.NET Multi-Stage Malware Loader Target Windows Systems
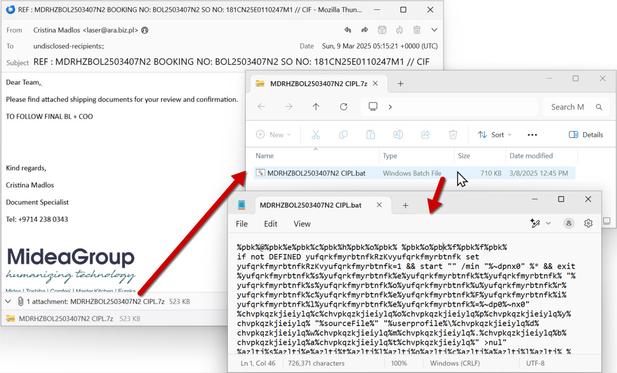
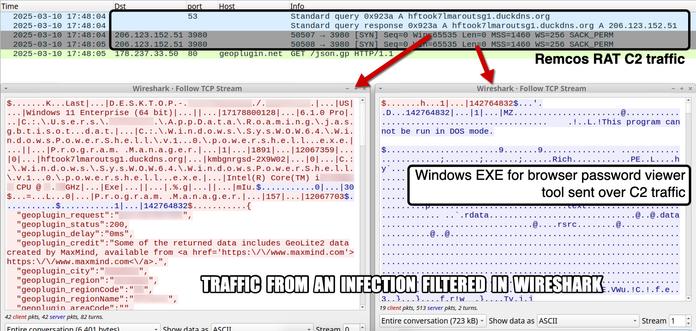
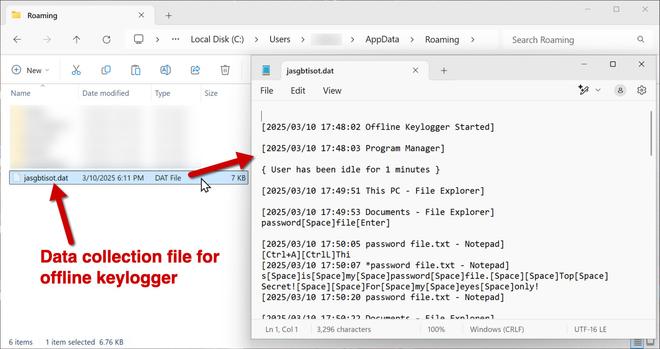
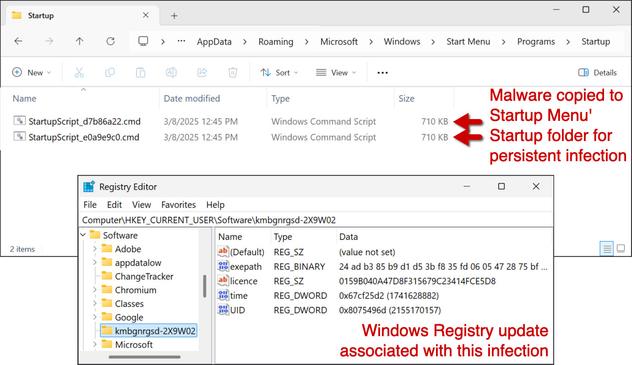
.NET-based multi-stage malware loader is identified to be targeting windows systems. It serves as a delivery system for a variety of harmful payloads, such as keyloggers (404Keylogger), remote access trojans (Remcos), and information thieves (AgentTesla and Formbook).
Pulse ID: 68292784661d61913074fa2d
Pulse Link: https://otx.alienvault.com/pulse/68292784661d61913074fa2d
Pulse Author: cryptocti
Created: 2025-05-18 00:19:16
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#CyberSecurity #FormBook #InfoSec #KeyLogger #Malware #NET #OTX #OpenThreatExchange #Remcos #RemoteAccessTrojan #Tesla #Trojan #Windows #bot #cryptocti