Discover the Shocking Truth About Ethical Hackers (And How They’re Saving You Every Day!)
1,115 words, 6 minutes read time.
You’ve probably heard the term “ethical hacker” thrown around in tech forums or news reports after a major data breach. But what if I told you that these so-called “white hat” hackers are the unsung heroes keeping your digital life safe—often without you even realizing it? In a world increasingly shaped by cybercrime, ethical hacking has emerged not just as a career path but as a frontline defense against the kind of digital threats that can ruin lives overnight.
Before we dive into how ethical hackers work their magic, let’s clear up what the term actually means. Ethical hacking is the process of legally breaking into computers and devices to test an organization’s defenses. Think of them as the cybersecurity world’s stunt drivers—they perform high-risk maneuvers so others don’t crash and burn. According to the EC-Council, “Ethical hackers aim to investigate the system or network for weak points that malicious hackers can exploit or destroy.”
Unlike their black hat counterparts—the bad guys—ethical hackers operate under strict legal and moral codes. Their goal isn’t to steal or destroy, but to protect and strengthen. As cybersecurity threats evolve, companies hire these specialists to simulate real-world attacks and uncover vulnerabilities before the criminals do. The stakes are high: one unpatched hole in a company’s firewall could expose millions of records, costing billions in damages.
To understand the role of ethical hacking in bolstering cybersecurity, it’s crucial to recognize the different types of hackers. Black hats are the criminals—those exploiting systems for personal gain or chaos. Gray hats walk the line, sometimes hacking without permission but often with noble intent. White hats, or ethical hackers, are the defenders. They work within the boundaries of the law to test and secure systems, often holding certifications like CEH (Certified Ethical Hacker).
One often overlooked aspect of ethical hacking is how it fosters trust. In the digital economy, trust is currency. When a company invests in ethical hacking, it sends a clear message to its users: your data matters. This isn’t just good PR—it’s smart business. Ethical hackers find the flaws before the attackers do, creating a digital moat that can mean the difference between success and scandal.
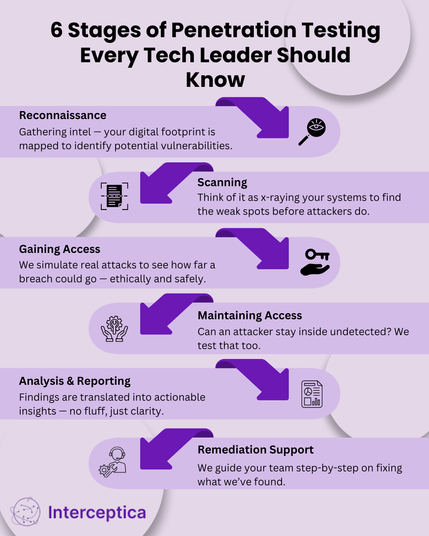
Penetration testing is one of the most common techniques ethical hackers use. This involves simulating a cyberattack to see how the system holds up. If you’ve ever seen a hacker movie where someone plugs a laptop into a server and types furiously—yeah, it’s kind of like that, minus the dramatic music. Real-life pen testers use sophisticated tools and scripts to probe for weaknesses, often spending weeks documenting every potential exploit.
Another method is vulnerability assessment. This doesn’t go as deep as penetration testing but scans systems for known vulnerabilities. It’s like a security check-up. These scans can be automated and run regularly to ensure no known exploits go unpatched. And increasingly, ethical hackers are leveraging AI and automation tools to accelerate these tasks, spotting patterns and threats that humans might miss.
The career path of an ethical hacker is as challenging as it is rewarding. It’s not just about technical know-how—you also need an unshakable moral compass and a commitment to learning. The digital landscape is constantly shifting, and what works today might be obsolete tomorrow. Resources like Cybersecurity Guide and Cisco’s Networking Academy offer beginner-friendly pathways into this complex field.
Certifications matter. Employers often look for credentials such as CEH, OSCP (Offensive Security Certified Professional), and CompTIA Security+. These not only validate your skills but prove your commitment to operating within ethical boundaries. According to NetCom Learning, “Ethical hackers must follow a well-documented process and respect client confidentiality at all times.”
Educating yourself in cybersecurity isn’t just for IT professionals—it’s becoming essential for everyone. Online platforms like Udemy offer courses that teach the basics of ethical hacking, even if you don’t have a technical background. Communities like Reddit’s /r/netsec or local cybersecurity meetups also provide opportunities to learn from real practitioners.
And let’s be real—cyber threats aren’t just something you read about. They can hit close to home. Whether it’s your email getting hacked or your bank account compromised, the consequences can be devastating. That’s why knowing how to protect your digital self is more crucial than ever.
Start with the basics. Secure your devices with strong, unique passwords and enable two-factor authentication wherever possible. Stay skeptical of suspicious emails, especially those asking for personal information or prompting you to click unknown links. And always, always keep your software up to date. It’s the digital equivalent of locking your front door.
Backing up your data is another underrated move. Ransomware attacks are on the rise, and having an offline backup could save you from losing everything. As Chubb Insurance puts it, “It’s not a matter of if, but when you’ll be targeted.”
The evolution of ethical hacking reflects the broader shift in how we approach cybersecurity. No longer an afterthought, it’s now a core component of any robust security strategy. As Stay Safe Online explains, “Ethical hacking has grown from a niche interest into a professional discipline critical to protecting modern infrastructure.”
In conclusion, ethical hacking plays a vital role in modern cybersecurity. These digital sentinels work tirelessly to find vulnerabilities before the criminals do, using their skills for good in an ever-changing threat landscape. If you’re interested in learning more or getting involved, there’s never been a better time to start. Join a community, take a course, or even consider pursuing a career in ethical hacking.
Don’t forget to subscribe to our newsletter for the latest in cybercrime news, ethical hacking tips, and expert insights. Got thoughts or questions? Drop a comment below—we’d love to hear from you and keep the conversation going!
D. Bryan King
Sources
Disclaimer:
The views and opinions expressed in this post are solely those of the author. The information provided is based on personal research, experience, and understanding of the subject matter at the time of writing. Readers should consult relevant experts or authorities for specific guidance related to their unique situations.
Related Posts
#AIInCybersecurity #CEHCertification #cyberDefenseTechniques #cyberThreatDefense #cybercrime #cybersecurity #cybersecurityBestPractices #cybersecurityEducation #cybersecurityForBeginners #cybersecurityInsights #cybersecurityTools #dataBreachPrevention #digitalSecurity #digitalVulnerability #ethicalHackerCertification #ethicalHackerFacts #ethicalHackerResponsibilities #ethicalHackerRole #ethicalHackerTools #ethicalHackerTraining #ethicalHackersVsBlackHat #ethicalHacking #ethicalHackingCareer #ethicalHackingCourses #ethicalHackingGuide #ethicalHackingImpact #ethicalHackingImportance #ethicalHackingMeaning #hackerEthics #hackerLifestyle #hackerSimulation #hackerTypes #hackingAndSecurity #hackingPrevention #hackingRiskReduction #hackingThreats #howToBecomeAnEthicalHacker #internetSafety #learnEthicalHacking #onlineHackingProtection #OnlineSecurity #PenetrationTesting #phishingAwareness #preventHackingAttacks #protectOnlinePrivacy #realEthicalHackers #safeBrowsing #secureOnlineBehavior #secureYourData #secureYourDevices #softwareUpdatesSecurity #vulnerabilityAssessment #whatIsEthicalHacking #whiteHatCyberExperts #whiteHatHacker