Thirty years of curl
Curl is for me part of the critical tools in any POSIX OS. Even in closed source OS like win64 curl is vital.
My gratitude is infinite
curl --verbose wttr.in/palmentuin|lolcat
...gets me such nice formatted output to (ba cs k z)sh
100% pure shell output, no browser needs to be spawned for that!
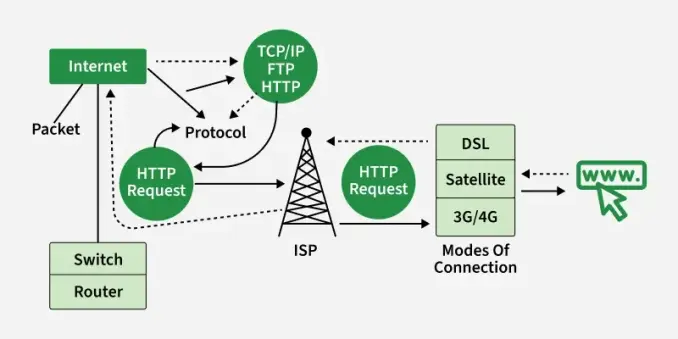
Curl usage
curl is used in command lines or scripts to transfer data. curl is also libcurl, used in cars, television sets, routers, printers, audio equipment, mobile phones, tablets, medical devices, settop boxes, computer games, media players and is the Internet transfer engine for countless software applications in over twenty billion installations.
curl is used daily by virtually every Internet-using human on the globe!
sources:
https://curl.se/
https://ioc.exchange/@bagder@mastodon.social/116130454645581888
#curl #critical #program #birthday #congratulations #30years #fun #jokes #OpenSource #POSIX #programming #networking #protocols #TCP #SSH