Breaking threat alert from DigitalOcean and Microsoft Azure! Mass exploitation campaign detected by actor codenamed Goofy Khaki Flamecrest. Find out about the 4 key events that characterized the campaign 👇
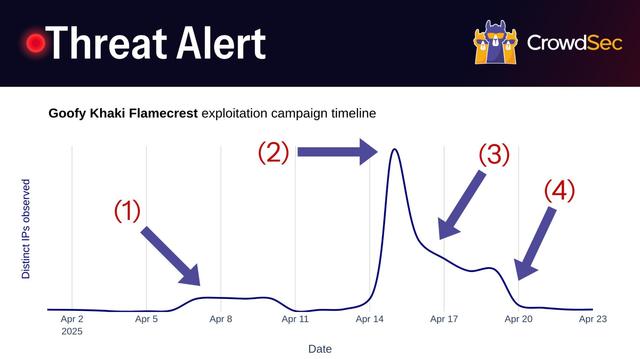
On the 15th of April, we detected a coordinated exploitation effort that included over 1,300 machines at its peak. The machines were small to medium-sized VPCs in public clouds such as Microsoft Azure and DigitalOcean. Using our comprehensive threat intelligence data, we were able to get a clear view of the exploitation campaign.
🔥Campaign Timeline:
The campaign timeline can be divided into 4 key sections:
1. 8th of April: The attacker launches a small-scale reconnaissance campaign using ~100 rented machines from a small Indonesian-based company. The reconnaissance involves exploits such as CVE-2021-41773 and CVE-2021-42013 for Apache Server to find vulnerable web servers.
2. 13th of April: The attacker kicks off the attack and delivers payloads using the previously used machines. The attack self-propagates as captured machines quickly start infecting other machines. At the peak of the two-day campaign, CrowdSec observed around 1,300 IPs from a broad range of server providers.
3. 16th of April: On the 3rd day of the campaign, the first cloud provider steps in with remediation. Microsoft Azure takes down all infected machines in direct action, dropping around ~400 machines from the network. Other server providers follow suit over the next few days.
4. 20th of April: DigitalOcean, the last remaining big provider, stops the propagation of Goofy Khaki Flamecrest on its servers. The attack gradually fades, leaving roughly 20 machines from various smaller Autonomous Systems operational.
💡 Further Information
🔹The most aggressive IPs involved in Goofy Khaki Flamecrest can be tracked using the CrowdSec CTI: https://app.crowdsec.net/cti?q=classifications.classifications.label%3A"Attacker+Group%3A+goofy+khaki+flamecrest"+AND+(reputation%3Amalicious+OR+reputation%3Asuspicious+OR+reputation%3Aknown)&page=1
🔹At the time of the detection, about 50% of the IPs involved in the attack were flagged as malicious in our Threat Intelligence database.
🔹The attack shows that fast response by VPC providers is an important metric to track. The longer affected machines stay online, the more opportunities arise to propagate the attack. Smaller MSSPs are especially vulnerable, as a failure to act can result in their IP ranges being blocked by other providers.
✅ Keeping tabs:
If you are an MSSP looking to get ahead of even Microsoft in taking down infected machines, you can inquire our sales team about Am I Attacking, a bespoke service where we proactively monitor your IP ranges to alert you if one of your machines starts showing up on our radar: https://crowdsec.net/business-requests?utm_source=mastodon&utm_medium=social&utm_campaign=threat-alert-250425
#cybersecurity #cohortattack #threaintel #opensourcesecurity #infosec #zeroday #blueteam