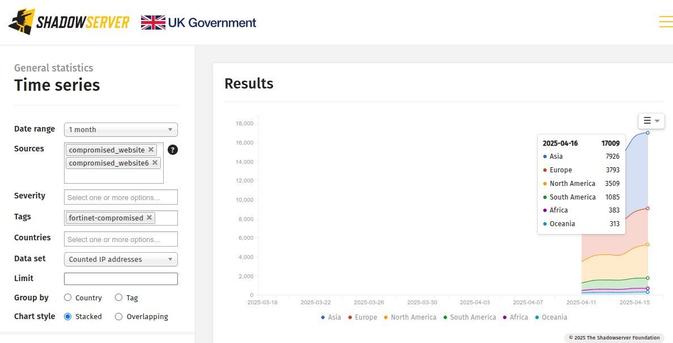
Now that it appears my move to BSD.cafe is complete, I believe it’s time for a #introduction.
First, I want to say how great it is to be part of the BSD.cafe community. I’m thrilled that this instance exists and is thriving.
I’m Blake, a Systems Administrator with a knack for #networks and #DevOps. Currently, I work in the insurance sector, focusing on #technology solutions for agricultural businesses. I have extensive experience with #Linux, #AWS, #Azure, and a variety of network solutions, from Fortigate (#FortiOS) to Netgate (#pfSense). I consider myself a big-picture solver, dedicated to enhancing infrastructure efficiency and security.
I’ve been using Linux daily since the late 2000s, when our family’s Windows XP machine gave out and I got my hands on Ubuntu 8.04 LTS. Since then, I’ve experimented with everything from Arch Linux to Void Linux. Recently, I’ve started exploring #FreeBSD and #OpenBSD, and I’m truly enjoying the fresh experience they offer.
When I’m not immersed in technology, you’ll find me participating in ultra-endurance #cycling events or tinkering with my #homelab. I’m committed to continuous learning and love sharing insights on cutting-edge network and server technologies. I also enjoy exploring how technology intersects with everyday life.
One of these days, I plan to create a proper blog site to share my thoughts and experiences.
I look forward to connecting with fellow tech enthusiasts and homelabbers!