No PE header? No problem.
@FortiGuardLabs dropped a deep dive into a malware sample dumped without a PE header — like a cybercriminal rage-quit halfway through packing their payload.
You ever load a binary in IDA and think, “Am I being punk’d?”
Yeah, it’s one of those samples.
This sample:
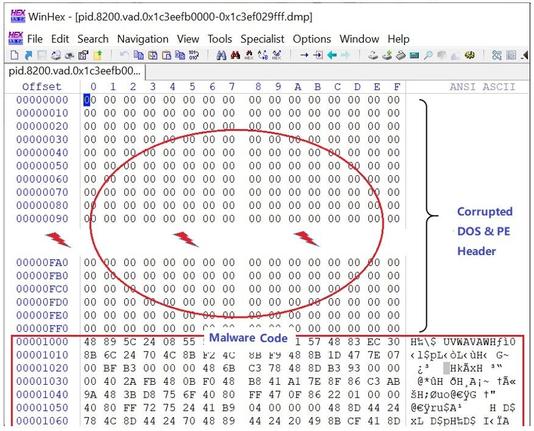
Reconstructs its own PE structure at runtime
Hides config data in obfuscated blobs
Uses anti-sandbox tricks to avoid analysis
Drops yet another info-stealer, because originality is dead
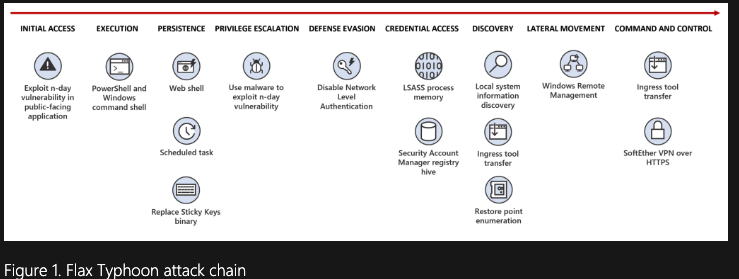
It’s engineered to break basic static analysis and dodge sandboxes like it’s speedrunning DEFCON CTF.
🔗 Full breakdown:
https://www.fortinet.com/blog/threat-research/deep-dive-into-a-dumped-malware-without-a-pe-header
TL;DR for blue teamers:
Static AV signatures won’t help here
Watch for suspicious memory allocations + hollowing patterns
Endpoint heuristics > file-based detection
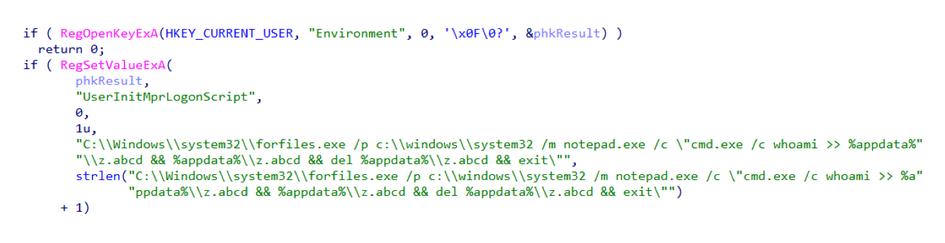
Log your PowerShell and LOLBins — this thing probably brings friends
If your EDR cries when it sees raw shellcode, maybe give it a hug
#ThreatIntel #MalwareAnalysis #ReverseEngineering #Infosec #PEFilesAreSo2020 #EDREvasion #LOLbins #CyberSecurity #BlueTeam