🚨 RIFT Update:
We’ve boosted our compiler detection! 🛠️
Now with sharper insights into binaries built using GNU, MinGW, and MSVC toolchains.
More enhancements are on the way—stay tuned! 🔍✨
#ReverseEngineering #MalwareAnalysis #RIFT #malware #msft
#malwareAnalysis
🛑 DragonForce Ransomware Hits UK Retail in 2025 🛍️
A New RaaS threat targeting M&S, Co‑op & Harrods 📦 💣
📰 Read full malware breakdown:
🔗 https://wardenshield.com/dragonforce-ransomware-siege-on-uk-retail-in-2025-malware-analysis
#cybersecurity #Ransomware #infosec #dragonforce #UKRetail #AIThreats #malwareanalysis
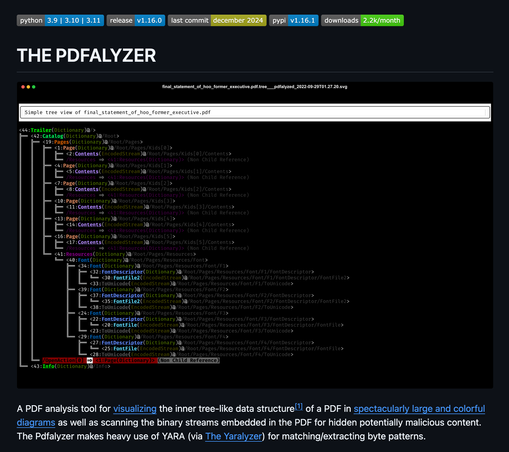
Just published version 1.16.6 of The Pdfalyzer, the surprisingly popular tool for analyzing (possibly malicious) PDFs I created after my own unpleasant encounter with such a creature. Includes a (kind of janky) #YARA rule for #GIFTEDCROOK infostealer PDFs.
* Github: https://github.com/michelcrypt4d4mus/pdfalyzer
* Pypi: https://pypi.org/project/pdfalyzer/
* Homebrew: https://formulae.brew.sh/formula/pdfalyzer
#pypi #python #pdf #pdfs #malware #Threatassessment #maldoc #malwareanalysis #homebrew #infosec #cybersecurity #yararule
Hello everyone.
In today's article, we are building a simple/medium level backdoor with python.
I wish everyone good work:
https://denizhalil.com/2025/06/28/simple-backdoor-project-with-python/
#backdoor #backdoorsimulation #c2 #cybersecurity #ethicalhacking #malwareanalysis #networking #python
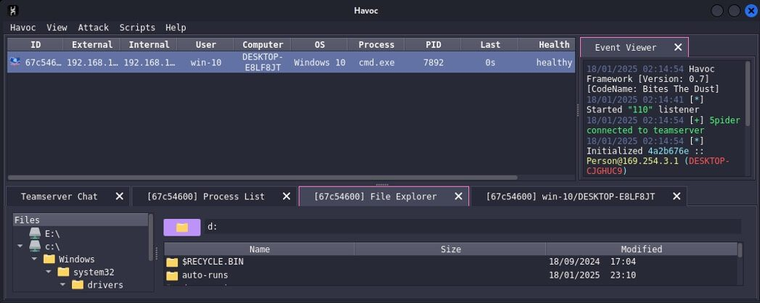
Sliver too mainstream? Cobalt Strike too patched? Say hello to Havoc.
@FortiGuardLabs just broke down a malicious Havoc C2 sample — and it’s bringing that open-source, post-exploitation energy with extra attitude.
Built for red teamers but abused by threat actors, this sample goes full dark mode:
- Shellcode loader in C++
- AES-encrypted payload
- XOR junk code to slow reverse engineering
- Dynamic API resolving
- LOLBin delivery via regsvr32
It’s like someone asked: “What if malware devs went full GitHub?” (never go full GitHub)
🔗 Full breakdown:
https://www.fortinet.com/blog/threat-research/dissecting-a-malicious-havoc-sample
TL;DR for blue teamers:
- Havoc ≠ harmless just because it’s open source
- Monitor regsvr32, rundll32, mshta — Havoc loves its LOLBins
- Watch for process injection + thread creation anomalies
- Memory analysis > file-based detection here
- Don’t assume your EDR is catching every beacon on port 443
Is it threat emulation or a real attack?
— Blue teamer having a full-blown identity crisis at 2am
Shoutout to @xpzhang and team for their amazing work!
#ThreatIntel #MalwareAnalysis #HavocC2 #RedTeamTools #PostExploitation #Infosec #BlueTeam #ReverseEngineering #CyberSecurity
New blog post up 🕵️♂️
🧅 Playing With Bits: Of Malware Labs, Steganography and Narnia
A peek into hiding data in images, setting up a simple but safe malware lab, and revisiting the OverTheWire Narnia wargame 🧙♂️
Read here: https://dreaming-of-dragons.blogspot.com/2025/06/playing-with-bits-of-malware-labs.html
#malwareanalysis #steganography #ctf #reversing #cybersecurity #linux #hacking
MalChela v3.0 enhances investigative workflows by introducing cases for organization, replacing MismatchMiner with FileMiner for improved file analysis, and suggesting tools based on file characteristics, streamlining the analysis process. #MalChela #DFIR #MalwareAnalysis
Explore how botnets operate—from infected “zombie” devices to the shadowy command-and-control (C2) centers that orchestrate massive cyberattacks. This episode uncovers the architecture, evolution, and real-world impacts of botnet-driven threats, plus how organizations can defend against them.
#CyberSecurity #Botnets #CyberThreats #C2Servers #MalwareAnalysis
#InfoSecPodcast #CyberAwareness
"Introduction to Static Analysis with radare2" by Professor Czech https://www.youtube.com/watch?v=RnqsT8GL3dg #malwareanalysis #reverseengineering
No PE header? No problem.
@FortiGuardLabs dropped a deep dive into a malware sample dumped without a PE header — like a cybercriminal rage-quit halfway through packing their payload.
You ever load a binary in IDA and think, “Am I being punk’d?”
Yeah, it’s one of those samples.
This sample:
Reconstructs its own PE structure at runtime
Hides config data in obfuscated blobs
Uses anti-sandbox tricks to avoid analysis
Drops yet another info-stealer, because originality is dead
It’s engineered to break basic static analysis and dodge sandboxes like it’s speedrunning DEFCON CTF.
🔗 Full breakdown:
https://www.fortinet.com/blog/threat-research/deep-dive-into-a-dumped-malware-without-a-pe-header
TL;DR for blue teamers:
Static AV signatures won’t help here
Watch for suspicious memory allocations + hollowing patterns
Endpoint heuristics > file-based detection
Log your PowerShell and LOLBins — this thing probably brings friends
If your EDR cries when it sees raw shellcode, maybe give it a hug
#ThreatIntel #MalwareAnalysis #ReverseEngineering #Infosec #PEFilesAreSo2020 #EDREvasion #LOLbins #CyberSecurity #BlueTeam
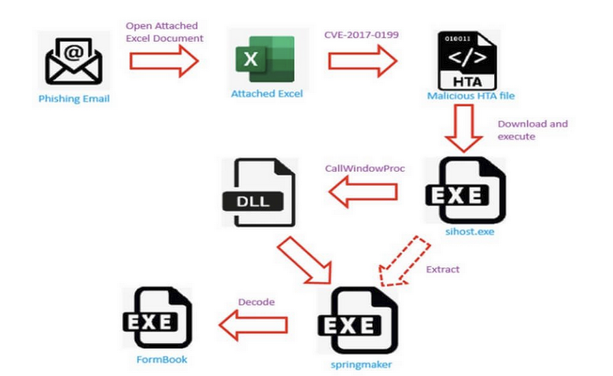
🚨 0-day vibes from 2017? Yup, it’s still happening.
A malicious Excel file using CVE-2017-0199 is out here in 2025 dropping FormBook like it's a fresh mixtape.
The attack chain?
- Macro-free Excel
- Weaponized with remote .hta
- Payload: Info-stealer FormBook
Despite being 7+ years old, this vuln still slaps in phishing campaigns — because patching is apparently a myth.
Full technical breakdown by @FortiGuardLabs: https://www.fortinet.com/blog/threat-research/how-a-malicious-excel-file-cve-2017-0199-delivers-the-formbook-payload
TL;DR for blue teamers:
- Watch your egress traffic
- Harden Office apps
- Monitor LOLBins (Living Off the Land Binaries)
- Block outbound to shady IPs faster than your memes go viral
Don’t let your org get dunked on by a 2017 CVE in 2025. That’s not a good look.
#CyberSecurity #ThreatIntel #FormBook #CVE20170199 #Infosec #BlueTeam #MalwareAnalysis #HackerNews #Phishing
Cybercrime group FIN6 (aka Skeleton Spider) is leveraging trusted cloud services like AWS to deliver malware through fake job applications.
Our latest analysis breaks down:
🔹 How attackers use LinkedIn & Indeed to build trust
🔹 The use of resume-themed phishing lures
🔹 Cloud-hosted infrastructure that evades detection
🔹 The delivery of the More_eggs backdoor via .LNK files
🔹 Key defense strategies for recruiters and security teams
This campaign is a masterclass in low-complexity, high-evasion phishing
📖 Read the full breakdown: https://dti.domaintools.com/skeleton-spider-trusted-cloud-malware-delivery/?utm_source=Mastodon&utm_medium=Social&utm_campaign=Skeleton-Spider
#CyberSecurity #ThreatIntel #FIN6 #Phishing #CloudSecurity #MalwareAnalysis #InfoSec #SkeletonSpider
🧠💻 Tired of endless hours fighting with obfuscation techniques embedded inside of malware? Check out Anthony Galiette's #BSidesBoulder25 talk "AI-Assisted Reverse Engineering for Enhanced Malware Analysis, Deobfuscation, and Threat Coverage"! Anthony's talk provides a hands on approach to using GenAI to reduce analytic toil while reverse engineering malware, which explores three open-source tools that harness LLMs to supercharge malware triage, reverse engineering, and threat artifact extraction. Whether you're in IR, threat hunting, or detection engineering, this talk will show you how AI can help extract answers faster from binary hell. 🚀🔍 #BSides #BSidesBoulder #IncidentResponse #CyberSecurity #MalwareAnalysis #ReverseEngineering #LLM4Sec #BlueTeamPower
Check out our full schedule at https://bsidesboulder.org/schedule/
Tickets are available for purchase for our 13 June event here: https://www.eventbrite.com/e/bsides-boulder-2025-registration-1290129274389
🧬 SmokeLoader evades detection by manually loading a clean copy of ntdll.dll, completely bypassing user-mode hooks placed by EDRs and debuggers.
This article breaks down how the malware sidesteps common monitoring techniques — a must-read for analysts tracking stealthy loader behavior.
🔗 https://malwareandstuff.com/examining-smokeloaders-anti-hooking-technique/
#MalwareAnalysis #ReverseEngineering #Infosec #SmokeLoader #CyberSecurity
🚨 Cybersecurity Alert: AI Tool Installers Under Siege! 🚨
AI is revolutionizing everything. But so are the threats.
🛡️ Read the full article :
👉 https://wardenshield.com/numero-malware-in-2025-a-stealthy-saboteur-targeting-ai-tool-installers
#CyberSecurity #MalwareAnalysis #AI #ThreatIntel #WardenShield #CyberThreats #NumeroMalware #Infosec #AItools
🕵️♂️ Ever wonder how cybercriminals weaponize PDFs? 💥
Check out Filipi Pires' #BSidesBoulder25 talk, "Structural Insights: PDF Analysis for Detecting and Defending Against Threats"! In his session, he’ll explore the structure of PDFs and how malicious payload can be hidden within them, provide guidance on identifying how Indicators of Attack (IOAs) found within them, and show you how to outsmart common obfuscation routines found in them. Come for the malware, stay for the live demos and defense tips! 📄 #CyberSecurity #PDFThreats #MalwareAnalysis #BSides #BSidesBoulder
Check out our full schedule at https://bsidesboulder.org/schedule/
Tickets are available for purchase for our 13 June event here: https://www.eventbrite.com/e/bsides-boulder-2025-registration-1290129274389
🕷️ Latrodectus: The “Black Widow” Malware of 2025
A new threat has emerged — Latrodectus, a stealthy malware loader evolving from IcedID’s shadow.
Read the full article:
👉 https://wardenshield.com/latrodectus-malware-analysis-a-deep-dive-into-the-black-widow-of-cyber-threats-in-2025
#CyberSecurity #InfoSec #Latrodectus #ThreatIntel #MalwareAnalysis #Privacy #IcedID #DigitalSecurity #WardenShield #CyberThreats #FOSS #TechNews
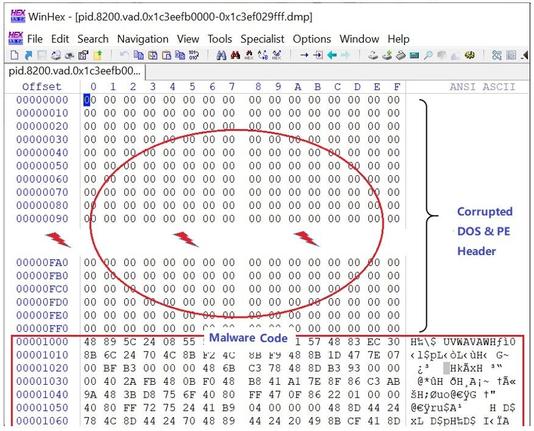
🖥️ A new Windows-based Remote Access Trojan (RAT) has been exposed — and it’s unusually stealthy.
👉 It corrupts critical DOS + PE headers, making it difficult to analyze or reconstruct.
👉 It embeds inside dllhost.exe, communicates via encrypted C2, and runs multi-threaded client sessions.
👉 Researchers at Fortinet had to replicate the compromised system’s environment to finally analyze it.
🚨 This attack highlights how adversaries are evolving to evade both detection and reverse engineering.
⚠️ Organizations should ensure endpoint monitoring can catch process anomalies — not just file signatures.
#CyberSecurity 🛡️ #MalwareAnalysis 🔍 #WindowsSecurity 💻 #ThreatIntel 🌐
https://thehackernews.com/2025/05/new-windows-rat-evades-detection-for.html
🔥 Hot off the presses!
DomainTools Investigations shares that a spoofed antivirus download page is delivering VenomRAT, StormKitty, and SilentTrinity—a powerful combo for credential theft, persistence, and long-term access.
🔎 We traced the infrastructure, payloads, and attacker tactics.
Full breakdown: https://dti.domaintools.com/venomrat/?utm_source=Mastodon&utm_medium=Social&utm_campaign=VenomRAT
Hashes for the Masses: Finding What Matters in a Sea of Samples #DFIR #MalwareAnalysis #Hash #MalChela