PC World: Hackers are spreading fake password manager ransomware via Bing ads. “Using an old trick, hackers have set up new sites with ‘squatter’ URLs that look close enough to the genuine KeePass site at KeePass.info. On the fake sites, the interface mimics the genuine one to near perfection, offering downloads of the password manager. But according to an investigation by WithSecure, the […]
#passwordManagement
Have I Been Pwned 2.0 is Now Live
https://www.troyhunt.com/have-i-been-pwned-2-0-is-now-live/
#HackerNews #Have #I #Been #Pwned #2.0 #CyberSecurity #DataBreach #OnlineSafety #PasswordManagement
When Strong Passwords Fail: Lessons from a Silent, Persistent Attack
1,038 words, 5 minutes read time.
Pro Git 2nd Edition, Kindle EditionAffiliate Link
Today’s affiliate link features Pro Git, 2nd Edition — available for free at the time of this post. Be sure to grab your copy before the offer ends!
As an IT professional, I pride myself on maintaining robust security practices. I use unique, complex passwords, enable two-factor authentication (2FA), and regularly monitor my accounts. Despite these precautions, I recently experienced a security breach that served as a stark reminder: even the most diligent efforts can fall short if certain vulnerabilities are overlooked.
The Unexpected Breach
I maintain a Microsoft 365 Developer account primarily for SharePoint development. This account isn’t part of my daily workflow; it’s used sporadically for testing and development purposes. To secure it, I employed a 36-character random password—a combination of letters, numbers, and symbols. This password was unique to the account and stored securely.
Despite these measures, I received a notification early one morning indicating a successful login attempt from an unfamiliar location. Fortunately, 2FA was enabled, and the unauthorized user couldn’t proceed without the second authentication factor. This incident prompted an immediate investigation into how such a breach could occur despite stringent password security.
The Silent Persistence of Attackers
Upon reviewing the account’s activity logs, I discovered a disturbing pattern: months of failed login attempts originating from various IP addresses. These attempts were methodical and spread out over time, likely to avoid triggering security alerts or lockouts. This tactic, known as a “low and slow” brute-force attack, is designed to fly under the radar of standard security monitoring systems.
Such persistent attacks underscore the importance of not only having strong passwords but also implementing additional security measures. According to the Cybersecurity and Infrastructure Security Agency (CISA), 2FA is essential to web security because it immediately neutralizes the risks associated with compromised passwords. If a password is hacked, guessed, or even phished, that’s no longer enough to give an intruder access: without approval at the second factor, a password alone is useless .
The Vulnerability of Dormant Accounts
One critical oversight on my part was the assumption that an infrequently used account posed less of a security risk. In reality, dormant accounts can be prime targets for attackers. These accounts often retain access privileges but are not actively monitored, making them susceptible to unauthorized access. As noted by security experts, dormant accounts often fly under the radar, making them perfect targets for threat actors. Since they aren’t actively monitored, cybercriminals can exploit them for weeks—or even months—before being detected .
This realization led me to reassess the security of all my accounts, especially those not regularly used. It’s imperative to treat every account with the same level of scrutiny and protection, regardless of its frequency of use.
Immediate Actions Taken
In response to the breach, I took several immediate steps to secure the compromised account and prevent future incidents:
First, I changed the account’s password to a new, equally complex and unique one. Recognizing that the email address associated with the account might have been targeted, I updated it to a more obscure variation, reducing the likelihood of automated credential stuffing attacks.
Next, I thoroughly reviewed the account’s security settings, ensuring that all recovery options were up-to-date and secure. I also examined the activity logs for any other suspicious behavior and reported the incident to Microsoft for further analysis.
Finally, I conducted a comprehensive audit of all my accounts, focusing on those that were dormant or infrequently used. I enabled 2FA on every account that supported it and closed any accounts that were no longer necessary.
Lessons Learned
This experience reinforced several critical lessons about cybersecurity:
Firstly, password strength alone is insufficient. While complex passwords are a fundamental aspect of security, they must be complemented by additional measures like 2FA. According to research, implementing 2FA can prevent up to 99.9% of account compromise attacks .
Secondly, dormant accounts are not inherently safe. Their inactivity can lead to complacency, making them attractive targets for attackers. Regular audits and monitoring of all accounts, regardless of usage frequency, are essential.
Thirdly, attackers are persistent and patient. The “low and slow” approach to brute-force attacks demonstrates a strategic method to bypass traditional security measures. Staying vigilant and proactive in monitoring account activity is crucial.
Strengthening Security Measures
In light of this incident, I have adopted several practices to enhance my cybersecurity posture:
I now regularly audit all my accounts, paying special attention to those that are dormant or infrequently used. I ensure that 2FA is enabled wherever possible and that all recovery options are secure and up-to-date.
Additionally, I have started using a reputable password manager to generate and store complex, unique passwords for each account. This tool simplifies the process of maintaining strong passwords without the need to remember each one individually.
Furthermore, I stay informed about the latest cybersecurity threats and best practices by subscribing to security newsletters and participating in professional forums. This continuous learning approach helps me adapt to the evolving threat landscape.
Conclusion
This incident served as a sobering reminder that no one is immune to cyber threats, regardless of their expertise or precautions. It highlighted the importance of a comprehensive security strategy that includes strong passwords, multi-factor authentication, regular account audits, and continuous education.
I encourage everyone to take a proactive approach to cybersecurity. Regularly review your accounts, enable 2FA, use a password manager, and stay informed about emerging threats. Remember, security is not a one-time setup but an ongoing process.
If you found this account insightful, consider subscribing to our newsletter for more cybersecurity tips and updates. Share your thoughts or experiences in the comments below—we can all learn from each other’s stories.
D. Bryan King
Sources
- CISA – Multi-Factor Authentication (MFA)
- arXiv – Understanding Multi-Factor Authentication Efficacy
- Microsoft – Why MFA Is a Must
- NCSC – Password Guidance: Simplifying Your Approach
- Tekie Geek – The Danger of Dormant Accounts
- OWASP – Authentication Cheat Sheet
- Bruce Schneier – Low and Slow Brute-Force Attacks
- Have I Been Pwned – Check if Your Email Was Compromised
- Australian Cyber Security Centre – Securing Your Accounts
- NIST – Updated Guidance on Digital Identity
- Kaspersky – Password Security Tips
- 1Password Blog – The Importance of MFA
Disclaimer:
The views and opinions expressed in this post are solely those of the author. The information provided is based on personal research, experience, and understanding of the subject matter at the time of writing. Readers should consult relevant experts or authorities for specific guidance related to their unique situations.
Related Posts
#2FA #accountHacking #accountMonitoring #accountTakeover #bruteForceAttack #cloudAccountProtection #cloudSecurity #compromisedAccount #compromisedCredentials #compromisedMicrosoftAccount #credentialStuffing #credentialTheft #cyberattack #cybercrime #cybersecurity #cybersecurityAwareness #cybersecurityLessons #developerAccountSecurity #dormantAccounts #emailSecurity #hackerPrevention #howHackersBypassMFA #identityProtection #infosec #ITProfessionals #ITSecurity #ITSecurityIncident #loginSecurity #lowAndSlowAttack #MFA #MFAImportance #Microsoft365Security #MicrosoftLogin #passwordAloneNotEnough #passwordBreach #passwordEntropy #passwordHygiene #passwordManagement #PasswordSecurity #passwordVulnerability #persistentThreats #phishingProtection #randomHashPassword #realWorldBreach #realWorldCybersecurity #securePasswords #securingDormantAccounts #securityAudit #securityBestPractices #securityBreach #SharePointDeveloperAccount #SharePointSecurity #strongPasswords #techSecurityBreach #tokenHijacking #TwoFactorAuthentication
Mashable: A review of 19 billion passwords reveals people are still bad at them. “Researchers at Cybernews studied more than 19 billion leaked passwords, and of those just 6 percent were identified as unique, meaning they weren’t re-used or duplicated. To make matters worse, the most common passwords are way too simple. Four percent of all passwords studied by Cybernews — meaning roughly […]
Microsoft is shaking things up—password autofill is leaving Authenticator for good! Get ready to transition to Edge by August 2025 or risk losing saved credentials. Are you set for this new security era?
#microsoftedge
#passwordmanagement
#cybersecurity
#microsoftauthenticator
#browsersecurity
OpSec Mastery: Tools for the Silent Revolution #Cybersecurity, #OpSec, #Privacy, #Encryption, #Anonymity, #DigitalSecurity, #Hacking, #PasswordManagement, #Linux, #VPN, #PGP, #Signal, #TailsOS, #Cryptography, #ThreatIntelligence, #Malware, #DataProtection, #TwoFactorAuthentication, #Tor, #DigitalFootprint, #EthicalHacking, #SecureCommunications, #ZeroTrustSecurity, #CyberGhost, #NetworkSecurity
http://tomsitcafe.com/2025/04/27/opsec-mastery-tools-for-the-silent-revolution/
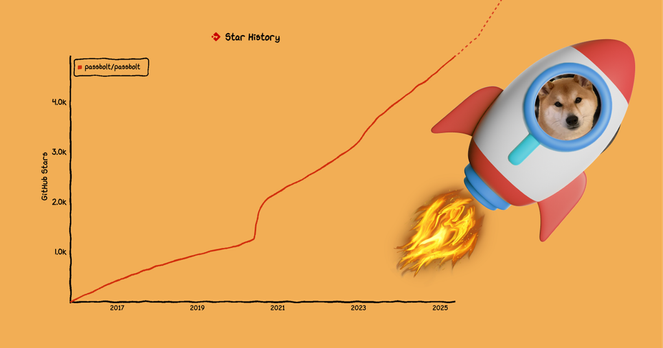
🌟 Our magic number is 5 and we just hit it! 🌟
5,000 stars on GitHub for the Passbolt 5.x series!
A massive thank you to everyone in the passbolt community who endorsed us.
Your star helps show that open source access and credential collaboration matters.
Haven’t starred us yet? There's still time to shine: https://github.com/passbolt/passbolt_api
You can also watch the videos on YouTube: https://youtube.com/playlist?list=PLzjv2928Zl0VIb3_8GK3sTPDEjrFMbohS&si=qcpTWuJLLT3I_I4X
#OpenSource #PasswordManagement #Cybersecurity
2/2
🔐 Password Hygiene: Rotating the Wardrobe of Digital Defense #PasswordHygiene #PasswordRotation #SmallBusinessSecurity #Cybersecurity #OpenSource #FreeTools #PasswordManager #KeePassXC #Bitwarden #Passbolt #TwoFactorAuthentication #2FA #Fail2ban #Yubikey #TOTP #OpenSourceSoftware #PasswordStrength #BusinessSecurity #DigitalDefense #SecurityPractices #PasswordPolicy #PasswordManagement #CybersecurityTips #SecurePasswords #BusinessCybersecurity #ITSecurity #OnlineSecurity
The Passbolt team is now at Forum InCyber (FIC) Europe 2025 and we’re all set up at booth F9-9.
Got questions about Passbolt? Curious about secure credential sharing? Want some exclusive fun stickers? Come say hi to Max Zanardo and Remy Bertot — they’ll be at the event until April 3rd.
#OpenSource #InCyberForum #Cybersecurity #PasswordManagement
Our magic number is 5!
Passbolt version 5 is just around the corner, and we’re about to hit 5,000 GitHub stars.
⭐ Star the repo
📣 Invite others to do the same
🔁 Share this post and spread the word
A high 5 to everyone who stars us here:
https://github.com/passbolt/passbolt_api
Voice Dream - Text to Voice
Version: 5.1.3 • 268.9 MB
Improvements to bionic mode and better password management
#VoiceDream, #BionicMode, #TextToSpeech, #app, #AppUpdate, #iOS, #AccessibilityFeatures, #PasswordManagement.
From sharing passwords and secrets to brand new stickers - we’ve got you covered at Forum INCYBER Europe (FIC) from April 1–3 in Lille.
Swing by Booth F9-9 to meet the team, explore our open source collaborative credential manager, and grab some of these exclusive freshly-printed stickers.
See you there! https://europe.forum-incyber.com/
Choosing the right tool for password and secret sharing? Here are 7 key criteria every organization should consider:
1. Granular access controls
2. TOTP delegation
3. Logging and reporting
4. High usability
5. Scalable workflows
6. Compliance readiness
7. Deployment options
Learn how to evaluate credential collaboration software in our free guide, originally published in TechRadar Pro: https://hubs.li/Q03cW5Hc0
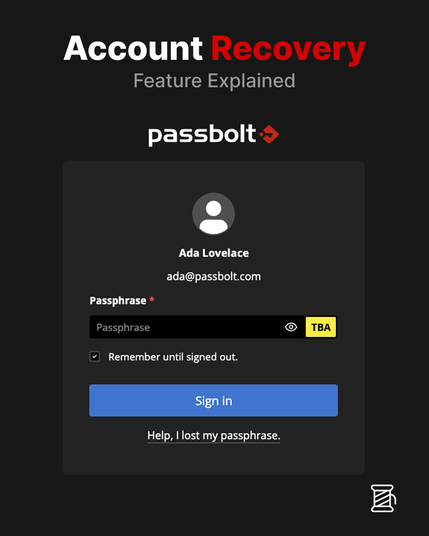
Explaining passbolt's account recovery feature.
Learn more: https://www.passbolt.com/docs/admin/authentication/account-recovery/
Watch the video: https://youtube.com/shorts/pXYEhlsRJ3E
#OpenSource #PasswordManagement #SecretsManagement
1/9
🔐 Tired of forgetting your passwords or spending time trying to remember them? Simplify your digital life with our state-of-the-art Password Manager! Effortlessly store, manage, and autofill passwords and other sensitive data securely and conveniently. Say goodbye to password headaches and hello to peace of mind! 🛡️✨
👉 Learn more or buy here: https://appsumo.8odi.net/locker-password-manager
KeePassXC Snap App Finally Supports Web Browser Integration
The KeepassXC snap package now “just works” with web browsers, with the latest update adding support for native messaging using secure desktop portals. KeePassXC is a cross-platform, open-source password manager billed as a ‘community-driven port of the Windows application ‘Keepass Password Safe'”. It supports Linux (including CLI), and a snap package has been available since 2017. But until now users who installed the snap to leverage the browser integration (be it auto-fill of usernames and passwords on websites they visit, or saving credentials for new accounts they create) have needed to use a workaround involving an external script. Aside from :sys_more_orange:
#News #Keepass #Keepassxc #PasswordManagement
:sys_omgubuntu: https://www.omgubuntu.co.uk/2025/02/keepassxc-snap-update-adds-native-messaging-support-i-e-browser-integration
1Password now lets you add physical locations to your passwords and items! 🗺️ Now, your passwords appear automatically in the app when you're nearby. Secure, smart, and location-aware! 🔒 #1Password #Cybersecurity #PasswordManagement #TechInnovation #Privacy #MobileSecurity
Unlocking the Secrets to Unbreakable Passwords: Your Ultimate Guide to Online Security
791 words, 4 minutes read time.
In today’s digital age, safeguarding your online presence has never been more critical. With cyber threats lurking around every corner, ensuring your accounts are protected by strong, unique passwords is paramount. This comprehensive guide will walk you through the essentials of creating and maintaining robust passwords, helping you fortify your digital defenses.
Introduction
Imagine leaving your front door wide open, inviting anyone to walk in. That’s essentially what you’re doing when you use weak passwords online. Cybercriminals are constantly on the prowl, seeking easy targets. By bolstering your password strength, you can deter these malicious actors and keep your personal information safe.
The Anatomy of a Strong Password
A formidable password is your first line of defense against unauthorized access. But what makes a password strong? Let’s break it down:
- Length Matters: Aim for passwords that are at least 12 characters long. The longer your password, the more combinations a hacker has to guess, making their task exponentially harder.
- Complexity is Key: Incorporate a mix of uppercase and lowercase letters, numbers, and special symbols. This diversity adds layers of difficulty for anyone attempting to crack your code.
- Unpredictability: Steer clear of common words, phrases, or easily guessable information like birthdays or pet names. Instead, opt for random combinations that don’t form recognizable patterns.
Crafting Your Fortress: Methods for Creating Strong Passwords
Creating a robust password doesn’t have to be a daunting task. Here are some effective strategies:
- Passphrases: Combine unrelated words to form a phrase that’s easy for you to remember but tough for others to guess. For example, “SunflowerJazzMountainRiver” is both lengthy and complex.
- Password Managers: These tools can generate and store complex passwords for you, ensuring each of your accounts has a unique key. Services like LastPass offer password generators that create strong passwords, reducing the burden on your memory.
- Personal Algorithms: Develop a formula that only you know. For instance, take the first letters of a memorable sentence and mix in numbers and symbols. “I love to travel to 5 countries every year!” becomes “Ilt2t5c3y!”.
Avoiding Common Pitfalls
Even with the best intentions, it’s easy to fall into habits that compromise your security. Here are some mistakes to watch out for:
- Password Reuse: Using the same password across multiple sites is a recipe for disaster. If one account is breached, all your accounts become vulnerable.
- Simple Substitutions: Replacing ‘a’ with ‘@’ or ‘o’ with ‘0’ is no longer sufficient. Hackers are well-versed in these tricks and can easily bypass them.
- Neglecting Updates: Regularly updating your passwords adds an extra layer of security. Aim to change them at least once every six months.
Enhancing Security with Additional Tools
Beyond strong passwords, consider these tools to bolster your online security:
- Multi-Factor Authentication (MFA): This requires multiple forms of verification to access an account, making unauthorized access significantly more difficult.
- Password Managers: As mentioned earlier, they not only generate strong passwords but also store them securely, so you don’t have to remember each one.
- Regular Monitoring: Keep an eye on your accounts for any suspicious activity. Services like HaveIBeenPwned can alert you if your information has been compromised.
Maintaining Vigilance: Best Practices
Staying secure is an ongoing process. Here are some habits to adopt:
- Educate Yourself: Stay informed about the latest security threats and updates. Knowledge is a powerful tool in protecting yourself.
- Be Skeptical: Phishing attempts are common. Always verify the source before clicking on links or providing personal information.
- Secure Your Devices: Ensure your devices have the latest security updates and use reputable antivirus software.
Conclusion
Protecting your online identity starts with strong, unique passwords. By implementing the strategies outlined in this guide, you can significantly reduce the risk of unauthorized access and keep your personal information safe. Remember, in the digital world, a robust password is your best defense.
For more insights on creating strong passwords, visit Microsoft’s guide on creating and using strong passwords.
Stay updated with the latest cybersecurity practices by following the Cybersecurity & Infrastructure Security Agency (CISA).
D. Bryan King
Sources
- How to Create a Strong Password in 2025: Examples and Guide
- Internet Safety: Creating Strong Passwords – GCFGlobal
- How to Create a Secure Password – Cybersecurity Tips
- How to Create a Strong Password – WordPress Security – YouTube
- How to Create a “Strong” Password | Mrs. Martin’s Music Room
- 4 Tips to Strengthen Your Passwords
- PiXi: Password Inspiration by Exploring Information
- You should actually ignore ’90 day’ password rule – as experts warn ‘myth’ is easy way to become instant ‘victim’
Disclaimer:
The views and opinions expressed in this post are solely those of the author. The information provided is based on personal research, experience, and understanding of the subject matter at the time of writing. Readers should consult relevant experts or authorities for specific guidance related to their unique situations.
Related Posts
Rate this:
#avoidPasswordHacks #avoidWeakPasswords #bestPasswordPractices #bestSecurityPractices #bestWaysToSecurePasswords #createSecurePasswords #createStrongPasswords #cyberProtection #cybersecurityAwareness #cybersecurityForBeginners #CybersecurityTips #digitalIdentityProtection #digitalSecurity #encryptedPasswords #hackingPrevention #howToMakeAStrongPassword #howToSecureAccounts #identityTheftProtection #MFASecurity #multiFactorAuthentication #onlinePasswordProtection #onlinePrivacy #onlineSafety #OnlineSecurity #passwordBestPractices #passwordCrackingPrevention #passwordHackingPrevention #passwordManagement #passwordManagerBenefits #passwordManagerTools #passwordProtection #passwordSafety #passwordSafetyTips #PasswordSecurity #passwordSecurity2025 #passwordSecurityAwareness #passwordSecurityGuide #passwordSecurityTips #passwordSecurityTools #passwordStrengthChecker #passwordVault #personalDataProtection #preventHacking #preventIdentityTheft #preventPasswordLeaks #preventPhishingAttacks #protectPersonalData #safeOnlinePractices #safePasswordTips #secureLoginTips #secureOnlineAccounts #secureYourPasswords #stopHackers #strongPasswordGenerator #strongPasswordStrategies #strongPasswords #TwoFactorAuthentication
Looking to secure your passbolt instance with an SSL certificate on Windows?
From self-signed certificates for testing to trusted CA certificates for production, this guide walks you through the step-by-step process to generate, configure, and install SSL certificates for passbolt on Windows.
🔗 Read the full guide: https://hubs.li/Q037YnB20
#Passbolt #OpenSource #PasswordManagement #SSL #WindowsSecurity