The Most Overlooked Bug Bounty Misconfiguration (Add This To Your Checklist)
This article describes a critical 2FA (Two-Factor Authentication) misconfiguration vulnerability that allows attackers to disable user accounts and gain unauthorized access. The vulnerability exploits improper input validation in 2FA systems where blank or empty verification codes are accepted, bypassing the authentication requirement. The exploitation involves intercepting the 2FA verification request with tools like Burp Suite and modifying the code parameter to be blank or empty before sending the request. While many developers have patched this specific issue, it still exists in some implementations, particularly in custom or poorly implemented 2FA systems. The attack vector allows attackers to disable legitimate users' two-factor authentication protection, effectively neutralizing the security layer. The impact ranges from complete account takeover to denial of service by preventing legitimate users from accessing their own accounts. This vulnerability represents a significant security gap as it undermines the entire purpose of 2FA protection. The attack requires minimal technical skill but can be highly effective against vulnerable targets. Organizations should implement proper input validation that rejects empty or malformed 2FA codes, ensure blank parameters are treated as invalid, and implement additional verification layers beyond simple code presence validation. The technique is particularly dangerous because it can affect any user with 2FA enabled, creating a wide attack surface. This misconfiguration highlights the importance of thorough security testing of authentication mechanisms, especially secondary authentication layers like 2FA. #infosec #BugBounty #Cybersecurity #2FA #AccountTakeover #AuthBypass
https://medium.com/activated-thinker/the-most-overlooked-bug-bounty-misconfiguration-add-this-to-your-checklist-448cce763beb?source=rss------bug_bounty-5
#accounttakeover
University of Pennsylvania probes mass email breach #Phishing #AccountTakeover #MailingListAbuse #Penn #UPenn #Pennsylvania #UniversityOfPennsylvania #PennGSE https://dysruptionhub.com/upenn-mass-email-breach-pa/
With the goal of better understanding cloud account takeover (ATO) attacks, our threat researchers developed a tool that automates the creation of malicious internal applications within a compromised cloud environment.
This blog post provides an in-depth technical analysis of that tool and its implications for enterprise security.
🚨 Account takeovers are growing fast—are you prepared?
Join Fastly’s live session: How to protect against account takeover attacks and other emerging cyber threats
What you’ll learn:
✅ Stop account takeover attacks
✅ Detect and mitigate bot traffic
✅ Automate smarter defenses
🎁 Free Web App Security Assessment available to all attendees!
📅 Save your spot now → https://learn.fastly.com/security-how-to-series
#CyberSecurity #AccountTakeover #Fastly
Masz wystawioną do Internetu Grafanę? Lepiej do niej zerknij… możliwe przejęcie konta
Grafana to otwartoźródłowa platforma do analizy i prezentacji danych, szeroko stosowana nie tylko w IT. Pozwala tworzyć panele prezentujące różne metryki, co powoduje, że jest popularnym rozwiązaniem wśród inżynierów IT i adminstratorów. Użytkownikom “domowym” może być znana między innymi z paneli prezentujących informacje udostępniane przez urządzenia klasy smart home (np....
#WBiegu #AccountTakeover #Grafana #Js #Openredirect #Websec #XSS
Urgent: 80,000+ Microsoft Entra ID accounts targeted in active takeover campaign. #MicrosoftSecurity #Cybersecurity #AccountTakeover
More details: https://www.helpnetsecurity.com/2025/06/12/researchers-warn-of-ongoing-entra-id-account-takeover-campaign - https://www.flagthis.com/news/16683
Proofpoint cloud threat researchers have recently uncovered an account takeover (ATO) campaign weaponizing TeamFiltration, a pentesting framework designed to assist cybersecurity practitioners in testing and improving defense solutions.
Attackers leverage Microsoft Teams API and globally distributed Amazon Web Services (AWS) servers for greater speed and efficiency, allowing for automating the tedious work of user enumeration and password spraying for both efficacy and stealth.
So far, over 80,000 user accounts across roughly 100 cloud tenants have been targeted.
Read the full campaign analysis here: https://brnw.ch/21wTk3G
#ATO #accounttakeover #MicrosoftTeams #OneDrive #Outlook #AWS #cyber
When Strong Passwords Fail: Lessons from a Silent, Persistent Attack
1,038 words, 5 minutes read time.
Pro Git 2nd Edition, Kindle EditionAffiliate Link
Today’s affiliate link features Pro Git, 2nd Edition — available for free at the time of this post. Be sure to grab your copy before the offer ends!
As an IT professional, I pride myself on maintaining robust security practices. I use unique, complex passwords, enable two-factor authentication (2FA), and regularly monitor my accounts. Despite these precautions, I recently experienced a security breach that served as a stark reminder: even the most diligent efforts can fall short if certain vulnerabilities are overlooked.
The Unexpected Breach
I maintain a Microsoft 365 Developer account primarily for SharePoint development. This account isn’t part of my daily workflow; it’s used sporadically for testing and development purposes. To secure it, I employed a 36-character random password—a combination of letters, numbers, and symbols. This password was unique to the account and stored securely.
Despite these measures, I received a notification early one morning indicating a successful login attempt from an unfamiliar location. Fortunately, 2FA was enabled, and the unauthorized user couldn’t proceed without the second authentication factor. This incident prompted an immediate investigation into how such a breach could occur despite stringent password security.
The Silent Persistence of Attackers
Upon reviewing the account’s activity logs, I discovered a disturbing pattern: months of failed login attempts originating from various IP addresses. These attempts were methodical and spread out over time, likely to avoid triggering security alerts or lockouts. This tactic, known as a “low and slow” brute-force attack, is designed to fly under the radar of standard security monitoring systems.
Such persistent attacks underscore the importance of not only having strong passwords but also implementing additional security measures. According to the Cybersecurity and Infrastructure Security Agency (CISA), 2FA is essential to web security because it immediately neutralizes the risks associated with compromised passwords. If a password is hacked, guessed, or even phished, that’s no longer enough to give an intruder access: without approval at the second factor, a password alone is useless .
The Vulnerability of Dormant Accounts
One critical oversight on my part was the assumption that an infrequently used account posed less of a security risk. In reality, dormant accounts can be prime targets for attackers. These accounts often retain access privileges but are not actively monitored, making them susceptible to unauthorized access. As noted by security experts, dormant accounts often fly under the radar, making them perfect targets for threat actors. Since they aren’t actively monitored, cybercriminals can exploit them for weeks—or even months—before being detected .
This realization led me to reassess the security of all my accounts, especially those not regularly used. It’s imperative to treat every account with the same level of scrutiny and protection, regardless of its frequency of use.
Immediate Actions Taken
In response to the breach, I took several immediate steps to secure the compromised account and prevent future incidents:
First, I changed the account’s password to a new, equally complex and unique one. Recognizing that the email address associated with the account might have been targeted, I updated it to a more obscure variation, reducing the likelihood of automated credential stuffing attacks.
Next, I thoroughly reviewed the account’s security settings, ensuring that all recovery options were up-to-date and secure. I also examined the activity logs for any other suspicious behavior and reported the incident to Microsoft for further analysis.
Finally, I conducted a comprehensive audit of all my accounts, focusing on those that were dormant or infrequently used. I enabled 2FA on every account that supported it and closed any accounts that were no longer necessary.
Lessons Learned
This experience reinforced several critical lessons about cybersecurity:
Firstly, password strength alone is insufficient. While complex passwords are a fundamental aspect of security, they must be complemented by additional measures like 2FA. According to research, implementing 2FA can prevent up to 99.9% of account compromise attacks .
Secondly, dormant accounts are not inherently safe. Their inactivity can lead to complacency, making them attractive targets for attackers. Regular audits and monitoring of all accounts, regardless of usage frequency, are essential.
Thirdly, attackers are persistent and patient. The “low and slow” approach to brute-force attacks demonstrates a strategic method to bypass traditional security measures. Staying vigilant and proactive in monitoring account activity is crucial.
Strengthening Security Measures
In light of this incident, I have adopted several practices to enhance my cybersecurity posture:
I now regularly audit all my accounts, paying special attention to those that are dormant or infrequently used. I ensure that 2FA is enabled wherever possible and that all recovery options are secure and up-to-date.
Additionally, I have started using a reputable password manager to generate and store complex, unique passwords for each account. This tool simplifies the process of maintaining strong passwords without the need to remember each one individually.
Furthermore, I stay informed about the latest cybersecurity threats and best practices by subscribing to security newsletters and participating in professional forums. This continuous learning approach helps me adapt to the evolving threat landscape.
Conclusion
This incident served as a sobering reminder that no one is immune to cyber threats, regardless of their expertise or precautions. It highlighted the importance of a comprehensive security strategy that includes strong passwords, multi-factor authentication, regular account audits, and continuous education.
I encourage everyone to take a proactive approach to cybersecurity. Regularly review your accounts, enable 2FA, use a password manager, and stay informed about emerging threats. Remember, security is not a one-time setup but an ongoing process.
If you found this account insightful, consider subscribing to our newsletter for more cybersecurity tips and updates. Share your thoughts or experiences in the comments below—we can all learn from each other’s stories.
D. Bryan King
Sources
- CISA – Multi-Factor Authentication (MFA)
- arXiv – Understanding Multi-Factor Authentication Efficacy
- Microsoft – Why MFA Is a Must
- NCSC – Password Guidance: Simplifying Your Approach
- Tekie Geek – The Danger of Dormant Accounts
- OWASP – Authentication Cheat Sheet
- Bruce Schneier – Low and Slow Brute-Force Attacks
- Have I Been Pwned – Check if Your Email Was Compromised
- Australian Cyber Security Centre – Securing Your Accounts
- NIST – Updated Guidance on Digital Identity
- Kaspersky – Password Security Tips
- 1Password Blog – The Importance of MFA
Disclaimer:
The views and opinions expressed in this post are solely those of the author. The information provided is based on personal research, experience, and understanding of the subject matter at the time of writing. Readers should consult relevant experts or authorities for specific guidance related to their unique situations.
Related Posts
#2FA #accountHacking #accountMonitoring #accountTakeover #bruteForceAttack #cloudAccountProtection #cloudSecurity #compromisedAccount #compromisedCredentials #compromisedMicrosoftAccount #credentialStuffing #credentialTheft #cyberattack #cybercrime #cybersecurity #cybersecurityAwareness #cybersecurityLessons #developerAccountSecurity #dormantAccounts #emailSecurity #hackerPrevention #howHackersBypassMFA #identityProtection #infosec #ITProfessionals #ITSecurity #ITSecurityIncident #loginSecurity #lowAndSlowAttack #MFA #MFAImportance #Microsoft365Security #MicrosoftLogin #passwordAloneNotEnough #passwordBreach #passwordEntropy #passwordHygiene #passwordManagement #PasswordSecurity #passwordVulnerability #persistentThreats #phishingProtection #randomHashPassword #realWorldBreach #realWorldCybersecurity #securePasswords #securingDormantAccounts #securityAudit #securityBestPractices #securityBreach #SharePointDeveloperAccount #SharePointSecurity #strongPasswords #techSecurityBreach #tokenHijacking #TwoFactorAuthentication
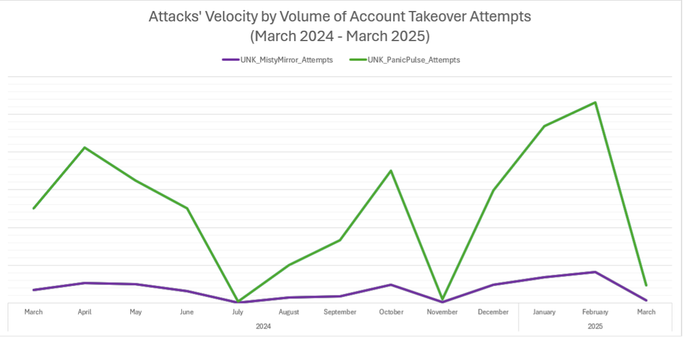
Proofpoint researchers have identified two active #accounttakeover (#ATO) campaigns, tracked as UNK_PanicPulse & UNK_MistyMirror, targeting #Microsoft365 accounts.
Since March 2024, both clusters have affected 6K+ accounts across 1.4K+ organizations, using botnets & unique client agents.
Our threat analysts have found strong similarities between these threat clusters’ operational infrastructure, tactics, and target selection methods, suggesting that these wide-scale, botnet-driven ATO threats may be tied to a single (currently unattributed) threat actor.
---
Key TTPs:
• Password spraying – Using generic passwords across multiple accounts
• IP rotation – 2.9K IPs linked to 30 abused proxies & ISPs
• Distinct client agents – Leveraging known web crawlers & RSS fetchers
• ‘O365 Suite UX’ abuse – Targeting M365 native sign-in app
---
IOCs (observed user agents):
• AdsBot-Google
• Bloglines/3.1
• FeedFetcher-Google
• Gaisbot/3.0
• msnbot/0.11 & 1.1
• Peach/1.01 (Ubuntu 8.04 LTS)
• facebookexternalhit/1.1
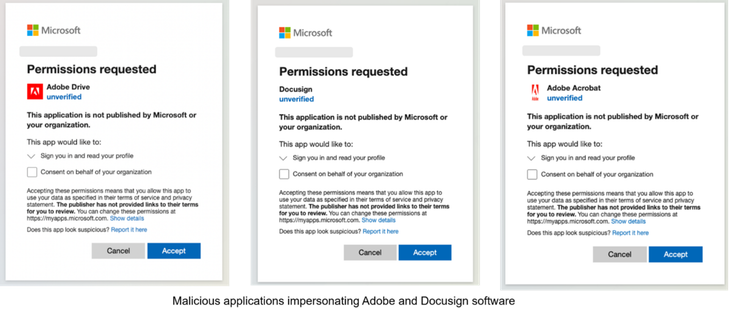
Threat researchers at Proofpoint are tracking two ongoing, highly targeted campaigns combining OAuth redirection mechanisms with brand impersonation techniques, malware proliferation, and #Microsoft365 themed #credentialphishing for #accounttakeover. 🧵⤵️
Proofpoint researchers recently uncovered three previously undisclosed malicious OAuth apps, disguised as ‘Adobe Drive,’ ‘Adobe Acrobat,’ and ‘Docusign’, which are used to redirect users to webpages hosting phishing and malware delivery threats.
To avoid triggering detection solutions, the observed apps were assigned limited scopes (such as profile, email, OpenID). However, Proofpoint’s threat detection engine classified them as malicious, thus protecting Proofpoint Account Takeover Protection (https://brnw.ch/21wRhAw) customers.
Observed IOCs:
App IDs
• 14b2864e-3cff-4d33-b5cd-7f14ca272ea4 (‘Adobe Drive’)
• 85da47ec-2977-40ab-af03-f3d45aaab169 (‘Adobe Drive X’)
• 355d1228-1537-4e90-80a6-dae111bb4d70 (‘Adobe Acrobat’)
• 6628b5b8-55af-42b4-9797-5cd5c148313c (‘Docusign’)
Reply URLs
• hxxps://li.tistateronic[.]ru/OqgX
• hxxps://fancy-bush-61e9sydgsyi29s.jennifer-may.workers[.]dev
• hxxps://fly.storage.tigris[.]dev/log/Statement.HTM
• hxxps://log.fly.storage.tigris[.]dev/Statement.HTM
• hxxps://embeds.beehiiv[.]com/2066d619-1342-40ba-893d-6d0e6eee70d5
Redirection URLs
• hxxps://be645c1d.bentlyerool.pages[.]dev
• hxxps://line.infoapollocapital[.]buzz
According to Proofpoint data, the second half of 2024 saw 78% of organizations experience at least one #accounttakeover (ATO) attempt involving an HTTP client, a 7% increase from the prior six months.
This blog explores the historical and current use of HTTP clients in #ATO attack chains, shedding light on the evolving tactics of threat actors. https://www.proofpoint.com/us/blog/threat-insight/http-client-tools-exploitation-account-takeover-attacks
Defending Against Account Takeovers
Account takeovers (ATOs) are among the most damaging cyberattacks, often leading to data breaches or financial loss. Crowdalert combines real-time monitoring with human verification to stop ATOs before they escalate, prompting users to verify suspicious actions.
Ready to protect your organization? https://crowdalert.com
#Crowdalert #Cybersecurity #AccountTakeover #ATO #SecOps #ThreatDetection
Account takeover attacks are a big threat to business. Cyber criminals gain access to your online accounts, which can expose data, enable theft, and allow further attacks. Proactive security is the answer
#CyberSecurity #AccountTakeover #CyberThreats https://www.techradar.com/pro/mitigating-the-growing-threats-of-account-takeover-attacks-in-2024
📬 Bots machen die Hälfte des gesamten Internetverkehrs aus
#Cyberangriffe #Internet #KünstlicheIntelligenz #AccountTakeover #badbots #imperva #NanhiSingh #WebScrapingBot https://sc.tarnkappe.info/a86b90
Just got two emails with security codes for my #ElectronicArts account even though I've got a long random password set. Anyone else experiencing the same?
"🚨 OAuth Vulnerabilities Exposed: Millions of Accounts at Risk! 🚨"
Recent research by Salt Labs has unveiled alarming vulnerabilities in the OAuth implementations of major online platforms, including Grammarly, Vidio, and Bukalapak. These oversights could have allowed attackers to take over millions of user accounts! 😱
OAuth, a widely adopted authorization protocol, is often perceived as secure. However, its implementation can be tricky. The research highlights the importance of verifying access tokens, a step often overlooked by developers. Without this verification, attackers can exploit tokens from one site to compromise user accounts on another.
For instance, Vidio, an online video streaming platform with 100M monthly users, and Bukalapak, a prominent eCommerce platform in Indonesia with 150M users, were found vulnerable to such attacks. Grammarly, the popular AI-powered writing tool, was also susceptible, potentially exposing users' private documents.
While these companies have since addressed the issues, the findings underscore the critical need for meticulous OAuth implementation and regular security audits. Always remember, it's not just about using secure protocols, but implementing them securely! 🔐
Source: Salt Labs Blog
Tags: #OAuth #Cybersecurity #Vulnerability #AccountTakeover #SaltLabs #Grammarly #Vidio #Bukalapak 🌐🔍🔓
📬 sphero: Hacker Sanggiero erbeutet Daten von 1 Million Nutzern
#Cyberangriffe #ITSicherheit #Szene #AccountTakeover #BreachForums #GraphQLAPI #Hack #Sanggiero #sphero https://tarnkappe.info/artikel/szene/sphero-hacker-sanggiero-erbeutet-daten-von-1-million-nutzern-281603.html
@confluency
POTENTIAL #SECURITY THREAT: The above website, #phanpyDotSocial is #CloudGlare and may be a #socialEngineering attack on #fediverse users to open them up to #accountTakeover.
If the above website asks one to login to ones #mastodon instance with their password then its a CloudGlare #phishing website/#honeypot.
We will not access on ethical grounds.
Tagging some boosters to warn them @njoseph @kkremitzki @michelin
#MITMAttack #MITMaaS #ClOudFlAre #fediverseAttack #cyberAttack
I'm not sure how Google is going to handle all the inactive accounts they are going to delete, but I assume they will do it wrong, and they will be available.
They should really communicate this list to the top companies, and let everyone else first clean up their authentication databases.
The amount of random account takeovers is going to be awesome.