Operation Endgame - Largest Ever Operation Against Botnets Hits Dropper Malware Ecosystem
Date: May 30, 2024
CVE: Not specified
Vulnerability Type: Malware
CWE: [[CWE-94]], [[CWE-502]]
Sources: Europol News, Eurojust News
Issue Summary
Europol, in coordination with law enforcement agencies from multiple countries, conducted the largest ever operation targeting botnets. This operation, dubbed "Operation Endgame," took place from May 27 to 29, 2024, and led to the disruption of major malware droppers including IcedID, SystemBC, Pikabot, Smokeloader, and Bumblebee. The effort resulted in four arrests and the takedown of over 100 servers worldwide. These droppers were used to facilitate ransomware and other cyber-attacks by installing additional malware onto target systems. The operation was supported by Eurojust and involved contributions from countries including France, Germany, the Netherlands, Denmark, the UK, the US, and others. Private partners also played a role in the operation, which aimed to dismantle the infrastructure supporting these malicious activities. The success of this operation marks a significant step in combating cybercrime on a global scale.
Operation Endgame, coordinated by Europol, dismantled several major botnets including IcedID, SystemBC, Pikabot, Smokeloader, and Bumblebee. This international effort involved law enforcement agencies from multiple countries and led to the arrest of four individuals and the takedown of over 100 servers. The botnets targeted facilitated ransomware and other cyber-attacks.
Technical Key Findings
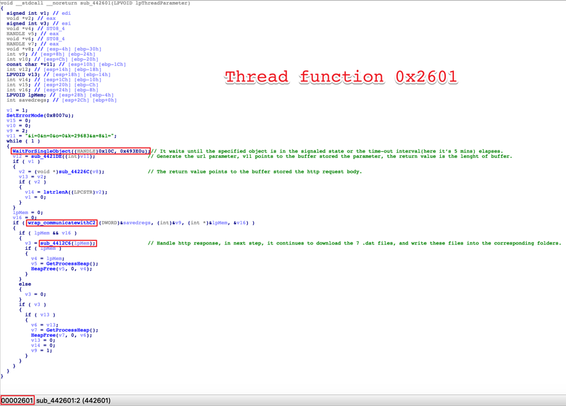
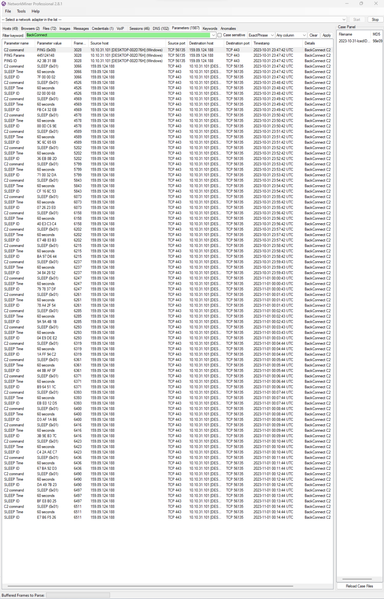
The malware droppers involved are designed to infiltrate systems and install additional malware, often avoiding detection through sophisticated evasion techniques. These droppers were used to deploy ransomware and other malicious payloads by bypassing security measures and enabling further system compromises.
Vulnerable Products
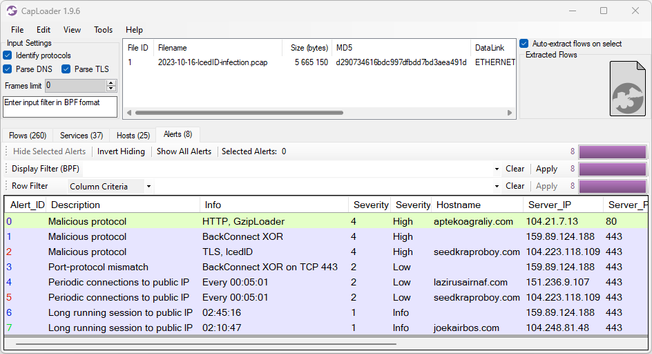
The operation did not specify particular products but targeted the infrastructures supporting droppers like IcedID, SystemBC, Pikabot, Smokeloader, and Bumblebee.
Impact Assessment
If abused, these vulnerabilities could lead to widespread ransomware attacks, financial losses, and significant disruption of services. The infrastructure taken down had facilitated numerous cyber-attacks globally, highlighting the severe impact on cybersecurity.
Patches or Workaround
The report did not mention specific patches or workarounds. However, continuous monitoring and updating of security measures are recommended to protect against such threats.
Tags
#Botnets #Malware #Ransomware #Cybersecurity #Europol #OperationEndgame #Cybercrime #IcedID #SystemBC #Pikabot #Smokeloader #Bumblebee