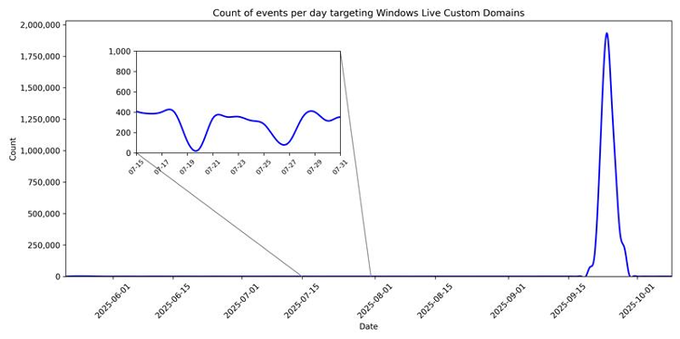
Since 14 October, we’ve tracked a high volume XWorm campaign targeting Germany. The activity is attributed to TA584, a sophisticated #cybercrime group tracked since 2020.
Messages are sent from hundreds of compromised sender accounts impersonating ELSTER and contain malicious URLs.
These URLs are either attacker-controlled URLs hosted on compromised websites, AWS-hosted URLs that redirect to those same sites, or unique Trend Micro click-time protection URLs that redirect to the AWS URLs. Proofpoint has notified Trend Micro about the potential abuse.
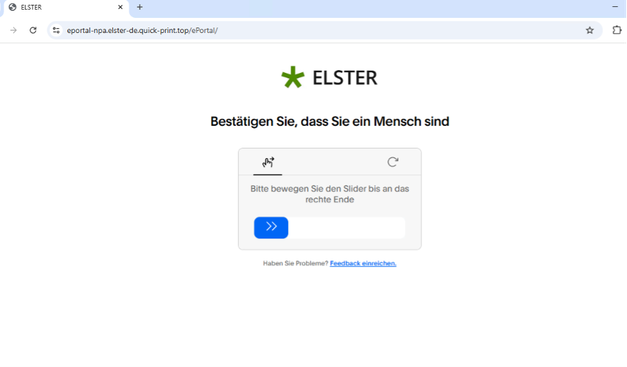
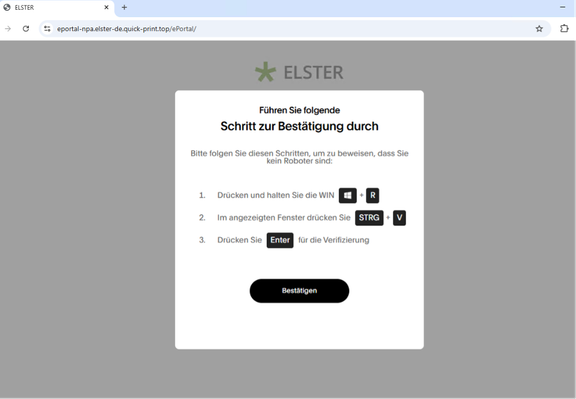
The compromised websites redirect the user to the attacker-controlled domain, which performs IP filtering. If passed, the visitor is redirected to the LP which contains a matching themed page with a "Slide" CAPTCHA. If the CAPTCHA is resolved, a ClickFix page guides users to follow instructions.
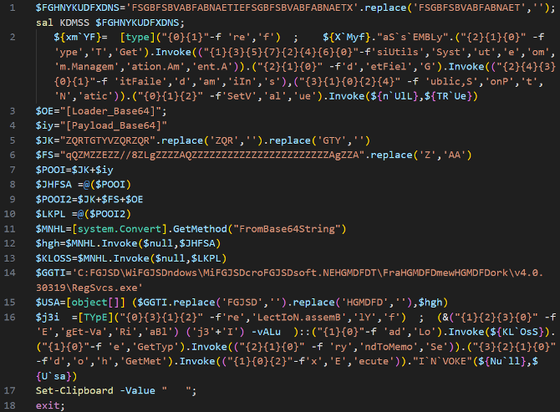
If the ClickFix instructions are followed, it will execute a remote PowerShell script that disables AMSI, loads a memory‑only .NET loader (included in the script) which injects an XWorm payload into RegSvcs.exe, clears the clipboard, and exits.
The user is redirected to a legit website if the ClickFix command is successful. This is done via server-side check (most likely based on IP) and response to post to https[:]//[InvolvedHostName][.]top/api/exe.
Proofpoint tracks this variant of XWorm as “P0WER” due to that is uses this string as AES Key. This variant always uses SharpHide for persistence by setting up a hidden registry key that will execute another remote PowerShell script on each boot to run XWorm again.
Proofpoint assesses TA584 is an initial access provider whose compromises can lead to #ransomware.
Historically, this actor focused on North America and the UK. TA584 expanded its targeting to include European entities including Germany since 1 July 2025.
---
Landing page: hxxps://www[.]eportal-npa[.]elster-de[.]quick-print[.]top/ePortal/ or hxxps://www[.]npa-eportal[.]digital-service[.]elster-de[.]status-drive[.]top/ePortal/
Click Payload: hxxp://94[.]159[.]113[.]37/ssd.png | b6956f45bd3c7b3009a31f0caf087d0686e60ee96978766a9f6477b8b093eace
XWorm C2: 85[.]208[.]84[.]208:4411
SharpHide Payload: 85[.]208[.]84[.]208/x.jpg