#Landlock
Updated #sydbox to 3.35.0: hardened #Landlock, empty mount namespaces using pivot_root and root:tmpfs a la #bubblewrap, many bug fixes thx to LTP, many bug/portability fixes thx to #alpine #linux folks. New utilities #syd-fd and #syd-x. See the release mail for more information: https://is.gd/syd_3_35_0 #exherbo #hacking #security
News from #sydbox #git: #Landlock compatibility levels are now supported with the "default/lock" option. Default compat level has been changed from "best-effort" to "hard-requirement" to adhere to the principle of secure defaults. Our standalone #Landlock utility syd-lock learned "-C" option to interface with compat levels. ENOENT, aka "No such file or directory" errors during sandbox setup are now fatal unless compat level has been set to "best-effort". #linux #security https://man.exherbo.org/syd-lock.1.html
I'm now wondering if I should compile it with this, and what security it adds additionally to a systemd service file with all the restrictions about the filesystem and syscalls one can do.
Do I need to configure anything with landlock to "activate" it when I compile it in? I didn't yet find the right documentation that I can understand for it it seems.
Does snac somehow "know" what to landlock and which paths to allow before landlocking itself, maybe reading my config file before that happens?
#snac #snac2 (never know which tag to use here :) ) #landlock #linux #kernel #security #selfhosting
News from #sydbox: when you configure syd-tor to use a #UNIX domain socket for external #TOR connections which is a new feature it will open an O_PATH fd to the socket, enter into a network+mount+user+... namespace, chroot into /proc/self/fd and access the unix socket using the fd number. This means it will work even if you remove the socket. The socket is duplicated to a random fd to make fd reuse harder. We also apply mdwe, #seccomp and #landlock on top, read more here: https://man.exherbo.org/syd-tor.1.html#SECURITY
I just published the fifth #Landlock newsletter! 🤓
- new kernel features: IPC scoping and audit logs
- kernel fixes
- library and talk updates
- new doc
- new open source Landlock users
- RHEL support
https://lore.kernel.org/landlock/20250519.ceihohf6a3uT@digikod.net/
#sydbox-3.33.0 is released, This work continues the sandbox category rework: "rmdir" category is now split from the "delete" category and the #landlock categories have been refined to be more #openbsd #pledge like. The tool syd-lock also got a rework so landlock categories may be used with that too while the old, easyinterface is still available so your scripts will not break! See the release announcement for more information: https://is.gd/eVxsBt #exherbo
I released a new version of the #Landlock crate: https://github.com/landlock-lsm/rust-landlock/blob/HEAD/CHANGELOG.md#v042
We can now easily restrict signal sending and connections to abstract UNIX sockets for #rustlang programs. The documentation and tests have also been improved. Last but not least, a few new features will be useful for the upcoming Landlock configuration format.
Landrun sperrt Prozesse performant mit Landlock ein - LinuxCommunity
However, you must enable it at boot. If you're using #GRUB, follow these steps:
1. Add the following line to /etc/default/grub:
GRUB_CMDLINE_LINUX_DEFAULT="lsm=landlock"
2. Regenerate the GRUB configuration:
geninitrd
3. Reboot your system and verify that Landlock is enabled:
sudo dmesg | grep landlock
Example output:
[ 0.000000] Command line: BOOT_IMAGE=/boot/vmlinuz-generic root=UUID=... ro lsm=landlock
[ 0.068388] Kernel command line: BOOT_IMAGE=/boot/vmlinuz-generic root=UUID=... ro lsm=landlock
[ 0.212270] LSM: initializing lsm=capability,landlock
[ 0.212270] landlock: Up and running.
Once enabled, you can use landrun on Slackware-current:
https://slackbuilds.org/repository/15.0/network/landrun/
The Landrun tool is now available in SlackBuildsOrg!
Landrun A lightweight, secure sandbox for running Linux processes using Landlock.
Think firejail, but with kernel-level security and minimal overhead.
Get it here:
https://slackbuilds.org/repository/15.0/network/landrun/
#Linux #Slackware #landlock #OpenSource #landrun
My website is a product of it: https://shtrophic.net
See: https://git.sr.ht/~shtrophic/gmlghd
Another LSM we don't talk enough about
https://github.com/Zouuup/landrun
The landlock LSM isn't frequently spoken about, it's Linux equivalent of OpenBSD unveil. See also "Following landlock development" in 204, "Landlock" in 161 among others. Or what I've written about it.(https://venam.net/blog/unix/2023/02/28/access_control.html#landlock--seccomp)
Love Linux/Unix? Subscribe to the Nixers Newsletter: https://newsletter.nixers.net/entries.php !
#landlock #landrun #linux #openbsd
🌘 在安全的、非特權沙盒中運行任何 Linux 進程,使用 Landlock LSM。<br>
➤ Landlock LSM 提供安全的 Linux 沙盒環境。<br>
✤ https://github.com/Zouuup/landrun
這篇文章介紹了針對 Linux 進程運行的 Landlock LSM 安全沙盒,類似 firejail,但更輕巧、用戶友好並融入內核。<br>
+ 這篇文章提供了清晰的說明,讓人對 Landlock LSM 的安全功能有更深入的瞭解。<br>
+ 使用 Landlock LSM 在 Linux 上運行進程看起來是一個很有前景的方向,希望以後能看到更多相關的應用場景。
#Linux安全 #沙盒環境 #Landlock LSM<br>
Landrun: Sandbox any Linux process using Landlock, no root or containers
https://github.com/Zouuup/landrun
#HackerNews #Landrun #Sandbox #Linux #Landlock #NoRoot #Containers
Regarding latest #landlock #cve which is still under analysis, #sydbox prevents unknown files (and files referring to block devices) from being listed and opened, see https://gitlab.exherbo.org/sydbox/sydbox/-/blob/main/src/hook.rs?ref_type=heads#L12380 and https://gitlab.exherbo.org/sydbox/sydbox/-/blob/main/src/path.rs?ref_type=heads#L349, the #cve is here, https://nvd.nist.gov/vuln/detail/CVE-2025-21830 So far the only false positive we had is pipewire passing files of unknown types thru unix sockets so we relaxed that but we still do disallow passing dirfds like #openbsd and add to that symlinkfds and blockdevfds #exherbo #security
The core idea behind #sydbox + #landlock and #openbsd's #pledge + #unveil is quite similar. In #sydbox, syscall emulator processes are confined with the same #landlock sandbox as the sandbox process, therefore it allows for building a multi-layered sandbox that complements the main seccomp-{bpf,notify} sandbox. This is the core reason why the #landlock break CVE-2024-42318 does not work under #sydbox. #exherbo #security
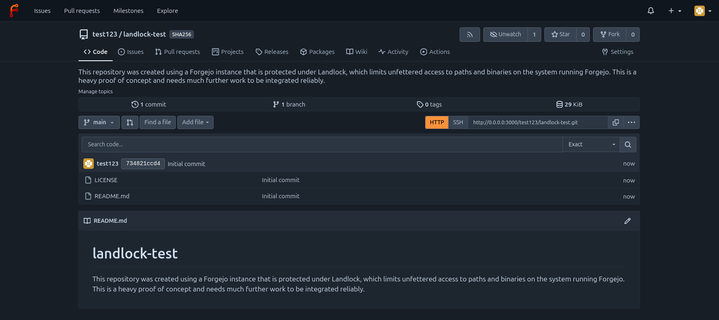
I'd like to share something nice that I am currently working on: A Landlock integration for Forgejo.
Landlock (https://landlock.io) lets userspace processes tell the kernel "hey kernel, please only let me access the following filesystem resources" (and it also supports sockets, etc. now).
My integration only limits unfettered access to arbitrary files. It needs a lot more yak shaving (refactoring, configurations, using the PATH variable for Git binaries) and time.
When tracing syscalls and setting
CURLOPT_VERBOSE, no failed syscalls show up on any network request... Also, curl is compiled with c-ares on alpine, but that still should only require /etc/resolv.conf and /etc/hosts.Not sure where to continue debugging...