JC64dis 3.1 Adds Better Cross References for C64 Disassembly
#Commodore64 #C64 #RetroComputing #ReverseEngineering #Disassembly #6502 #SID #GameDev #DemoScene #VICEEmulator #OpenSource
https://theoasisbbs.com/jc64dis-3-1-adds-better-cross-references-for-c64-disassembly/?fsp_sid=816
#disassembly
Does anyone know if BAP is dead now? Last update on the public github is from 8 months ago https://github.com/BinaryAnalysisPlatform/bap
#binary #vulnerability #disassembly #ocaml
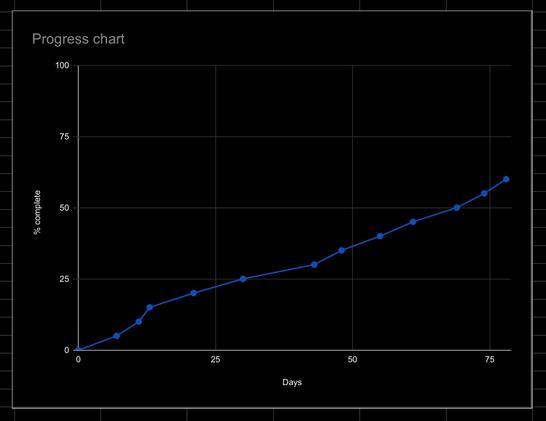
Some projects just take a long time to work through. I mean, I’ve got to make sure it can stand alongside the others.
It should be worth the wait, though.
Disassembling terabytes of random data with Zig and Capstone to prove a point
https://jstrieb.github.io/posts/random-instructions/
#HackerNews #Disassembling #terabytes #of #random #data #with #Zig #and #Capstone #to #prove #a #point
Annotated #Disassembly of the #NES Super #Contra ROM
#retrodev #retrogaming #assembler #reverseengineering #nesdev #ROMhacking
Annotated Disassembly of the N...
I have an extra Psion 3a with broken hinges.
I have managed to disassemble the display bezel.
Now I'm not sure how to disassemble the ribbon cable.
Computer Archeology’s Page On Space Invaders
This one's for the hardcore techies out there. Computer Archeology is a terrific site with information on the inner workings of several prominent games. One of their most complete and detailed is on the code and hardware of arcade Space Invaders, including a disassembly. While it is not, a
https://setsideb.com/computer-archeologys-page-on-space-invaders/
#retro #ComputerArcheology #disassem #disassembly #hardware #retro #spaceinvaders #taito
Grabbed a highlight from Sunday's #pinball hacking #stream where I explain what I'm working on and how it fits into my project to a chatter who dropped in.
A good overview if you're interested in my work reverse-engineering Data East's Time Machine so I can add my own enhancements to the code.
https://www.twitch.tv/gandalfdagreat/v/2489738146?sr=a
#reverseEngineering #mc6800 #disassembly #pinMAME #MAME #C #Livestream #twitch #hacking #retroComputing
🎉🤖 Behold the riveting #disassembly #adventure of a #modulation #generator that only an #oscilloscope fetishist could love. Dive deep into a sea of acronyms, numbers, and a clock that even your grandfather wouldn't miss. It's like watching paint dry, but with more #circuits and fewer fumes! ⚡🔧
https://tomverbeure.github.io/2025/04/26/RS-AMIQ-Teardown-Analog-Deep-Dive.html #tech #enthusiasts #HackerNews #ngated
Taking Apart a Boat Lighting Control Panel
*sigh* things rarely work out the way they should in my head, couldn't find the bit patterns I worked out that should correspond to the representations of digits on the seven-segment displays. I think I'm going to pivot again to implementing a simulator for time machine in PinMAME so I can shoot shots with the keyboard and see what happens in the debugger
#MAME #Debugger #Pinball #Ghidra #Disassembly #ReverseEngineering
Another detour on the Time Machine #Pinball #disassembly project, I think the processor specification I've been using is incomplete. There are a lot of instances of indexed addressing being interpreted as an offset from the current address. This is making it hard to figure out where in RAM different pieces of data live without manually calculating the address.
Time to learn #Sleigh and patch the processor definition. Maybe the extension author will even accept a pull request.
Moonlight Tower Disassembly • Austin, Texas, USA
Rolleiflex SL66 • Kodak Tri-X 400 • 2025
#FilmPhotography #Kodak #TriX #Camera #Film120 #MediumFormat #Rolleiflex #BWfilm #Monochrome #Photography #ATX #TX #Downtown #Austin #Texas #Outdoors #Moonlight #Tower #Disassembly #Street #April_27_2025
Cool. After my productivity speedbump of last night, my Time Machine #pinball #disassembly project has moved forward. I now have a python script which exports the #ghidra program into an info file which a real 6800 disassembler reads to produce assembly which should actually be able to be reassembled into a final binary.
I'll use ghidra to continue analyzing the code, and when I'm ready to actually start writing my own patches, I'll do that outside of ghidra as though it were a source file.
Perusing the #documentation for JPype as it's the translation layer letting me write my #Ghidra script in #Python, and I'm enjoying the conversational style of the introduction in the user guide
https://jpype.readthedocs.io/en/latest/userguide.html#case-1-access-to-a-java-library
Haven't worked on my #Pinball code #disassembly much directly, but I have been working to get all the tools I need collected. It seems like once I've used #Ghidra to annotate and explore the code I'll want to bring the disassembled "source" into a real editor to actually make my changes.
To ensure the actual disassembly is compatible with assembling back to EPROM images, I plan to write a script to convert ghidra's code representation into a file that will drive a dedicated 68xx disassembler
This week I have mostly been digging into the code for Heavy on the Magick by Gargoyle Games. ( https://spectrumcomputing.co.uk/entry/2274/ZX-Spectrum/Heavy_on_the_Magick ). The graphics are freaky, so far I found the code which blits them onto the menu screen at normal size (The game blits the main play area double the size). Normally on a spectrum a byte, when stored on the screen will display 8 pixels in order from left to right. In HOTM, they shift every odd pixels into the left hand nibble of the byte, then shift the even pixels into the right hand nibble. But thinking about it, if you are doubling the size visually, a byte will only hold 4 pixels, so I reckon they shift each pixel into the two bytes alternatively within the same loop #zxspectrum #retrogaming #z80 #disassembly
Printed myself a 68xx #reference guide and put it in a binder. It'll be nice having a paper reference while I'm working on the Time Machine #Pinball #disassembly effort.
I've really been enjoying having a color #printer of my very own, and I'm especially happy about the fact that I haven't even put a visible dent in the ink tank fill indicators from the first fillup. The #EcoTank was pricey, but not having to be skimpy on ink usage is worth it.
"So awhile ago I had asked federal employees for an interview for a story." : from r/fednews
https://www.reddit.com/r/fednews/comments/1j2ykef/so_awhile_ago_i_had_asked_federal_employees_for/


![A screenshot from Ghidra with some disassembled x86 Intel-style assembly code. The disassembly reads as follows:
entry
LEA ECX,[LAB_08049086]
XOR dword ptr [ECX]=>LAB_08049086,0x5414070e
XOR dword ptr [ECX + 0x4]=>LAB_08049087+3,0x550a1141
XOR dword ptr [ECX + 0x8]=>LAB_0804908d+1,0x1241010e
XOR dword ptr [ECX + 0xc]=>LAB_0804908f+3,0x711491b
XOR dword ptr [ECX + 0x10]=>LAB_08049096,0x466d4f03
ADD EBX,0x1
ADD EAX,0x4
ADD EDX,0x13
INT 0x80
SUB EAX,0x12
XOR EBX,EBX
INT 0x80
LAB_08049086
PUSH EDI
LAB_08049087+3
PUSH 0x63207461
OUTSD DX,ESI
LAB_0804908d+1
JNZ LAB_080490fb
LAB_0804908f+3
AND byte ptr FS:[EDI + 0x6f],AH
AND byte ptr [EDI + 0x72],DH
LAB_08049096
OUTSD DX,ESI
OUTSB DX,ESI
AAS](https://files.mastodon.social/cache/media_attachments/files/115/877/642/154/254/266/small/d758682a2cf62d33.png)