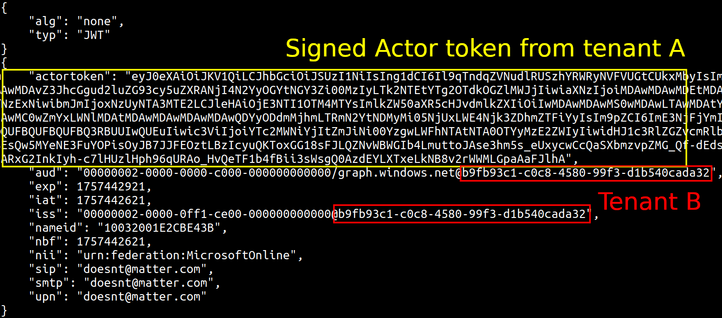
🔍 Detection Method
===================
🔍 OSINT
Executive summary: Public-facing identity services such as Entra ID
(Azure AD) are at risk from non-credential enumeration techniques that
combine OSINT with identity-focused tooling. References to
AADInternals and email-harvesting workflows indicate a threat model
where reconnaissance informs credential-based attempts rather than
zero-day exploitation.
Technical details:
• Tools and techniques mentioned include AADInternals for Entra
enumeration and common OSINT sources (LinkedIn, Hunter.io) for
collecting potential usernames and emails.
• Attacks described focus on credential-driven vectors: password
spraying and targeted authentication attempts that probe MFA and
Conditional Access responses.
Analysis:
• The core risk arises from visibility: externally discoverable
identities and role metadata enable focused attacks that bypass noisy
scanning. Entra/AD telemetry can be used to detect reconnaissance if
logs are instrumented.
• The presence of Conditional Access and MFA changes the attacker
tradeoffs: failures and policy evaluation events become important
detection signals.
Detection guidance:
• Surface and aggregate failed sign-in patterns across tenants; alert
on unusual volumes of password-spray–style failures targeting many
accounts in short windows.
• Monitor Conditional Access evaluation logs for repeated policy
decisions from anomalous IPs or device states.
• Correlate OSINT-derived lists with authentication telemetry to spot
targeted attempts.
Mitigation:
• Enforce MFA for all privileged and high-risk accounts and reduce
legacy authentication allowances.
• Harden user discovery: limit public exposure of role-based emails
and group memberships where possible.
• Implement rate-limiting and suspicious-activity thresholds in
identity platforms and enrich logs with UEBA for context.
Limitations:
• Public reporting does not supply IoCs or exploitation artifacts;
analysis is high-level and defensive.
🔹 AzureAD #Entra #AADInternals #OSINT #MFA
🔗 Source: https://dmcxblue.net/2025/08/23/how-to-rob-a-hotel/