#collaborative #shahai by Arvinder Kaur @arvinderk8 ( #monoku )and Pratham S. S. Jolly ( #photo ). #hope #poetry #photography #micropoetry #blackandwhite #sepia #poetrylovers #photographylovers #haiku #India #milkyway
#collaborative
16% of proven-aggressive IPs CrowdSec blocks are still unknown to other vendors for 15 to 20 days. 👀
🗓️ That’s over two weeks where you’re protected while others remain exposed.
How do we do it?
#CrowdSec leverages a #collaborative network of thousands of contributors worldwide, enabling us to detect and block malicious behavior before it becomes common knowledge.
Learn more 👉 https://crowdsec.net/blocklists
#collaborative #shahai with #haiku by Hifsa Ashraf @hifsays and Oscar Luparia #poetry #poetrycommunity #whispers #poetrylovers #micropoetry #photography #sky #poem #clouds #photo #photooftheday #photographylovers #pakistan
#collaborative #shahai with #haiku by Hifsa Ashraf @hifsays and Oscar Luparia #poetry #poetrycommunity #whispers #poetrylovers #micropoetry #photography #sky #poem #clouds #photo #photooftheday #photographylovers #pakistan
Free download codes:
The Missing Note - et cetera
"A multi-genre album of Post-Everything"
Get 7 to 60 days ahead of #attacks. ⚡
⏳ When malicious IPs hit the internet, every second counts.
#CrowdSec gives you the upper hand by identifying and blocking malicious IPs days to even weeks before any other vendor on the market.
How? Our real-time #collaborative network of thousands of contributors feeds into our blocklists, resulting in early, accurate, and actionable #IP intelligence.
Learn more 👉 https://www.crowdsec.net/blocklists
Free download codes:
Zone-440 - Inverted Waves (LB)
"Exponential Growth; We shape our tools and then our tools shape us."
#experimental #edm #chiptune #collaborative #goldbox #concept #jummbox #beepbox #ultrabox #music
here we go, here we go! https://codeberg.org/caranmegil/theshard
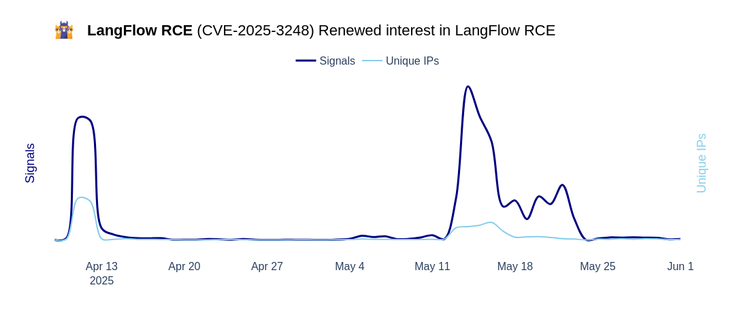
🚨 CVE-2025-3248: Renewed Interest in Langflow Remote Code Execution
ℹ️ About the exploit:
#Langflow is a widely used #opensource library for building AI agents, backed by corporate support from #Datastax (now #IBM). The tool provides a web-based, drag-and-drop interface for creating agentic workflows, making it particularly attractive to businesses, but also a high-value target for exploits. Given that such workflows often integrate with critical business databases and tools, security vulnerabilities in Langflow could have severe consequences.
This risk is not hypothetical. Langchain, another leading AI framework, has already been associated with over 30 CVEs, underscoring the security challenges in the fast-moving LLM development ecosystem.
The vulnerability in Langflow allowed unauthenticated attackers to execute arbitrary code on the host machine. Discovered and disclosed by Horizon3 in late February, the issue was patched in version 1.3, released at the end of March. Below is a detailed timeline of the discovery and remediation process.
🔎 Trend analysis:
🔹 Feb 25, 2025: The vulnerability is disclosed to DataStax by Horizon3.
🔹 Mar 5, 2025: DataStax fixes the vulnerability in the development branch.
🔹 Mar 31, 2025: Langflow 1.3.0 releases, containing a fix for CVE-2025-3248.
🔹 April 7, 2025: CVE-2025-3248 is published to the NVD.
🔹 April 9, 2025: The exploit is leaked to the public, and the CrowdSec Network starts tracking the exploit.
🔹 April 11-12, 2025: The CrowdSec Network observes a first wave of exploitation attempts by approximately 200 machines.
🔹 April 12 - May 14, 2025: Attackers disappear, with barely any attacks registered in the CrowdSec Network.
🔹 May 14 - 23, 2025: The CrowdSec Network observes a renewed, smaller wave of attacks, peaking out at around 100 involved machines.
✅ How to protect your systems:
🔹Patch: If you haven’t already, ensure your publicly exposed Langflow instance is updated with the latest patch.
🔹Preemptive blocking: Use Crowdsec CTI to block IPs exploiting CVE-2025-3248 👉 https://app.crowdsec.net/cti?q=cves%3ACVE-2025-3248
🔹Stay proactive: Install the Crowdsec Web Application Firewall to stay ahead of exploit attempts with 100+ virtual patching rules available 👉 https://app.crowdsec.net/cti?q=cves%3ACVE-2025-3248
Sharing insights and taking swift action can collectively reduce the impact of these threats. This is your call to action for real-time threat intelligence and #collaborative #cybersecurity 👉 http://crowdsec.net/
///From Seed to Humus///
Here is the video presentation of our association, recently posted online.
From Seed to Humus offers open, free and collaborative resources to move towards a sustainable development more in harmony with our environment.
https://tube.hoga.fr/w/1YVU4o4cS1d82PCnKmG2bM
#video #presentation #seed_to_humus #resources #libre #free #collaborative #environment #social
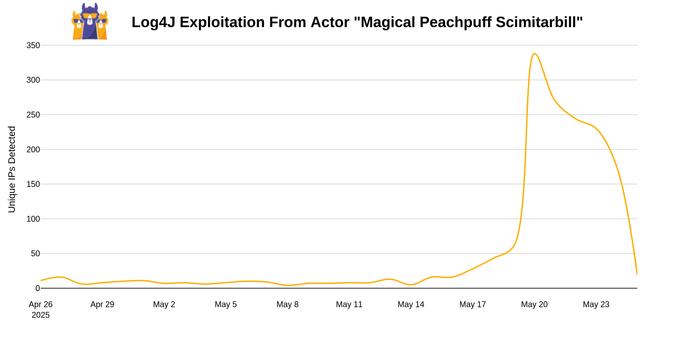
🚨 Rapid surge in Log4j scanning campaigns (CVE-2021-44228) detected!
4 Years after the exploit was first published, the CrowdSec Network still detects active campaigns targeting the Log4Shell class of exploits.
ℹ️ About the exploit:
The Log4j exploit, a famous remote code execution issue in a popular Apache logging library, ruined Christmas festivities for most security teams in 2021. Nowadays, this exploit is still abused by small-time hacker groups looking to find easy targets to launch more dangerous exploits from.
🔎 Trend analysis:
🔹20th of May: The CrowdSec network detects a rapid surge in machines targeting CVE-2021-44228, with over 95% of machines originating from DigitalOcean, a VPS provider. The group is assigned a tag, “Magical Peachpuff Scimitarbill” by the CrowdSec monitoring service.
🔹20th - 24th of May: Within 4 days, the campaign targets over 1000 machines connected to the CrowdSec network with a diverse selection of exploits targeting popular open source applications such as CVE-2021-41773 (Apache Server) or CVE-2021-43798 (Grafana).
🔹25th of May: The machines disappear, presumably due to intervention from DigitalOcean.
✅ How to protect your systems:
🔹Stay informed: Use Crowdsec CTI to explore IPs used for the campaign 👉 https://app.crowdsec.net/cti?q=classifications.classifications.label%3A%22Attacker+Group%3A+magical+peachpuff+scimitarbill%22&page=1
🔹Stay proactive: Install Crowdsec Web Application Firewall to stay ahead of exploit attempts with 100+ virtual patching rules available 👉 https://doc.crowdsec.net/docs/next/appsec/intro/
Sharing insights and taking swift action can collectively reduce the impact of these threats. This is your call to action for real-time threat intelligence and #collaborative #cybersecurity 👉 http://crowdsec.net/
Collaborative Text Editing Without CRDTs or OT
https://mattweidner.com/2025/05/21/text-without-crdts.html
#HackerNews #Collaborative #Text #Editing #CRDTs #OT #Technology #Innovation
See parts and instructions here → https://ikego.world/products/clothing/bounce/
#sustainable #modular
„Bounce↑↓“ #circular #open #customizable #collaborative #shoes
See parts and instructions here → https://ikego.world/products/clothing/bounce/
#collaborative #shahai with #haiku by Hifsa Ashraf @hifsays and Oscar Luparia #poetry #poetrycommunity #poetrylovers #micropoetry #photography #pink #rose #pinkrose #photo #photooftheday #photographylovers #pakistan
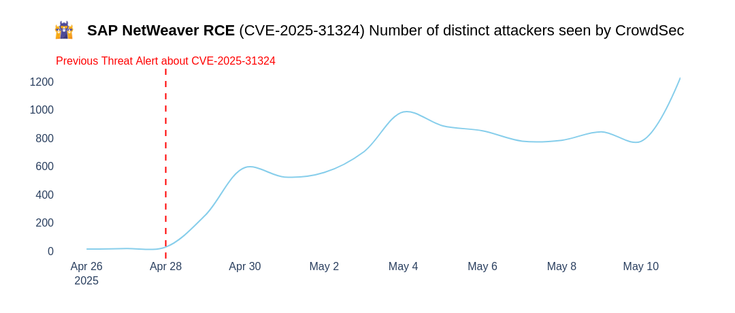
⚠️ Update: Active exploitation of SAP NetWeaver Zero-Day (CVE-2025-31324) surges!
At the end of April, the CrowdSec Network detected a wave of critical zero-day vulnerability exploits (CVE-2025-31324) affecting SAP NetWeaver’s Visual Composer component. Since then, exploitation attempts have surged by 20x, with multiple threat actors now actively targeting unpatched systems.
ℹ️ About the exploit:
A critical zero-day vulnerability (CVSS 10.0) was identified in SAP NetWeaver's Visual Composer component. This flaw allows unauthenticated attackers to upload arbitrary files via the /developmentserver/metadatauploader endpoint, leading to remote code execution with high privileges. Active exploitation in the wild was confirmed, with attackers deploying web shells and tools like Brute Ratel to gain persistent access.
🔎 Trend analysis:
🔹 April 25, 2025: The CrowdSec Network starts flagging the first exploitation attempts.
🔹 April 28, 2025: The CrowdSec Network publicly communicated about ~40 IPs exploiting the CVE.
🔹 April 29, 2025: A coordinated actor nicknamed Magical Firebrick Piopio in Crowdsec CTI was flagged as exploiting this CVE, and 400 IPs were flagged that day.
🔹 May 12, 2025: More than 1,000 IPs are being spotted daily and made available in the CrowdSec CTI. Most IPs (90%) are from Microsoft ASN georeferenced in the US, with a high rotation rate.
✅ How to protect your systems:
🔹 Patch: Apply SAP Security Note immediately.
🔹 Preemptive blocking: Use the CrowdSec CTI to block IPs exploiting CVE-2025-31324 👉 https://app.crowdsec.net/cti?q=cves%3A%22CVE-2025-31324%22
🔹 Stay proactive: Install the CrowdSec WAF to stay ahead of exploit attempts with 100+ virtual patching rules available 👉 https://www.youtube.com/watch?v=LyNfr4QWiqw
Sharing insights and taking swift action can collectively reduce the impact of these threats. This is your call to action for real-time threat intelligence and #collaborative #cybersecurity 👉 http://crowdsec.net/
///PS: Handilibre///
In addition to providing guidance on disability issues when we can and taking your suggestions into account for moving forward, we also contact developers to add features missing from certain free tools ;)
#handilibre #disability #free #collaborative #software #plan #3Dprinting #participation
///Handilibre Call for Participation///
Do you or some close have a disability and a free project has made your life easier?
It could be a plugin, a 3D print, a software program, a fablab project...
Share it with us in the comments or on www.handilibre.org to spread the word!
#handilibre #disability #free #collaborative #software #plan #3Dprinting #participation
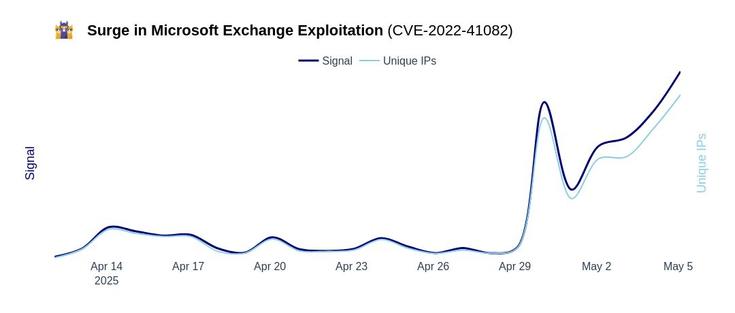
🚨 Threat alert on #Microsoft Exchange: Surge in CVE-2022-41082 exploitation 👇
The #CrowdSec Network has detected a wave of exploitation attempts targeting CVE-2022-41082, a critical vulnerability in Microsoft Exchange Server. This flaw allows authenticated attackers to execute remote code via PowerShell, often in conjunction with CVE-2022-41040, forming the notorious "ProxyNotShell" exploit chain.
ℹ️ About the exploit:
CVE-2022-41082 affects Microsoft Exchange Server 2013, 2016, and 2019. When exploited alongside CVE-2022-41040, it enables attackers to gain remote access and execute arbitrary code. Microsoft has released patches addressing these vulnerabilities, but unpatched systems remain at high risk.
🔎 Trend analysis:
🔹 The exploitation started on April 28 and is still going on as we publish.
🔹 Most of the exploitation attempts are emanating from cloud actors known for dubious activity (M247 Europe SRL or LATITUDE-SH) and already referenced in several of the CrowdSec Blocklists.
✅ How to protect your systems:
🔹 Make sure your servers are patched and up-to-date.
🔹 Check this 4-minute video on how to install the CrowdSec Web Application Firewall and get instant protection from this exploitation and hundreds of other CVEs: https://youtube.com/watch?v=LyNfr4QWiqw
🔹 Protect yourself using blocklists updated in real-time with collective intelligence: https://app.crowdsec.net/blocklists/65a56c160469607d9badb813
Sharing insights and taking swift action can collectively reduce the impact of these #threats. This is your call to action for real-time threat intelligence and #collaborative #cybersecurity.
For more information, visit http://crowdsec.net
#collaborative #tanrenga by Paul Callus @callus.safi47 of Ħal Safi, Malta and Linda L. Ludwig of Florida, USA. — both accomplished poets & editors. #poetry #micropoetry #tanka #haiku #poetrycommunity #poetrylovers