Как подружить DynamoRIO и LibFuzzer
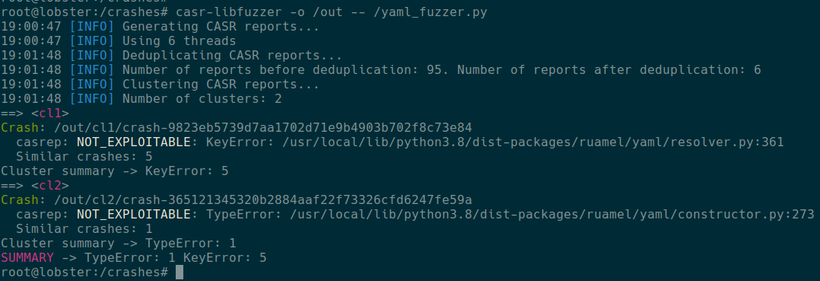
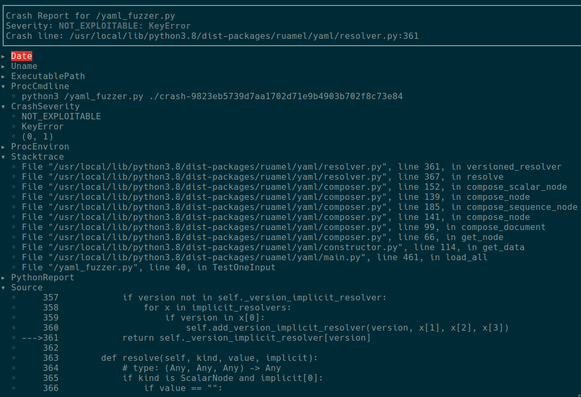
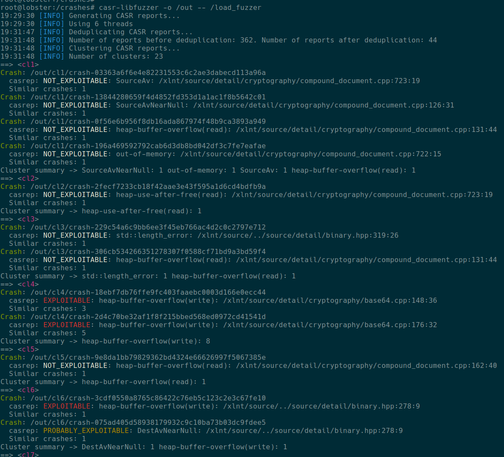
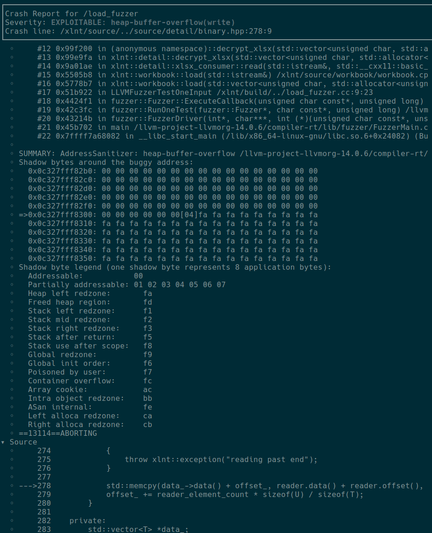
Приветствую всех обитателей Хабра и случайных гостей! Этой статьёй я хотел бы начать цикл заметок, посвящённых моей научной работе в вузе, связанной с фаззинг-тестированием. Всего на данный момент я работаю над темой 2 семестра. За это время мне много раз приходилось обращаться к интернет ресурсам в поисках информации по работе с DynamoRIO. Но, к сожалению, годных ресурсов попадалось крайне мало. Поэтому я решил облегчить судьбу другим, интересующимся этой темой и инструментарием, и состряпал данную статью. Надеюсь, кому-нибудь это да пригодится ;-)
https://habr.com/ru/articles/826932/
#фаззинг #фаззингтестирование #dynamorio #libfuzzer #ассемблер #динамический_анализ #динамическая_инструментация #динамический_анализ_кода #криптография #инструментация