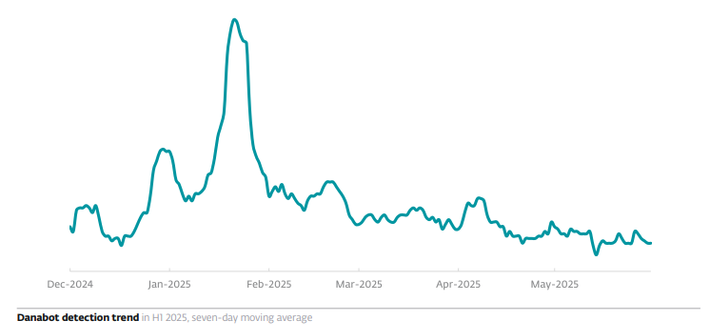
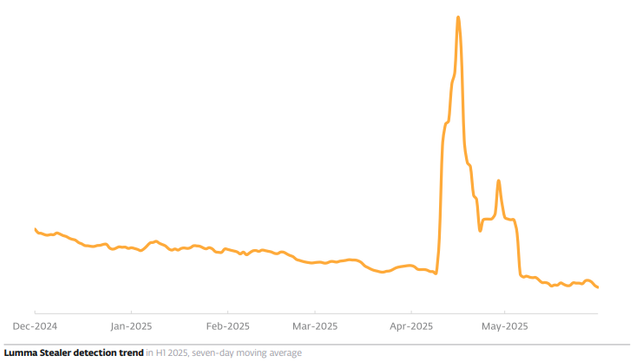
In May 2025, #ESET participated in operations that largely disrupted the infrastructure of two notorious infostealers: #LummaStealer and #Danabot.
As part of the Lumma Stealer disruption effort, carried out in conjunction with Microsoft, BitSight, Lumen, Cloudflare, CleanDNS, and GMO Registry, ESET supplied technical analysis and statistical information.
Danabot was targeted by the #FBI and #DCIS, alongside #OperationEndgame led by #Europol and #Eurojust. ESET participated together with several other companies. We provided the analysis of the malware’s backend infrastructure and identified its C&C servers.
Before these takedowns, both infostealers were on the rise: in H1 2025, Lumma Stealer detections grew by 21%, while Danabot’s numbers increased by more than 50%.
For a time, Lumma Stealer was the primary payload of HTML/FakeCaptcha trojan, used in the #ClickFix social engineering attacks that we also cover in this issue of the #ESETThreatReport. In recent months, we have seen Danabot being delivered via ClickFix as well.
For more details on these two operations and on the ClickFix attacks, read the latest #ESETThreatReport: https://welivesecurity.com/en/eset-research/eset-threat-report-h1-2025
#dcis
From Navigating the Unknown to Building a Movement: My DCIS Cancer Journey - https://dcisunderstood.org/from-navigating-the-unknown-to-building-a-movement-my-dcis-journey/ #DCIS
Oops: DanaBot Malware Devs Infected Their Own PCs - The U.S. government today unsealed criminal charges against 16 individuals accused... https://krebsonsecurity.com/2025/05/oops-danabot-malware-devs-infected-their-own-pcs/ #defensecriminalinvestigativeservice #artemaleksandrovichkalinkin #u.s.departmentofjustice #russiaswaronukraine #aleksandrstepanov #neer-do-wellnews #alittlesunshine #lummastealer #flashpoint #proofpoint #microsoft #teamcyrmu #intel471 #maffiozi #danabot #jimmbee #dcis
Oops: DanaBot Malware Devs Infected Their Own PCs
https://krebsonsecurity.com/2025/05/oops-danabot-malware-devs-infected-their-own-pcs/
#DefenseCriminalInvestigativeService #ArtemAleksandrovichKalinkin #U.S.DepartmentofJustice #Russia'sWaronUkraine #Ne'er-Do-WellNews #AleksandrStepanov #ALittleSunshine #LummaStealer #Flashpoint #proofpoint #microsoft #teamcyrmu #Intel471 #Maffiozi #DanaBot #JimmBee #Zscaler #google #Paypal #Lumen #DCIS #ESET #Onix #fbi
The #FBI and #DCIS disrupted #Danabot. #ESET was one of several companies that cooperated in this effort. https://www.welivesecurity.com/en/eset-research/danabot-analyzing-fallen-empire/
#ESETresearch has been involved in this operation since 2018. Our contribution included providing technical analyses of the malware and its backend infrastructure, as well as identifying Danabot’s C&C servers. Danabot is a #MaaS #infostealer that has also been seen pushing additional malware – even #ransomware, such as #LockBit, #Buran, and #Crisis – to compromised systems.
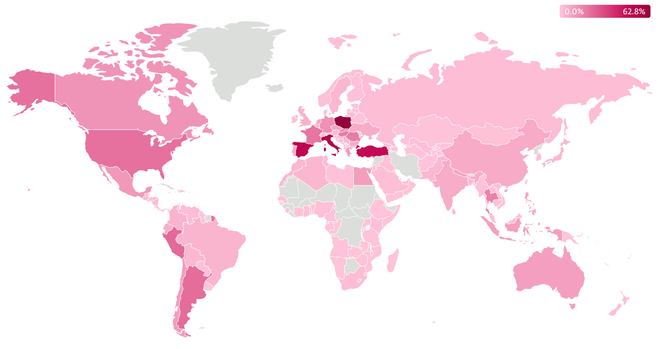
We have analyzed Danabot campaigns all around the world and found a substantial number of distinct samples of the malware, as well as identified more than 1,000 C&Cs.
This infostealer is frequently promoted on underground forums. The affiliates are offered an administration panel application, a backconnect tool for real-time control of bots, and a proxy server application that relays the communication between the bots and the C&C server.
IoCs are available in our GitHub repo. You can expect updates with more details in the coming days. https://github.com/eset/malware-ioc/tree/master/danabot
Danielle Fishel shares her #DCIS diagnosis and reminds women not to put off their mammogram!
https://www.huffpost.com/entry/danielle-fishel-cancer_n_66c33c11e4b00547468bd799
Thank you Danielle Fishel for sharing your #DCIS diagnosis. Don't put off your mammogram.
https://www.huffpost.com/entry/danielle-fishel-cancer_n_66c33c11e4b00547468bd799
A team of #researchers mapping a #molecular atlas for ductal carcinoma in situ (#DCIS) has made a major advance toward distinguishing whether the early pre-cancers in the #breast will develop into invasive #cancers or remain stable.
#BreastCancer #Medical #Biology #sflorg
https://www.sflorg.com/2022/11/med11192201.html