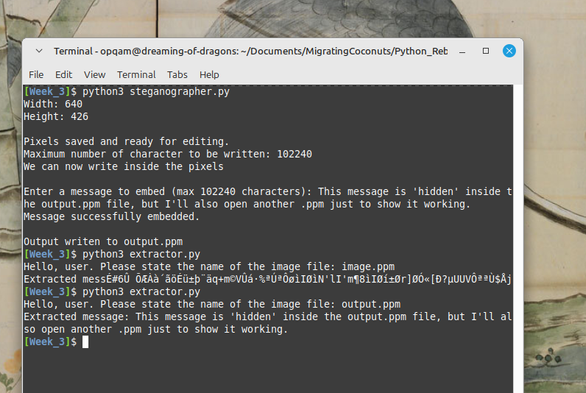
More Steganography!
A malicious Excel file using steganography was analyzed, revealing embedded XLS sheets and a complex infection chain. The file downloads an HTA file that creates a BAT file, which in turn generates and executes a VBS file. The VBS file fetches a VBA script that creates and runs a PowerShell script. The PowerShell script downloads an image containing a hidden payload delimited by specific tags. The payload is a Base64-encoded PE file, which is decoded and executed as a DLL. The final payload appears to be a Katz stealer. This analysis highlights the use of multiple file types and steganography techniques to evade detection.
Pulse ID: 684da8c81baecf48b68eb91e
Pulse Link: https://otx.alienvault.com/pulse/684da8c81baecf48b68eb91e
Pulse Author: AlienVault
Created: 2025-06-14 16:52:24
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#CyberSecurity #Excel #InfoSec #OTX #OpenThreatExchange #PowerShell #RAT #Steganography #VBS #bot #AlienVault