В новый #htop добавили вкладку с i/o, теперь #iotop стал ненужен. Осталось добавить функции #atop, #atopsar, мониторинг сети и будет универсальный комбайн для мониторинга системы.
#atop
Archiv: #EKOI ULTRALIGHT 2 Carbon #Rennradschuhe im Test. Meine ersten #Erfahrungen in Deutschland. https://www.sports-insider.de/ekoi-ultralight-2-carbon-rennradschuhe-im-test-meine-ersten-erfahrungen-in-deutschland-44081/ #Testbericht #PlanetX #Erfahrungsbericht #ATOP #Fahrradschuhe #Test
Nuevo contenido... hoy estuve viendo #monitoresDeSistemaXTTY y probé algunos que no conocía como : #aidar #glances #atop #s-tui https://elprofejuan.duckdns.org/autosave-886180b941bfe0b40a81bd5b5ea5ad71
https://www.fogolf.com/958951/rory-mcilroy-on-verge-of-career-grand-slam-leading-masters-by-two-shots-heading-into-final-round/ Rory McIlroy on verge of career Grand Slam, leading Masters by two shots heading into final round #atop #Augusta #back #Before #by #Career #Charged #CLEAR #FINAL #finishing #Golf #GolfNews #Grand #heading #historic #into #Lead #leaderboard #Leading #Masters #mcilroy #Mondays #Nationals #Nine #of #on #rory #round #Shots #slam #stand #Start #Strong #third #TIME #two #Verge #with
Oh, #atop fixed their security issue https://www.atoptool.nl/downloadatop.php
So ... all good now?
https://security-tracker.debian.org/tracker/source-package/atop
The updated news is that atopgpud's TCP service, that I mentioned, is indeed one problem.
https://github.com/Atoptool/atop/issues/334
It does beg the question of why it uses TCP at all, when an AF_LOCAL socket in /run/atop/ or something is more in line with its other data-collection service.
Far from the only problem with atopgpud.
However, note that someone else has run xyr own code checker on atop in the meantime and claims to have found a problem nonetheless.
I saw it, and I agree with people's response to "This is not the way to do this.", which was: "Then why did you do it that way, then?"
I've just installed #atop on #sydbox #ctf server in case people want to explore exploiting the recent heap corruption. I don't trust jia tan enough to leave atop.service running as root though so the attack vector is limited. Sail with #ssh to syd.chesswob.org (user/pass: syd) or go to https://syd.chesswob.org although the #nodejs client is a bit more limited. See here for the #security issue, https://www.openwall.com/lists/oss-security/2025/03/26/2 (tl;dr uninstall #atop asap!) and here for #sydbox #ctf https://ctftime.org/event/2178
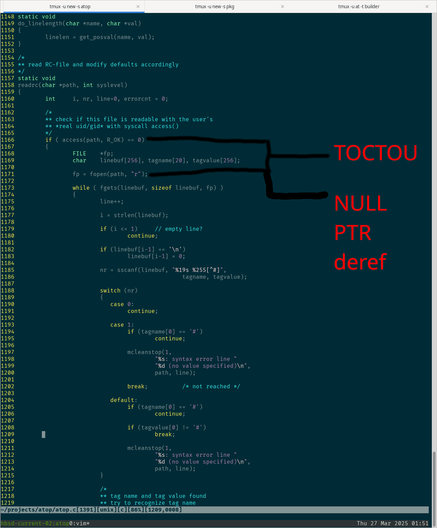
There's a whole bunch of dodgy stuff, from atopgpud to code that assumes that it can blat a NUL and then call strcpy().
See thread at
https://social.chatty.monster/@losttourist/114229385233902820
People who wrote their system tools with safe string libraries such as DJB's, skalibs, or even just C++'s std::string automatically suspect such tries-to-be-clever-with-NULs code.
At the bare minimum, tag the SPC onto the destination buffer & don't touch the (possibly only 1) NUL-terminated source buffer. But better yet, don't do it that way at all.
But there are so many other poor practices in that software, including the aforementioned atopgpud TCP server.
These things when undisclosed are usually almost never reflected in GitHub.
I looked at the code yesterday, and, from inspection only, my suspicion immediately landed on photoproc.c .
There's some dodgy C trickery going on there that I wouldn't put past having some edge cases.
Assuming (wrongly) that a string is doubly-NUL terminated (not guaranteed by getdelim()), blatting the first NUL with a SPC and then calling strcpy() is just one such suspect case.
Ну чёт я нифига не понял: