Linux deepin 15.4 beta | Esthétique - Y'a du nouveau!
#Deepin
#Odysee - https://odysee.com/@switchedtolinux:0?view=content
#Rumble - https://rumble.com/c/SwitchedToLinux/videos
#Bitchute - https://www.bitchute.com/channel/uf9hzD216LX0
*Videos may take a considerable amount of time to post. If it is not present, it will be, soon(tm).
ALL HAIL THE VAN PANTHERS!!!
!!! NOTE !!! Switched To Linux is, “written by a broad spectrum computer consultant to help people learn more about the Linux platform.” This account is a supporter of @switchedtolinux and provides convenience posts of thumbnails art, videos and streams.
<<Posts may contain hashtags as content may pertain to many distributions and/or related material/topics. Posts may be reposted, boosted, shared, etc. by bots and/or other accounts and are done so at the discretion of the bots/accounts that perform those actions. This account is not responsible for the action(s) of those bots and/or accounts. Therefore, Offended Discretion is advised.>>
#SwitchedToLinux #Linux #Windows #Mac #AltTech #FOSS #YouTube #Odysee #Rumble #BitChute #Locals #DLive #Twitch #FactCheckTrue #Fediverse #Fedi22 #Fedi23 #Fedi24 #BigTech #OpenSUSE #Deepin
#Odysee - https://odysee.com/@switchedtolinux:0?view=content
#Rumble - https://rumble.com/c/SwitchedToLinux/videos
#Bitchute - https://www.bitchute.com/channel/uf9hzD216LX0
*Videos may take a considerable amount of time to post. If it is not present, it will be, soon(tm).
ALL HAIL THE VAN PANTHERS!!!
!!! NOTE !!! Switched To Linux is, “written by a broad spectrum computer consultant to help people learn more about the Linux platform.” This account is a supporter of @switchedtolinux@fosstodon.org and provides convenience posts of thumbnails art, videos and streams.
#SwitchedToLinux #Linux #Windows #Mac #AltTech #FOSS #YouTube #Odysee #Rumble #BitChute #Locals #DLive #Twitch #FactCheckTrue #Fediverse #Fedi22 #Fedi23 #Fedi24 #BigTech #OpenSUSE #Deepin
openSUSE ha deciso di escludere i pacchetti del desktop cinese Deepin per ragioni di sicurezza e poca trasparenza continua a leggere.....
#opensuse #deepin
https://www.miamammausalinux.org/2025/05/opensuse-ha-deciso-di-escludere-i-pacchetti-del-desktop-cinese-deepin-per-ragioni-di-sicurezza-e-poca-trasparenza/
openSUSE is dropping support for the Deepin Desktop Environment due to security concerns and bypassing of openSUSE's security review.
#openSUSE has removed Deepin Desktop from its repositories due to security concerns and maintenance issues, including a package that bypassed security protocols.
While users can still choose Deepin Desktop, openSUSE advises against it due to potential risks.
Stay updated on security news, upgrade your system, and avoid Deepin Desktop for now.
https://news.itsfoss.com/opensuse-deepin-desktop-removal/
#Deepin #Desktop #DeepinDesktop #Linux #Cybersecurity #Security #OpenSource #Freedom #Technology #TechNews #Tech
Removal of #deepin desktop from openSUSE due to packaging policy violation 👇🤔🧐
(I'm not a user of none of them, but it's interesting that the team of a distro opted for these actions on a software that was only suspicious because of its chinese origin)
https://security.opensuse.org/2025/05/07/deepin-desktop-removal.html
References:
openSUSE security Guide Lines for Packaging
#openSUSE #Linux #POSIX #OpenSource #programming
#Deepin #frightmare #Infosec #nightmare #elmStreet
https://en.opensuse.org/openSUSE:Package_security_guidelines#Audit_Bugs_for_the_Security_Team
🛑 Due to security policy violations and a packaging bypass, #openSUSE is removing the #Deepin #Desktop from Tumbleweed and Leap 16.0. Read the full story: https://linuxiac.com/opensuse-removes-deepin-desktop-over-security-policy-violations/
Don't run the #Deepin Linux desktop https://security.opensuse.org/2025/05/07/deepin-desktop-removal.html
@rl_dane
According to the openSUSE team the people were made perfectly aware of what they were circumventing; it was put in plain English.
What was not put in plain English is that because of the circumvention they were putting themselves in tremendous risk.
Consider taking two kg of Aurum four kg of Argentum jewelry putting them on your body and then just walking on the street wearing only those jewels, in a street where there are only ladrónes. You're just begging for trouble
#openSUSE #Linux #POSIX #OpenSource #programming
#Deepin #frightmare #Infosec #nightmare #elmStreet
For me reading this post took about 10 minutes since I not only read but I also processed and checked references and I tooted about it immediately
It is quite sobering to read something this horrific happening in an Open Source project of this magnitude of volume
This is something you would expect in closed source not open source; it's like a shower with 0° degrees Celsius of water flowing over you 0° in the depth of the coldest Siberian winter
#openSUSE #Linux #POSIX #OpenSource #programming
#Deepin #frightmare #Infosec #nightmare #elmStreet
This is where the depth of the deception became clear
>>
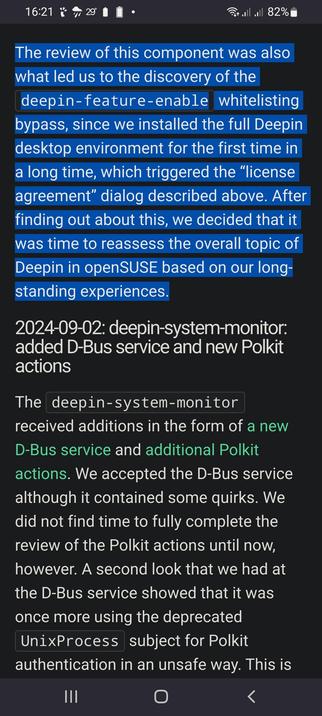
The review of this component was also what led us to the discovery of the deepin-feature-enable whitelisting bypass, since we installed the full Deepin desktop environment for the first time in a long time, which triggered the “license agreement” dialog described above. After finding out about this, we decided that it was time to reassess the overall topic of Deepin in openSUSE based on our long-standing experiences.
<<
#openSUSE #Linux #POSIX #OpenSource #programming
#Deepin #WTF #frightmare #Infosec #nightmare #elmStreet
This part I screen capped for accentuation
>>
2024-08-29: deepin-api-proxy: D-Bus Service
After a longer time of standstill regarding Deepin reviews, a request for the addition of deepin-api-proxy arrived. This package greeted us with over two dozen D-Bus configuration files. Again, upstream’s description of what the component is supposed to do was very terse. From looking at the implementation we deduced that the proxy component seems to be related to the renaming of interfaces described in the previous section.
We found a design flaw in the proxy’s design which allowed a local root exploit. You can find the details in a dedicated blog post we published about this not too long ago.
It is noteworthy that the communication with upstream proved very difficult during the coordinated disclosure process we started for this finding. We did not get timely responses, which nearly led us to a one-sided publication of the report, until upstream finally expressed their wish to follow coordinated disclosure at the very last moment.
<<
I now have really seen it all The Good the Bad and the Ugly in Open Source programming
#openSUSE #Linux #POSIX #OpenSource #programming
#Deepin #WTF #frightmare #Infosec #nightmare #elmStreet
More excerpts
>>
Sadly the review of deepin-app-services was another chaotic case, one that is actually still unfinished. Even understanding the purpose of this D-Bus service was difficult, because there wasn’t really any design documentation or purpose description of the component. From looking at the D-Bus service implementation, we judged that it is a kind of system wide configuration store for Deepin. Contrary to most other Deepin D-Bus services, this one is not running as root but as a dedicated unprivileged service user.
<<
This reads like a horror novel but it's actually happening! Unbelievable how this has harmed a distro with many dedicated users!
https://security.opensuse.org/2025/05/07/deepin-desktop-removal.html
#openSUSE #Linux #POSIX #OpenSource #programming
#Deepin #wtf #frightmare #Infosec #nightmare #elmStreet
The Deepin frightmare
Excerpt from linked site
>>
After reviewing the main D-Bus service, we could not help ourselves but call it a security nightmare. The service methods were not only unauthenticated and thus accessible to all users in the system, but the D-Bus configuration file also allowed anybody to own the D-Bus service path on the system bus, which could lead to impersonation of the daemon. Among other issues, the D-Bus service allowed anybody in the system to create arbitrary new UNIX groups, add arbitrary users to arbitrary groups, set arbitrary users’ Samba passwords or overwrite almost any file on the system by invoking mkfs on them as root, leading to data loss and denial-of-service. The daemon did contain some Polkit authentication code, but it was all found in unused code paths; to top it all off, this code used the deprecated UnixProcess Polkit subject in an unsafe way, which would make it vulnerable to race conditions allowing authentication bypass, if it had been used.
<<
¿WTF?
https://security.opensuse.org/2025/05/07/deepin-desktop-removal.html
#openSUSE #Linux #POSIX #OpenSource #programming
#Deepin #WTF #frightmare #Infosec #nightmare #elmStreet
”According to the #SUSE Security Team, though, DDE's beauty is only skin deep. Beneath the polished surface, it's not pretty at all. The team enumerates a whole list of problems, including claimed abuses of D-Bus and Polkit, but also some very poor design decisions. Some of these represent major security holes“
theregister.com: openSUSE deep sixes #Deepin desktop over security stink
https://www.theregister.com/2025/05/09/opensuse_ditches_deepin/
openSUSE removes Deepin Desktop after discovering a policy-violating workaround used to bypass required security reviews of sensitive system components.
https://linuxiac.com/opensuse-removes-deepin-desktop-over-security-policy-violations/
Yeah, it's interesting to think about:
When using software intentionally, you always have to be aware of who's generally in charge of the code. Who are also in charge of your data...
People are seemingly waking up from this fever dream of #enshitification and data tracking. Switching to #FOSS and even a different OS.
#Deepin does not seem like a trustworthy project, every time I've heard about it, something sketchy goes on, so it's a very bad example of FOSS :(