#SmtpSmuggling
notqmail is the collaborative Open Source successor to qmail and netqmail. It begins with stable, compatible, small releases to which existing qmail users can safely update, and aims to become a more extensible, more easily packaged, and more modern Mail Transport Agent suitable for most needs.
qmail's design principles haven't _always_ prevented bugs or holes, nor have they _always_ made adding new functionality easy. But pretty often we get both. And that's why we continue to invest in this codebase.
Project goals that have made particular progress in the 1.09 release:
- Preserve qmail's hard-earned security properties
- Reduce marginal cost of development
- Make packaging easier
- Provide sensible defaults
Some well-known patches have been merged; others will need some adjustment.
Full release notes: https://notqmail.org/releases/1.09
It's been almost four years since 1.08. Thanks for your patience. With continued focus on making development safer and faster, our next release will arrive much sooner. Feedback welcome, as always.
#email #selfhosting #qmail #netqmail #notqmail #smtp #smtpsmuggling #mailserver
Pour le détail technique du SMTP Smuggling : https://smtpsmuggling.com/
Et l'excellente présentation au CCC en décembre dernier : https://media.ccc.de/v/37c3-11782-smtp_smuggling_spoofing_e-mails_worldwide
🏆 Achievement unlocked : être crédité comme "Reporter" sur un advisory de sécurité Github 🔒
https://github.com/postalserver/postal/security/advisories/GHSA-j42r-6c99-hqf2
👏 to @login for all the hard work
Only noticed today that there's a new long-term fix for #smtpsmuggling in #postfix for versions ≥ 3.5.24 using “smtpd_forbid_bare_newline = normalize”. The old “yes” setting for this option is now an alias for the new “normalize”. Also took some time for extended #smtpsmuggling testing using the “SMTP-Smuggling-Tools” from https://github.com/The-Login/SMTP-Smuggling-Tools.
Timo Longin @login introduces SMTP smuggling, a novel technique to spoof fully SPF-validated emails from various popular domains including @microsoft.com.
Wow. It's incredible nobody found this before. It's the first of its kind. Probably not the last...!
Related:
https://media.ccc.de/v/37c3-11782-smtp_smuggling_spoofing_e-mails_worldwide
https://www.postfix.org/smtp-smuggling.html
https://www.malwarebytes.com/blog/news/2024/01/explained-smtp-smuggling
#SmtpSmuggling #37C3 #SMTP #vulnerability #infosec #TimoLongin #security
It's a wrap! 🌯 Our technical guideline "BSI TR-03108 (Secure Email Transport)" is now accompanied by "BSI TR-03182 (Email Authentication)" providing guidance for email services to protect their users against impersonation attacks like Spoofing and Phishing :flan_mask:
https://bsi.bund.de/dok/tr-03182-en
#TeamBSI #EmailAuthentication #DNSSEC #DMARC #DKIM #SPF #SMTP #SMTPSmuggling
Finally the two missing options against #smtpsmuggling arrived in #debian buster this morning.
https://security-tracker.debian.org/tracker/CVE-2023-51764
smtpd_forbid_bare_newline = normalize
and if needed:
smtpd_forbid_bare_newline_exclusions = $mynetworks
see
SPF-valid spoofed mail from admin@microsoft.com 😈 ?
Timo Longin @login stumbled upon SMTP Smuggling while looking for vulnerabilities in the Simple Mail Transfer Protocol.
Great work and great talk!
#Smtp #SmtpSmuggling #TimoLongin #37c3
https://media.ccc.de/v/37c3-11782-smtp_smuggling_spoofing_e-mails_worldwide
Ich: »Ich habe gerade mal getestet, ob Ihr für #SmtpSmuggling anfällig seid, aber anscheinend kann ich auch einfach so Mails als jeder beliebige Absender über Eure Server verschicken.«
Mail-Provider: »Ja, das ist ganz normales Phishing, aber das ist so gewollt, damit man mit mehreren Absendern dasselbe Sammelpostfach bedienen kann.«
Ich: »Es ist gewollt, dass ich mich als Ihr oder jeder Eurer anderen Kunden ausgeben kann? Inklusive gültiger DKIM-Signatur?«
Mail-Provider: 🤷♂️
Es gibt so Tage...
@ParadeGrotesque
The patch for CVE-2023-51766, #SMTPSmuggling in Exim4, just landed in Debian.
https://security-tracker.debian.org/tracker/source-package/exim4
Możliwy atak SMTP Smuggling na popularne serwery pocztowe
Tim Longin, znany z ataków na protokół DNS, we współpracy z SEC Consult, opublikował informację o możliwości ataku SMPT Smuggling na popularne serwery i usługi pocztowe. Cała historia rozpoczyna się w czerwcu 2023 roku, kiedy to przedstawiono pierwszy PoC (Proof of Concept) ataku SMPT Smuggling działającego w systemie pocztowym firmy...
#Aktualności #Atak #Smtp #SmtpSmuggling
https://sekurak.pl/mozliwy-atak-smtp-smuggling-na-popularne-serwery-pocztowe/
#smtpsmuggling ... Zumindest für #Debian #Bullseye ist die gefixte #postfix 3.5.23 in den Repos...
Long planned, but now with enhanced motivation due to #SMTPSmuggling attack I finally replaced my old #EMailServer based on #Postfix and applied the workarounds.
Beside that I completely replaced the server hardware and all the VMs for Calendar, Files and Web (last one still WIP).
🔗 https://sec-consult.com/blog/detail/smtp-smuggling-spoofing-e-mails-worldwide/
🔗 https://media.ccc.de/v/37c3-11782-smtp_smuggling_spoofing_e-mails_worldwide
Neue Lücke in altem E-Mail-Protokoll: #SMTP smuggling | Security https://www.heise.de/news/Neue-Luecke-in-altem-E-Mail-Protokoll-SMTP-smuggling-9584467.html #SMTPsmuggling
@ParadeGrotesque
The patch for #SMTPSmuggling just landed in Debian Bullseye:
* 3.5.23 (Closes: #1059230)
- Addresses CVE-2023-51764, requires configuration change
- Security: with "smtpd_forbid_bare_newline = yes" (default "no" for Postfix < 3.9), reply with "Error: bare <LF> received" and disconnect when an SMTP client sends a line ending in <LF>, violating the RFC 5321 requirement that lines must end in <CR><LF>. This prevents SMTP smuggling attacks that target ...
https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=1059230
@Daojoan In order for this to be a truly viable reality, the FOSS community needs to massively step up their code privacy, security, and reliability practices. The average user cannot be put into the position of self-hosting insecure software without risking disaster.
Are you aware of the recent #SMTPSmuggling revelation scandal? That is the future to which you would doom everyone.
#SMTPSmuggling – Spoofing E-Mails Worldwide https://media.ccc.de/v/37c3-11782-smtp_smuggling_spoofing_e-mails_worldwide
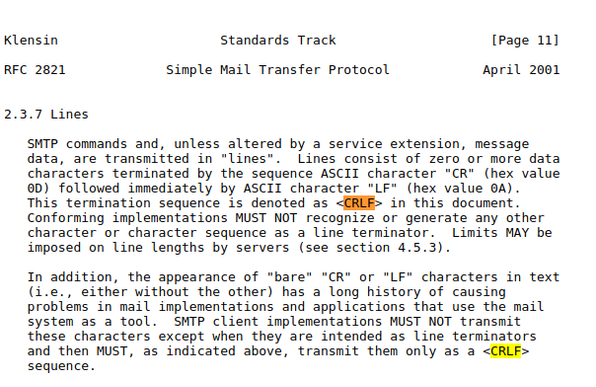
Prescient words from RFC 2821, "Simple Mail Transfer Protocol". #smtpsmuggling https://www.ietf.org/rfc/rfc2821.txt
So, all in all, the whole #smtpsmuggling issue was based on clear-text protocols and servers/OSes that handle line ends differently? wow.. makes me even more a fan of binary protocols
#37c3
https://fahrplan.events.ccc.de/congress/2023/fahrplan/events/11782.html