Node Package Manager (NPM): Sicherheitsvorfall #Malware #Phishing #Cryptojacking #Supply Chain #TeamInfoSec #cyberangriff https://www.security-incidents.de/sicherheitsvorfaelle/sicherheitsvorfall-node-package-WW-10696.php
#Cryptojacking
⚠️ LunoBotnet: A modular Linux botnet with cryptomining + DDoS-for-hire.
✔️ Self-healing watchdogs
✔️ System binary replacement
✔️ Targets Roblox, Minecraft, Valve
✔️ Markets services via Telegram
Experts call it a criminal infrastructure platform for long-term monetization.
💬 How do you rate the detection difficulty here? Follow @technadu for analysis.
#Cyble #LunoBotnet #LinuxMalware #Cryptojacking #DDoS #Botnet #SelfHealing #Malware #CyberThreatIntel
Misconfigured Docker APIs are a hacker’s gateway to secret crypto-mining—thanks to Tor, stopping them is tougher than ever. Is your cloud truly secure?
https://thedefendopsdiaries.com/securing-docker-apis-navigating-the-threat-landscape/
#dockersecurity
#cybersecurity
#cloudsecurity
#cryptojacking
#tor
@anathema INHO #JavaScript should be outlawed for being the #1 source of #malware, #cryptojacking and escalation in #WastefulComputing!
Watch Out: A new malware hijacking Windows Character Map to mine #crypto on a targeted device, exposing risks of attacks in everyday software processes.
Read: https://hackread.com/new-malware-uses-windows-character-map-cryptomining/
#CyberSecurity #Malware #Cryptomining #Cryptojacking #Windows
🚨 First known obfuscated AutoIt loader used to deliver NBMiner via PowerShell + charmap.exe.
Experts warn cryptojacking = intrusion signal, not a nuisance.
Cyber crooks are hijacking cloud power to secretly mine crypto—one scam even racked up over $3.5M by posing as an educational platform. How safe is your data in the cloud?
https://thedefendopsdiaries.com/understanding-cryptojacking-a-growing-threat-in-cloud-computing/
#cryptojacking
#cloudsecurity
#cybercrime
#infosec
#cybersecurity
Tom’s Hardware: Hacker plants three strains of malware in a Steam Early Access game called Chemia — security company found crypto-jacking infostealers and a backdoor to install yet more malware in the future. “A cyber threat intelligence firm called Prodaft revealed that ‘Chemia,’ a game previously available via Steam’s Early Access program, shipped with three strains of malware.”
For those who don't know the size of the problem:
In 2006 I bought a new [entry level] Computer with 256 MB of RAM and a single-core P4 Celeron with 2,8 GHz.
This thing ran #WindowsXP and #NeedForSpeedMostWanted just fine.
Nowadays it would crash trying to open #Slack even on a minimalist #Linux distro like @bunsenlabs in @dillo, a lightweight browser ...
And now imagine that some folks have to use #Slack, #MicrosoftTeams, #Telegram, #Signal, #WhatApp, #WeChat, #QQ and #LineMessenger at the same time on their machine, and you can imagine that this will make entry-level desktops already scream harder than if someone were to loop the Lost Coast benchmark on them...
- The #bloat of modern #WebApps is just the socially accepted equivalent to #Cryptojacking desktops and driving some *phat #SuperUselessVehicle just to get less than a kg of groceries at a walking distance supermarket.
Everywhere else we'd not accept such a #bloatware IRL.
- So why should we accept #obscene|ly #WastefulComputing*?
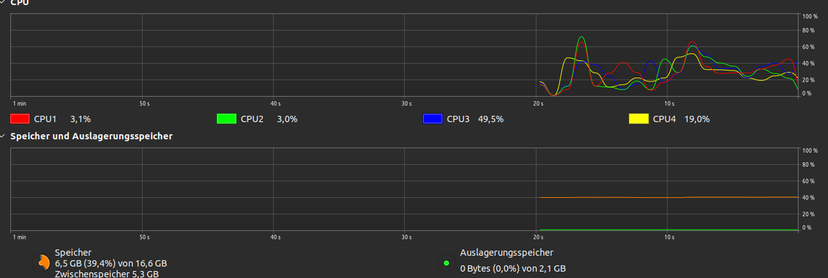
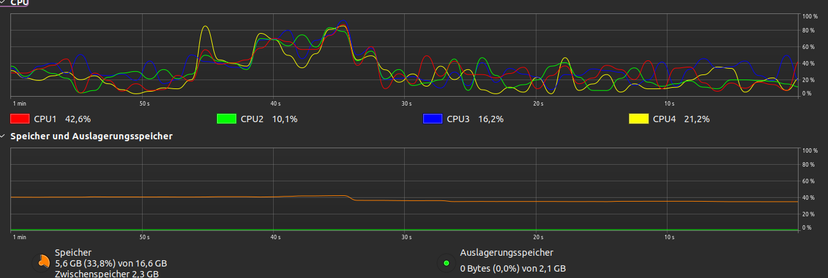
You know someone fucked up #WebDesign when logging out makes your CPU spike to 85% and the fan sound like one's running a #Shitcoin #Mining #Malware (aka. #Cryptojacker) and closing the tab results in 1 GB less RAM and 3 GB less overall cached assets.
- And yes I did check these results by running
sudo sh -c "sync; echo 3 > /proc/sys/vm/drop_caches"'before, during and after the website has been opened.
#Cryptojacking #ShitWebsite #Shitty #Enshittification #JavaScript #Malware #Miner #FuckedUpShit #FuckUp
@MxVerda I think #JavaScript is being.runed by the fact that it's being abused for #tracking & #cryptojacking #malware to the point that disabling it is a necessity!
@cR0w not really...
Obviously it's the #1 target and every #Skiddie has their own index of #WordPress sites waiting to deploy their #Cryptojacking #malware the second they get their hands on an exploit before people have patched it, but the same applies to #Windows (espechally #WindowsServer!) and other shitty applications...
@tjhexf personally, I hate #JavaScript because it's #ableist, bricks #accessibility and the only "cool" thing it has demonstrated is the abuseability for #tracking and #Cryptojacking #malware!
@cR0w @Dio9sys I bet you #skiddies gonna go #cryptojacking #Monero tonite...
@jonathankoren I'm just the kind of person who expects shit to work on #LynxBrowser over @torproject and if it doesn't then it's ableist trash IMHO.
Ukrainian Hacker Gets Arrested For Hacking 5,000 Accounts For Cryptojacking #bitcoin #cryptocurrency #cryptojacking #cryptomining #hacker
https://www.lowyat.net/2025/355126/ukrainian-hacker-cryptojacking/