MacでPowerShellやWindows運用の練習がしたい!無茶な要望にAWS で挑戦してみた その1
https://qiita.com/enough-e-o-rice/items/1d126f24c84903922d42?utm_campaign=popular_items&utm_medium=feed&utm_source=popular_items
#EC2
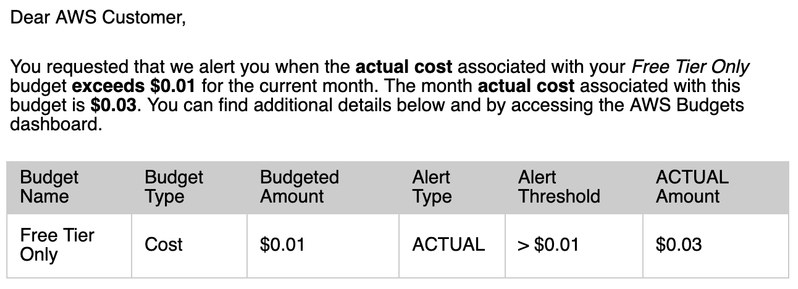
Oops. After I _did_ set up AWS budgets for my free-tier oriented accounts, I got sidetracked after only changing the credit_specification for the one that caused the problem in the first place.
Good to know those budget alerts work, I guess.
5-10m later and some tf validate/plan/apply runs later, and that's all sorted. 😅
Note to self - When running a free tier EC2 instance (in a fresh AWS account) you can still end up being charged for that thing if you're not careful, when you overload it and run out of CPU credits.
At that point, if your “credit specification" has “Unlimited mode" enabled (and that appears to be the default) it will end up costing you for additional CPU credits.
Disabling that with TF, in the aws_instance:
credit_specification {
cpu_credits = "standard"
}
🤞
From the digital archives: #AWS #EC2 IP ranges from 14 years ago.
Little bit smaller than today (https://ip-ranges.amazonaws.com/ip-ranges.json)
【実践記】プログラミングを始めて1年目 Vite+Go+AWSでブログ制作してみた。
https://qiita.com/run4learning/items/6e80e875ca2e01030884?utm_campaign=popular_items&utm_medium=feed&utm_source=popular_items
New AWS Developers podcast episode: Rick Ochs explains how AWS Compute Optimizer analyzes resource utilization to provide EC2, EBS, and Auto Scaling recommendations.
Listen in your podcast apps 🎧 or here 👉
https://developers.podcast.go-aws.com/web/episodes/162/index.html
Could your AWS cloud be secretly exposed? Hackers are exploiting SSRF to snag sensitive metadata, but upgrading to IMDSv2 might just turn the tables. Check out why tightening up this single layer could mean the difference between breach and safety.
https://thedefendopsdiaries.com/securing-aws-cloud-environments-against-ssrf-vulnerabilities/
#Development
EC2 reserved instances’ silent exit · The impact on Amazon Elastic Compute Cloud users https://ilo.im/16383s
_____
#Amazon #AWS #EC2 #Cloud #Pricing #Application #Website #Hosting #WebDev #Backend
A Beginner's Guide to Setting Up AWS Alarm Email Alerts using CloudWatch | https://techygeekshome.info/a-beginners-guide-to-setting-up-aws-alarm-email-alerts/?fsp_sid=16077 | #Amazon #AWS #Cloud #CloudWatch #EC2 #Guide #refresh
https://techygeekshome.info/a-beginners-guide-to-setting-up-aws-alarm-email-alerts/?fsp_sid=16077
A Beginner's Guide to Setting Up AWS Alarm Email Alerts using CloudWatch | https://techygeekshome.info/a-beginners-guide-to-setting-up-aws-alarm-email-alerts/?fsp_sid=16076 | #Amazon #AWS #Cloud #CloudWatch #EC2 #Guide #refresh
https://techygeekshome.info/a-beginners-guide-to-setting-up-aws-alarm-email-alerts/?fsp_sid=16076
Hosting Writebook on AWS
There are now several ways to read the short story I wrote earlier this year. You can of course always re-read the serialized "blog style" story on Substack. But, if you want a more traditional book style format, I have a couple options for you. You can buy the book on Amazon Kindle for $5.00. Or, if you are a KindleUnlimited subscriber, you can read it for free. Nice! I installed the very lovely Writebook software from 37Signals' ONCE on AWS, so you can read it there as well, for […]https://www.micahwalter.com/2025/03/hosting-writebook-on-aws/
I had to write an automation to rip through 106 Windows Server 2019 #EC2 instances today across 14 accounts in 14 regions. I had to grow all their EBS volumes and notify the OS to grow to the full disk size. And it ran and succeded the first time with 0 failures.
(a) #AWS Systems Manager is kind of amazing
(b) I should go buy a lottery ticket. Nothing that good ever happens when I do stuff like this.
Amazon has this leadership principle of "Learn and Be Curious" which is all about wanting to know things and enjoying learning new things. I have my own version of this called "Learn and Be Furious." Every once in a while I have to learn how something works, and once I get in there and figure it out, I'm shaking my fist at the screen asking "why did they DO it this way!?"
In #AWS EBS volumes are the virtual hard disks on EC2 instances, and EBS volumes can have snapshots. Snapshots are often used for backup/recovery and lots of other important uses, so there is a way to "lock" a snapshot. This prevents it being deleted accidentally. Yesterday I had to learn how to work with locked snapshots.
Here's what I learned.
The API
How do you lock a snapshot? There's an #EC2 modify-snapshot-attribute API, but "locked" is not a snapshot attribute. You can't lock it that way. Snapshot attributes are actually mainly permissions. It allows some folks to see, and thereby launch instances from, the snapshot. This is how, say, the Debian team or the FreeBSD team make an AMI that you can launch in EC2. They make an EC2 instance, make a snapshot of its EBS volume, set its snapshot public, and do some other things that make it available. So attributes aren't really "attributes" in some general sense: they're permissions.
If you want to lock a snapshot there's a lock-snapshot API. That's all it's good for: locking snapshots. If you want to unlock one, you guessed it: different API: unlock-snapshot.
This isn't exactly bad. Generally speaking, AWS APIs are service:verb-noun. So ec2:lock-snapshot fits the idiom and the common pattern. But by that logic, you'd expect ec2:share-snapshot and ec2:unshare-snapshot instead of ec2:modify-snapshot-attributes with user: all.
Why so furious?
I'm writing a janitor job that finds orphaned snapshots and deletes them. But if the snapshot is locked, trying to delete it throws an exception.
There are obviously 2 ways to do this: try it anyway and catch the exception when the snapshot is locked and deal with it. Or, I can figure out which snapshots are locked, and don't try to delete them in the first place.
I'm doing the latter, because I guess I want exceptions to be thrown only on failures. I don't want the janitor to run into something I did on purpose (locking a snapshot), and then figure it out down in the exception handler. I guess this is just what I think is the right way to do it, and maybe I'm wrong.
How do I find locked snapshots?
You'd think that you could call describe-snapshots, which takes certain Filters. There's a lot of possible things to filter on. I can get it to filter down to a certain set of snapshots based on a few criteria. Locked state is not one of them. In fact, the status of the lock is not returned in the information you get from describe-snapshots. If you wanted to know about locked snapshots, you should have called describe-locked-snapshots, which will return just those.
What about the list of unlocked snapshots?
If I have a list of snapshots (say, a list of orphans that should be deleted), but I want to figure out which ones are not locked, how do I do that?
First I get the list of all snapshots (or in my case, all orphaned snapshots). Then I get the list of all locked snapshots. Then I do the diff to remove locked snapshots from the list of all snapshots.
This feels like what my niece would call wonker bonkers. I dunno. Maybe my expectations are all wrong.
【ネットワーク系】EC2インスタンス構築時のデフォルト設定の"理由"を考えてみる
https://qiita.com/mob_engineer/items/d7c156fa93439b09a84d?utm_campaign=popular_items&utm_medium=feed&utm_source=popular_items
I'm working on an EC2 instance. SOMETHING is periodically modifying the routing table to add 169.254.169.253 (aka, the Route53 resolver endpoint) to point to the wrong place, which, naturally, makes everything on the box fall over.
If I delete the offending route, everything starts working again, but then some 15 minutes later it gets added back. I checked all the obvious candidates (cron, systemd, etc) that I could think of and can't figure out what is adding this route. Anybody know of any way to audit routing table changes so that I can stop this from happening anymore?
(this is incidentally a kubernetes node but I don't feel like that should matter???? Idkwtf though)