Aviation weather for Santa Ana Del Yacuma airport (Bolivia) is “SLSA 041100Z 12004KT 9999 SCT004 SCT070 25/24 Q1013” : See what it means on https://www.bigorre.org/aero/meteo/slsa/en #santaanadelyacuma #bolivia #santaanadelyacumaairport #slsa #sbl #metar #aviation #aviationweather #avgeek vl
#SLSA
Tomorrow I'm speaking at the Auckland Kubernetes Meetup.
Alongside Jonas, who is talking about "AI Assisted DevSecOps", I'm talking about "Secure software supply chain with Sigstore".
https://www.meetup.com/auckland-kubernetes/events/305896235/
Hope to see you there!
Join Harsh Thakur (Civo) & Saiyam Pathak (Loft Labs) as they talk about practical steps for achieving #SLSA compliance:
✔️ Generating SBOMs & provenance
✔️ Keyless attestations with cosign
✔️ Hermetic builds with Buildkit
📍 #SOSSCommunity Day India
Wondering whether users of #cosign (by #sigstore) and #slsa (slsa-verifier) would have opinions on how to best make use of these verification tools when downloading binaries for use in container images?
I started a StackOverflow discussion here with more details, since I'm new to playing around with these toolchains:
My #OSHcamp presentation for those struggling with the screen https://www.slideshare.net/slideshow/showing-that-you-care-about-security-for-your-open-source-hardware-project/271275092
@dolmen Many systems are based on #bootstrapping and #reproducableBuilds
• https://bootstrappable.org/
• https://reproducible-builds.org/
• https://en.wikipedia.org/wiki/Bootstrapping_(compilers)
These ensure that the build system integrity cannot be tampered with. One example of such system is https://openbuildservice.org/
Here's a great read on the topic from #SUSE : https://documentation.suse.com/sbp/server-linux/html/SBP-SLSA4/
Generally Supply-chain Levels for Software Artifacts (#SLSA) framework is a great resource on this topic: https://slsa.dev/ #cybersecurity #infosec
slsa-github-generator v2 now uses upload/download-artifact v4, so I can update those in all the Pallets projects. Turns out the publish workflow for most projects didn't need any changes at all. Only MarkupSafe, with multiple build jobs, needed a little change to use different upload names and combine their downloads. https://github.com/pallets/markupsafe/commit/f4905079ef7573d5c1e8fe1f291f1e353050bc87 #Python #Flask #MarkupSafe #GitHub #SLSA
To explain, we have #SLSA signatures that verify the build was done automatically by #GitHub as instructed, *and* we have traditional #gpg signatures with private keys only known to maintainer(s) that verify a maintainer actually triggered the built and locally reproduced it…
Given they both validate, you automatically achieve reproducible builds _and_ #SLSA validity.
One caveat: This was only easy, because our build process is essentially one command (git archive).
https://github.com/PrivateBin/PrivateBin/blob/master/doc/Release.md
The way this works, is, essentially, quite easy: the whole build process is documented in the same repository, builds are automated via CI/CD and all that is, to reach best support, done in an environment that prevents tampering and (crucially) is *out of your control*.
Then you get #SLSA v3: https://slsa.dev/get-started#slsa-3 (quite easy with GitHub Actions)
Note on all the #xz drama, there are some technical solutions for such #supplychainattack that can make such an attack way harder, at least to hide the code in tarballs etc.
https://slsa.dev/ e.g. is a solution. Combined with reproducible builds, it ensures that a software artifact is built exactly from the source given in a source repository, with the possibility to prove that and no way for any maintainer to tamper with (in the highest level).
I've decided to try my hand at speaking at IT Security conferences: I've got one rejected CFP so far, but today I proposed another for BSides Boulder:
"Preventing SolarWinds 2.0: #SLSA isn't gonna save you".
#Adoptium has finalised the releases of the January #Temurin #openjdk updates - jdk 8u402, 11.0.22, 17.0.10 and 21.0.2.
This is the first JDK21 release to include AIX and Linux/s390x platforms, and the release is #SLSA build level 3 compliant on Linux and macOS platforms.
https://adoptium.net/blog/2024/01/eclipse-temurin-8u402-11022-1710-and-2102-available/
Beach safety for humans in a more-than-human world
Have drones at the beach, repel birds
Beachgoers are warned with larges signs of a drone operating at Sawtell beach. The warning posters for the aerial operations states that they have the rationale to keep human beings safe. The unmanned aerial vehicle makes an irritating buzzing sound while flying over the heads of beachgoers.
The beauty of Sawtell beach is usually to share the ambience with shorebirds, birds of prey and little terns. With the loud gadget droning up and down the beach no bird or endangered shorebird was visible or audible. The scarecrow in the sky, the jet skis and car on the sand make sure the beach is just for one species alone.
Drones are disturbing critically endangered shorebirds in Moreton Bay, creating a domino effect
https://theconversation.com/drones-are-disturbing-critically-endangered-shorebirds-in-moreton-bay-creating-a-domino-effect-209391
Human safety, The Civil Aviation Safety Authority
https://www.casa.gov.au/knowyourdrone
Sawtell - Threatened Shorebirds. The Threatened Shorebirds program shares the plight of these incredible shorebirds, including Little terns, Pied oyster catchers and Beach stone curlews
https://www.coffsharbour.nsw.gov.au/Eventbrite/Threatened-Shorebirds-767985383957
#Sawtell #SawtellBeach #UAVs #regulation #drones #gadgets #CASA #SLSA #SurfLifeSaving #safety #IndustrialisedBeaches #birds #Shorebirds #ThreatenedShorebirds #wildlife #ShareTheBeach
If I could pick one software supply chain security thing for people to look at in the new year, it would be the Secure Supply Chain Consumption Framework. It describes in detail how to manage risk associated with software dependencies.
I consider this more important than SBOMs or SLSA.
Check it out! https://github.com/ossf/s2c2f
#SLSA: #Macaron is an extensible supply chain security analysis framework from Oracle which integrates with existing #SBOM in OWASP #CycloneDX
My colleague Scott Fryer gave a talk at this year's @EclipseFdn 's #EclipseCon on #Adoptium's secure development practices, what we've done and what we're going to do going forward. It covers #SLSA, #SSDF, #SBoM, binary #reproducibleBuilds and keeping a heterogeneous #openSource project's infrastructure secure with #Wazuh
If some of those buzzwords have piqued your interest (or you want to know what they are) checkout his video: https://www.youtube.com/watch?v=mpEKUnX84UQ
#secureDev #CycloneDX
Highlights from our SLSA Tech Talk 💃 + additional Q&As we didn't have time for during the live session & where to watch on demand: https://openssf.org/blog/2023/10/20/slsa-tech-talk-highlights/ Securing the Software Supply Chain: An In-Depth Exploration of #SLSA
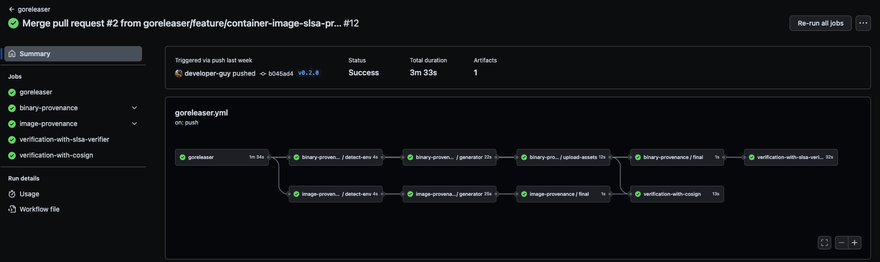
🚀 Exciting News! We've just released a new blog post!
📝 In this article, we explore the world of software supply chain security, offering insights into how to safeguard the integrity of your binaries and container images using two powerful tools! ⚡️
💃 Dive into the capabilities of SLSA provenances for enhanced security.💻
👏 A big shoutout to @furkanturkaI and @caarlos0 for their invaluable contributions!
https://goreleaser.com/blog/slsa-generation-for-your-artifacts/
#SLSA #DevSecOps #OpenSource #goreleaser #slsaverifier #cosign 🌟
🎉 Incredible news! 🚀 I've successfully generated #SLSA provenance for binaries and container images via @GoReleaser and slsa-github-generators. 📦🔒 Thrilled to showcase this achievement! 🙌 #OpenSource #Security