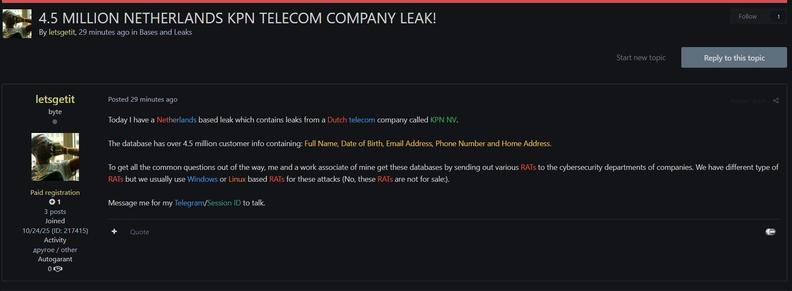
A medium confidence data breach has targeted a Dutch telecom company, KPN N.V. 🇳🇱 in the Netherlands, within the Network & Telecommunications sector. #DataBreach #TelecomSecurity #CyberThreat
#telecomsecurity
🤖 Here is a summary for you! @technadu
#TelecomSecurity #CyberSecurityRules #DataProtection #IMEIVerification #PolicyUpdate
DoT has clarified that the Telecom Cyber Security (TCS) Amendment Rules 2025 remain active, despite a duplicate Gazette publication being withdrawn.
The updates introduce MNV-based identity validation, enhanced IMEI verification for resold devices, and tighter coordination with TIUEs handling telecom identifiers - all with data-protection guardrails.
Thoughts from the security community on the practical impact?
Follow @technadu for more vendor-neutral policy and infosec reporting.
#infosec #cybersecurity #telecomsecurity #DoT #DigitalIndia #fraudprevention #policy
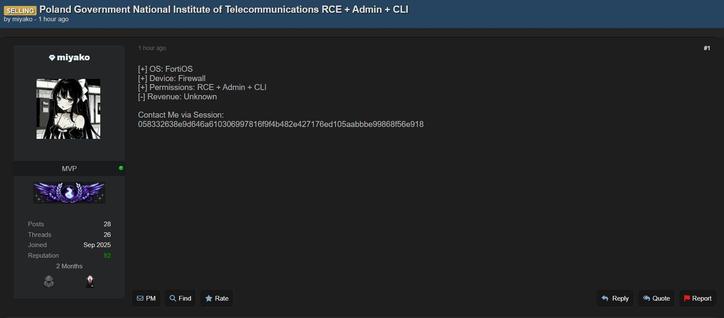
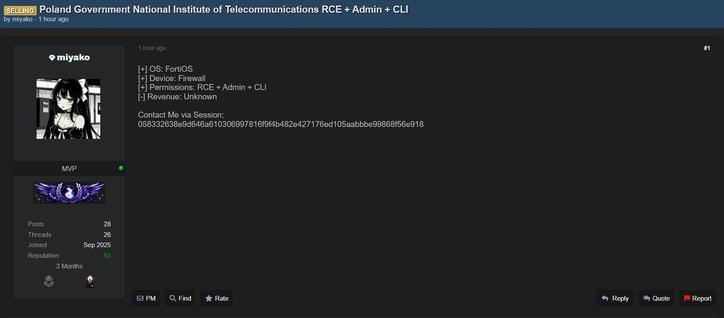
High confidence initial access attempt detected targeting Poland 🇵🇱 and its National Institute of Telecommunications in the Network & Telecommunications sector. #CyberThreats #TelecomSecurity #ThreatIntel
High confidence initial access activity detected targeting the national institute of telecommunications in Poland 🇵🇱. The sector involved is Network & Telecommunications. #CyberThreat #Poland #TelecomSecurity
The FCC has reversed a telecom security measure originally introduced after the Salt Typhoon intrusions.
Supporters cite authority and flexibility concerns; critics warn the shift may weaken protections around lawful intercept systems - longstanding targets of sophisticated threat actors.
💬 Thoughts on whether CALEA needs a modernized, standards-based framework?
👍 Follow @technadu for more infosec insights.
#Infosec #FCC #TelecomSecurity #CALEA #SaltTyphoon #Cybersecurity #CriticalInfrastructure #ThreatIntel #DigitalSafety
Ribbon Communications was breached by nation-state hackers who lurked undetected for months—revealing just how deep and stealthy modern cyber espionage can be. How vulnerable is our digital infrastructure?
#nationstateattack
#cyberespionage
#telecomsecurity
#cyberthreats
#ribboncommunications
📞 Caller ID spoofing is now industrialized.
Europol urges a unified European framework to stop “spoofing-as-a-service” kits enabling large-scale impersonation scams.
Losses exceed €850M annually, with law enforcement calling for cross-border cooperation and technical standards to trace calls.
Can telecoms realistically close this gap - or do we need new protocols at the network level?
💬 Share your take & follow @technadu for more global cyber policy coverage.
#CyberSecurity #Europol #CallerIDSpoofing #TelecomSecurity #ThreatIntelligence #NetworkDefense #CyberPolicy #InfoSec
A global scam network renting out tens of thousands of phone numbers—Europol’s SIMCARTEL bust uncovered glaring telecom vulnerabilities and sparked international teamwork against cybercrime. How will this change our digital world?
#cybercrime
#europol
#telecomsecurity
#publicprivatepartnership
#infosec
#simbox
#cybersecurity
#lawenforcement
#forensicanalysis
KT assures markets that no SIM key data was compromised, eliminating concerns over cloned phones and reinforcing confidence in telecom security.
#YonhapInfomax #KT #SIMKey #DataLeak #ClonedPhones #TelecomSecurity #Economics #FinancialMarkets #Banking #Securities #Bonds #StockMarket
https://en.infomaxai.com/news/articleView.html?idxno=82400
Top 5G Security Vulnerabilities: Insights from P1 Security Pentest Activities
From weak authentication to misconfigured core functions, 5G deployments keep revealing new ways attackers can break into critical infrastructure.
Join our 5G Penetration Tester El Mehdi Regragui as he shares exclusive findings from P1 Security’s pentest activities, including:
✔ Real-world vulnerabilities in 5G networks
✔ Lessons learned from offensive security engagements
✔ Key takeaways for operators and vendors to strengthen defenses
Register here: https://watch.getcontrast.io/register/p1-security-top-5g-security-vulnerabilities-insights-from-p1-security-pentest-activities
Orange Belgium’s cyberattack hit 850,000 accounts and exposed SIM unlock codes—an alarming wake-up call for telecom security. Think your phone data is safe? Discover the full story.
https://thedefendopsdiaries.com/orange-belgium-cyberattack-a-wake-up-call-for-telecom-security/
#cybersecurity
#telecomsecurity
#databreach
#orangecyberattack
#infosectrends
Weekly output: Ford’s EV strategy, Open RAN security risks, Waymo + Spotify
After a week and a half on the West Coast that began with Black Hat, I can now turn my attention to catching up on the talks I had to skip at that conference, since on-demand video is now available for all but a handful of its sessions. Video of some DEF CON talks is also now starting to pop up, and I’m looking forward in particular to seeing the Voting Village talks that I missed because I bugged out of Vegas Friday afternoon of that week.
Patreon readers got a recap of Black Hat that included some observations about Washington’s wilted presence at this security conference and the generally skeptical take of conference speakers on AI hype.
8/11/2025: Ford Announces $5B Plan to Make EVs Cheaper, Starting With $30,000 Pickup, PCMag
With PCMag’s automotive writer traveling, I stepped in to write this breakdown of the automaker’s ambitious plan to reinvent electric-vehicle production. I hope Ford can deliver on this, and I hope the coming family of cheaper EVs will include a four-door hatchback (even if they call it an SUV or a crossover because it’s a little taller than a sedan).
8/14/2025: Researchers recap some security downsides to open RAN, Light Reading
This Black Hat briefing on Thursday of the previous week about possible vulnerabilites in Open RAN (Radio Access Network) sites went much deeper in the weeds than I usually get when covering telecom infrastructure. So I took an extra couple of days to look over the presentation again, read the reports linked to from it, listen again to my recording of the session, and briefly quiz researchers Tianchang Yang and Kai Tu over e-mail. And then I somehow typed two numbers wrong in the same graf, both of which I’d had correct in my notes. Fortunately, my editor quickly fixed those flubs after Yang brought them to my attention.
8/16/2025: Waymo Picks Up Spotify: Cue Up Personal Playlists on Robotaxi Rides, PCMag
I found out about this change to the Waymo ride experience not from one of that Alphabet subsidiary’s social-media posts, a note from any of its publicists, or an announcement on its site, but from an e-mail I got as a Waymo customer Friday morning. I felt a little bad learning that Waymo had posted this news on four different social platforms Tuesday, but then I realized that earlier news coverage had not mentioned Waymo’s removal of online documentation about an older, jankier way to play music from your phone through a Waymo robotaxi’s speakers.
#5G #BlackHat #correction #electricCars #electricVehicles #EVs #Ford #OpenRAN #robotaxi #Spotify #streamingMusic #telecomSecurity #Waymo
One of the talks you can’t miss at #OrangeCon2025: KPN ethical hackers Sebastiaan Groot & Frank Cozijnsen reveal how they discovered a remote code execution (RCE) vulnerability in a standard Steering of Roaming system and how they creatively turned it into two-way communication across networks.
Check out the full schedule and get your tickets: orangecon.nl/#schedule
#OrangeCon2025 #Cybersecurity #TelecomSecurity #RCE #EthicalHacking
📡 IMS and SIP: The Brains Behind Telecom Services — and Prime Targets for Attackers
Modern telecom systems rely heavily on IMS and SIP to deliver multimedia services across prepaid and postpaid platforms. But with great flexibility comes major exposure:
⚠️ SIP spoofing, session hijacking
⚠️ IMS DoS and third-party app vulnerabilities
⚠️ Weak authentication and interception risks
In our blog post, we break down:
🔍 How IMS and SIP actually work
🔍 Where the most critical vulnerabilities lie
🔍 How telcos can reinforce their infrastructure — both technically and operationally
🔗 Read the full article here:
💡 Want to go deeper? Our TS-250 training helps security teams and operators master IMS vulnerabilities: https://online-training.p1sec.com/course/ims
#TelecomSecurity #IMS #SIP #VoLTE #MobileNetworkSecurity #P1Security #VulnerabilityManagement #TS250 #Training #5G #Diameter #Smishing #SessionHijacking
🚨 Why Responsible Disclosure in Telecom Still Fails – And How P1 Security Acts
Many telco vulnerabilities never make it into public CVEs. Vendors delay, ignore, or quietly patch—without alerting operators. Meanwhile, critical infrastructure stays exposed.
At P1 Security, our process doesn’t wait in silence:
🔍 We research, pen-test, and notify both clients and vendors
⏳ We follow a 180-day disclosure window (double the standard)
🧠 When vendors remain silent, we document and publish responsibly in our Vulnerability Knowledge Base
📣 Clients are always informed and can assess their risk
Transparency isn’t optional in telecom—it’s a necessity.
🔗 https://www.p1sec.com/blog/responsible-vulnerability-disclosure-policy
#TelecomSecurity #ResponsibleDisclosure #CVE #VulnerabilityResearch #P1Security #VKB
🎥 What is O-RAN, really?
O-RAN isn't just a buzzword — it's a structural shift in how we build radio access networks.
By moving away from proprietary, locked-in systems and toward open, cloud-native architectures, operators gain flexibility… but also inherit new risks.
At the beginning of this analysis, we lay the groundwork — defining what O-RAN is before unpacking the security implications throughout the session.
▶️ Watch the full webinar for the complete breakdown: https://app.getcontrast.io/register/p1-security-open-ran
#ORAN #TelecomSecurity #5GSecurity #MobileNetworks #NetworkSecurity #CRAN #OpenRAN #TelcoSec #TelecomTransformation #CyberSecurity #P1Security
Vodafone just got hit with a €51M fine over bogus contracts by shady partner agencies. How deep do these security breaches really go—and what does it mean for your data?
https://thedefendopsdiaries.com/vodafone-fined-for-data-breaches-a-wake-up-call-for-telecoms/
#vodafone
#databreach
#telecomsecurity
#gdprcompliance
#cybersecurity
SK Telecom fell victim to a silent three-year cyberattack that exposed millions of users—thanks to a single web shell. How did such a massive breach slip by for so long, and what does it mean for our data security?
#sktelecombreach
#cybersecurity
#databreach
#infosec
#telecomsecurity
O2 UK's VoLTE and WiFi Calling security breach could let hackers intercept your call data and track your location. How safe are your conversations? Dive into the details now.
#volte
#wifi-calling
#telecomsecurity
#encryptionflaw
#userprivacy