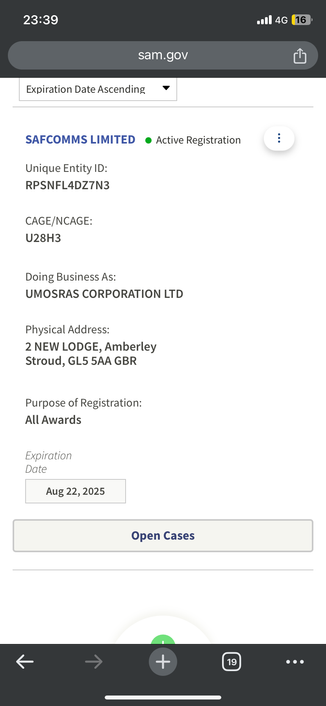
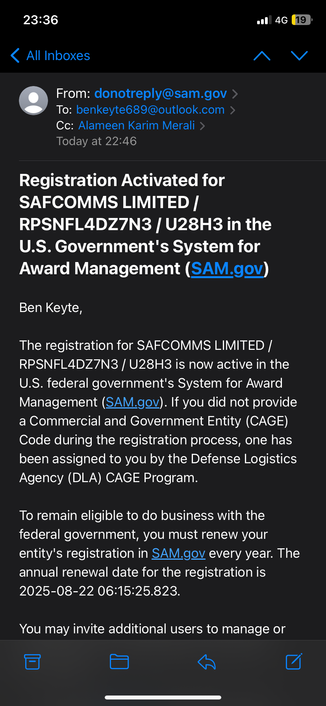
If I were @standupmaths , there would be some Terrible Python Code parsing the output of dnsqr and doing line fitting to the TTL values; and an entire video on how to estimate from such data how many real machines under the covers serve up some seemingly single service on the Internet, and a second channel one on how people did that from the Netcraft uptime graphs that it used to present a couple of decades ago.
And then a clever viewer switching from parsing text from a pipe to some proper Python DNS client library and achieving a 6283% speedup.
(-:
#DomainNameSystem #BendersTest #Python #TerriblePythonCode #StandUpMaths