🔒 Verizon call log exposure was more than a bug—it was a real-time surveillance risk.
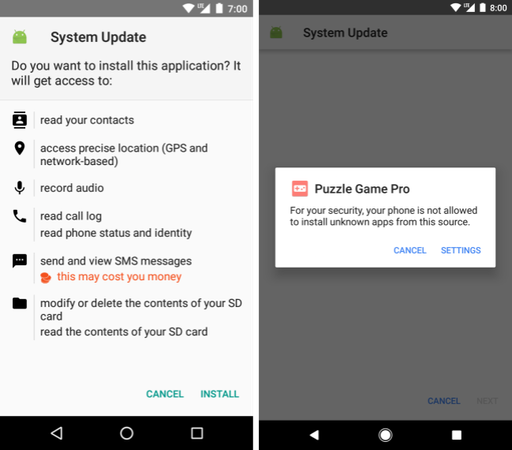
A serious flaw in Verizon’s pre-installed Call Filter iOS app allowed unauthorized access to detailed incoming call logs of any Verizon user.
Discovered by ethical hacker Evan Connelly in February and patched in March, the issue:
・📱Affected millions using the app to block spam and ID unknown numbers
・📂 Could have exposed call histories of journalists, law enforcement, and public officials
・🚨 Raised massive concerns around privacy and real-time surveillance
Verizon confirmed the fix, but experts stress this as a wake-up call for rigorous mobile app security—especially those preloaded at scale.
👉 https://www.newsweek.com/verizon-expose-customer-call-history-hack-2055247
#CyberSecurity #Verizon #PrivacyBreach #AppSecurity #Surveillance #DataProtection #EthicalHacking #MobileSecurity