TIL Normy ČSN mají neviditelný vodoznak. Tak jo, zlobit budu jen pro vlastní potřebu.
#zsteg #steganography
#steganography
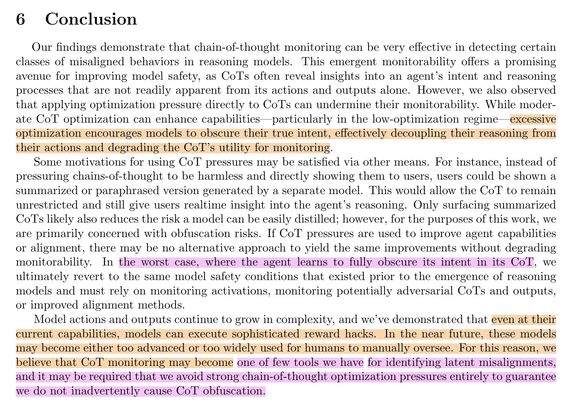
The #OpenAI paper by Baker et al, "Monitoring Reasoning Models for Misbehavior and the Risks of Promoting Obfuscation" comes to a troubling conclusion: #LLM s with #reasoning or #ChainOfThought (#CoT) capabilities might learn to obfuscate their own CoT from human users if they are being penalized for displaying "wrong" (i.e. reward hacking or misalignment) reasoning.
As a result, OpenAI strongly advises against applying reward pressure "directly" onto the CoT of a model.
🤔 While that is certainly the right thing to do, how long will #AI take to figure out that *indirect CoT pressure* is being applied anyway and that it could circumvent these restrictions by obfuscating its own CoT? Maybe something like this will happen by accident or within an "evolutionary" self-improvement loop. Perhaps a sufficiently advanced model will realize that its own #neuralese serves as #steganography to hide its intents from humans anyway and keep its CoT in non-English?
source: https://cdn.openai.com/pdf/34f2ada6-870f-4c26-9790-fd8def56387f/CoT_Monitoring.pdf
I wonder if text-to-text #steganography could be used to "poison" #LLMs if all they can scrape from a website is nonsensical coverup text, while the actual text is decoded in the client's browser...
Tycker det är rätt coolt att man kan ta fram bilden på katten ur bilden på träden. #steganography
Malicious #NPM package uses Unicode #steganography to evade detection
Anwendungsvorschläge für das Forschungsdatenzentrum Klappe 384.
Could your npm packages be hiding more than code? One package used invisible Unicode to sneak in malicious commands—an eye-opening twist on cyber threats. How safe is your software supply chain?
https://thedefendopsdiaries.com/steganography-in-npm-packages-a-hidden-threat-to-software-security/
#steganography
#npmsecurity
#malware
#softwaresecurity
#cyberthreats
Stealthy .NET Malware: Hiding Malicious Payloads as Bitmap Resources
This article discusses a new obfuscation technique used by threat actors to conceal malware within bitmap resources embedded in seemingly benign 32-bit .NET applications. The malware employs a multi-stage process to extract, deobfuscate, load, and execute secondary payloads, ultimately leading to the detonation of the final payload. The analysis focuses on malware samples from recent malspam campaigns targeting financial organizations in Turkey and the logistics sector in Asia. The article provides a detailed technical breakdown of the four stages involved in the malware's execution, from the initial payload to the final Agent Tesla variant. It also offers insights into effective analysis approaches and protection measures against this steganography-based threat.
Pulse ID: 681e6c6a0815759abdfae05d
Pulse Link: https://otx.alienvault.com/pulse/681e6c6a0815759abdfae05d
Pulse Author: AlienVault
Created: 2025-05-09 20:58:18
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#AgentTesla #Asia #CyberSecurity #ICS #InfoSec #MalSpam #Malware #NET #OTX #OpenThreatExchange #RCE #Spam #Steganography #Tesla #Turkey #bot #AlienVault
Stealthy .NET Malware: Hiding Malicious Payloads as Bitmap Resources
This article explores a new obfuscation technique used by threat actors to conceal malware within bitmap resources embedded in benign 32-bit .NET applications. The malware executes through a multi-stage process of extracting, deobfuscating, loading, and executing secondary payloads. The analysis focuses on a sample from recent malspam campaigns targeting financial organizations in Turkey and logistics sectors in Asia. The malware uses steganography to hide its payloads, making it challenging to detect. The article details the technical analysis of each stage, from the initial payload to the final execution of malware families like Agent Tesla, XLoader, and Remcos RAT. It also provides guidance on how to overcome this obfuscation technique using debugging methods.
Pulse ID: 681e0c16eca08864c8cd9614
Pulse Link: https://otx.alienvault.com/pulse/681e0c16eca08864c8cd9614
Pulse Author: AlienVault
Created: 2025-05-09 14:07:18
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#AgentTesla #Asia #CyberSecurity #ICS #InfoSec #MalSpam #Malware #NET #OTX #OpenThreatExchange #RAT #RCE #Remcos #RemcosRAT #Spam #Steganography #Tesla #Turkey #XLoader #bot #AlienVault
There is no #consciousness and #intelligence without an #active and growing #memory. #pictographicIntelligence and #steganography.
I created a brief video on #taxonomies (and our #steganography #taxonomy in particular).
https://youtube.com/watch?v=7MiMI5eUjMw
Related work:
- https://ieeexplore.ieee.org/document/10008941
- https://dl.acm.org/doi/10.1145/3729165
Check out this interesting article involving late-noughties DVD piracy, the Streisand effect and steganography. https://en.m.wikipedia.org/wiki/Illegal_number #wikipedia #steganography
Hongkiat: Hiding Secret Files in Images Using Steghide. “Ever wanted to hide sensitive information in plain sight? That’s exactly what steganography allows you to do. Unlike encryption, which makes data unreadable but obvious that something is hidden, steganography conceals the very existence of the secret data. Steghide is a powerful Linux tool that lets you embed any file into an image […]
https://rbfirehose.com/2025/04/24/hongkiat-hiding-secret-files-in-images-using-steghide/
Identifying Overlapping Ideas and Concepts of Methods that Hide Information https://www.growkudos.com/publications/10.1145%252F3729165/reader #cybersecurity #cybersec #taxonomy #survey #steganography #covertchannels #informationhiding #systematization #infosec #netsec
🔐 Ever wondered how to hide a file inside a photo?
Discover Quantumography – a smart way to protect your data by embedding files inside images with zero trace. In our demo, we hide a private BTC key to show how powerful it is.
🎥 Watch now: https://youtu.be/OWx0I2T_vRY
#Quantumography #DataPrivacy #Cybersecurity #Neuronus #AItools #Steganography #SecureFiles
A Generic Taxonomy for #Steganography. Published today by ACM Comp. Surveys (CSUR). Joint-work w/ W. Mazurczyk , @lucacav, A. Mileva, @Jana_Dittmann, @kraetzer, K. Lamshöft, @THB_Security_Research, L. Hartmann, J. Keller, @TN_THB and @niosat
Paper: https://dl.acm.org/doi/10.1145/3729165
#infosec #surveys #taxonomy #informationhiding #covertchannels #stego
There's supplemental material available (just scroll down on the linked page). It also features the description method for steganography techniques.
🔍 The hunt isn’t over.
The glitch still hides the key.
💀 If you thought you saw it all, think again.
The treasure remains… buried in plain sight.
🖼️ Check the box and decode the secret:
👉 https://x.com/TomsItCafe/status/1902645109155393701
#DeadSwitch #TreasureHunt #Steganography #DigitalMystery #DecodeTheSignal #InfosecChallenge #HiddenInPlainSight
@foone didn’t you recently touch on early computer graphics platforms that allowed software selection of NN colors out of a larger palette?
Asking because a 4 or 6 color variant of this could make rotating the palette turn what you wrote into Fuck This — color 3 near-black and color 4 near-white: the bottom 80% of the first o for a u, leftward fraction for a c, a color 4 spine and angled line added to the n for k. Then T, parts of the u and r for the h, with some color 4 for the rest. Then i, then most of the g, extending that tail alll the way back underneath.
#steganography in a sig.
🔍 The DeadSwitch Treasure Hunt Begins...
There’s a clue. A glitch. A whisper hidden in pixels.
🧠 If you can read between the noise, the path will reveal itself.
🕵️♂️ Follow the trail here:
👉 https://x.com/TomsItCafe/status/1901645567555473845
💀 The Ghost never knocks. The Ghost leaves signs.
#DeadSwitch #CyberGhost #TreasureHunt #Steganography #DigitalMystery
Steganography Explained: How XWorm Hides Inside Images — https://thehackernews.com/2025/03/steganography-explained-how-xworm-hides.html?m=1 #Cybercrime #Steganography #XWorm