# Evolving Our Tor Relay Security Architecture
https://blog.emeraldonion.org/evolving-our-tor-relay-security-architecture
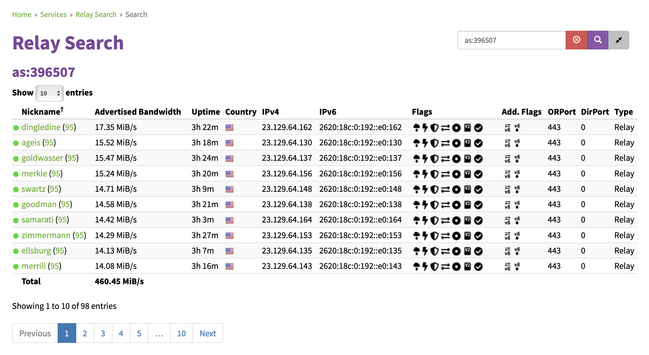
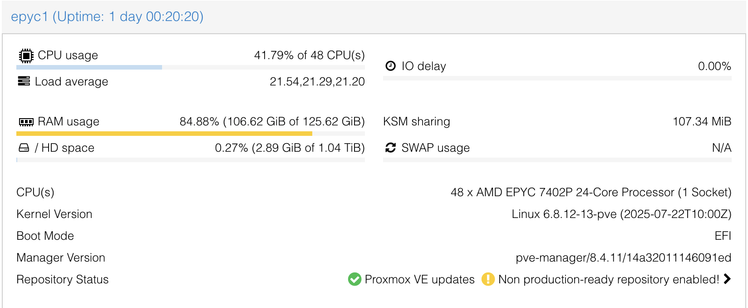
A new blog post where @alexhaydock goes into some detail showcasing our minimalistic @alpinelinux Tor relays architecture, a threat model, and including a link to our now-public open source "Emerald Relays" orchestration framework.
The past 6 months have proven its success, and now we look forward to phase 2 (read the post!), which we need your help in funding. Emerald Onion is a U.S. 501(c)(3) tax-deductible nonprofit, so please consider donating before 31 December! https://emeraldonion.org/donate/
#Tor #TorOps #Privacy #AntiCensorship #Anonymity #Ansible #Proxmox #Terraform #AMD #Epyc #SEVSNP #NonProfit #GivingTuesday