNS where this is a two-click operation...
there were zero changes to the root zone
https://mastodns.net/@diffroot/114638713618340487
looks like afilias/donuts/ident-dig taking on a portfolio from ultra/neustar/vercara/digicert
#dns #dnssec