🔎 Malware Analysis Tools & Resources — Lab-Only Guide (Defensive) ☣️🛡️
Malware analysis is the practice of studying suspicious files and binaries to understand capabilities, indicators, and containment actions — always inside isolated, offline labs. 🧪💻 Below are trusted tools and resources analysts use to triage, unpack, and investigate malicious samples, plus learning hubs to level up your skills.
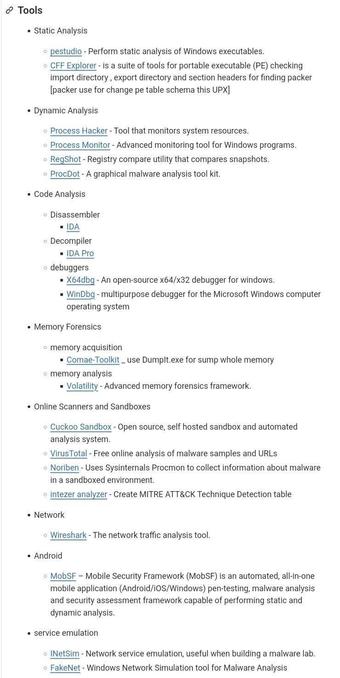
For static analysis (examining files without running them) analysts rely on tools like strings, file, ssdeep, PEStudio, Detect It Easy (DIE), Ghidra, and r2 / radare2 to inspect headers, imports, embedded strings, and binary structure. 🧩 For dynamic analysis (safe execution), sandboxes such as Cuckoo Sandbox, Any.Run, and instrumented VMs with Process Monitor, Process Explorer, Procmon, Sysmon, API monitor, plus network capture (Wireshark/tshark, tcpdump) reveal runtime behavior and network indicators. 🔬📡
Memory & forensic analysis uses Volatility / Volatility3, Rekall, and tools to capture RAM and extract artifacts. For unpacking and debugging native code, analysts use x64dbg, WinDbg, GDB, and deobfuscation helpers; for Java/.NET, tools like jadx and dnSpy help reverse engineered bytecode. 🧠⚙️
Threat intel & enrichment resources accelerate investigation: VirusTotal, Hybrid Analysis, MalwareBazaar, Malpedia, AbuseIPDB, OTX (AlienVault), and MISP provide samples, IOCs, yara rules, and community knowledge. 🗂️📊 Combine these with YARA for signature matching and Sigma for log detections. 🔎🧰
Learning resources & safety: follow vendor blogs (Microsoft Defender, Cisco Talos, CrowdStrike), training platforms (Practical Malware Analysis labs, REMnux VM, FLARE VM), and courses (SANS/GIAC tracks, online DFIR courses). Always run samples in air-gapped / host-only VMs, snapshot before/after, and capture PCAPs & memory for reproducibility. 📚🔐
#MalwareAnalysis #DFIR #ThreatHunting #Volatility #CuckooSandbox #Ghidra #VirusTotal #CyberSecurity #InfoSec #DigitalForensics #YARA