#UnlimitedMobile senkt die Preise: Der Unlimited Max mit 300 Mbit/s im o2-Netz ist jetzt für 29,99 Euro monatlich zu haben - bis zu 70 Prozent günstiger als vergleichbare Tarife direkt bei #O2. https://winfuture.de/news,156443.html?utm_source=Mastodon&utm_medium=ManualStatus&utm_campaign=SocialMedia
#o2
Pues hemos estado desde las 20h de ayer sin conexion a internet por #O2 y desconozco la causa.
#o2 can do. Läuft #südschwarzwald
Du kannst es dir kaum ausdenken:
Auf Nachfrage erklärt der #Gemüsetürke dass die #Avocado zwar #essreif sei, aber nicht überall. Ins #Stadion könne man sie zB nicht mitnehmen. Ich kaufe also 2 da er auch erklärt man könne sie über Nacht einfrieren, dann wären sie nach dem Auftauen weich. Besmillah, ischschwöhr -ich kaufe noch eine.
Im O2-Shop hat #O2 kein Netz aber um die #Esim zu enrollen könne man das freie WiFi des #Otelo-Shops benutzen wenn man sich eng an die Wand stellt.
„Unbegrenzter Tarif“, „Unbegrenztes Datenvolumen“ … „Mehr Daten buchen“
Die UX von Sauerstoff-Mobile ist an der Stelle aber auch kaputt 😂. Mehr als unendlich? Wenn ich den Button drücke, kommt eine Auswahl, in der ich „TV und Sicherheitspakete“ buchen kann 😅
BRITs nominations revealed as female stars dominate in record-breaking list
Hat noch jemand DSL Probleme mit #o2 #o2telefonica in Bad #Oeynhausen #Eidinghausen ?
„Gutes Netz oder Geld zurück“: O2 führt eine Zufriedenheitsgarantie von 30 Tagen ein https://www.computerbase.de/news/internet/gutes-netz-oder-geld-zurueck-o2-fuehrt-eine-zufriedenheitsgarantie-von-30-tagen-ein.95862/ #Telefonica #O2
@jsanchez0x @PabloAsekas @Ragenau Por casualidad que operadora tienes ? Yo tanto con #O2 y #Digi no he sido capaz de hacer funcionar #Nginx Proxy Manager ..... por algún motivo la redirección de puertos no me funciona con un router #Mikrotik , ya una vez @PabloAsekas intentó ayudarme pero lo di por perdido. Aparentemente se redirigían las peticiones al #NAS #Synology
How to beat mobile hikes in 2026 and a top tip to avoid the price increases
https://fed.brid.gy/r/https://www.mirror.co.uk/tech/mobile-phone-annual-price-increases-36430105
Another example of a virtual assistant being utterly useless from #O2 (UK phone network)
Asking me to make a call from a faulty SIM card🙄
Switch-off of #3G affecting some #electric #vehicle #chargers
Mobile operator’s switch-off of 3G in #Scotland causing issues with some of Shetland’s electric vehicle chargers
Shetland Islands Council (SIC) said it was aware of disruption to charging network, which is due to #O2’s3G switch-off in #Shetland
The SIC’s environment and estate operations manager Carl Symons said this was part of a wider shut-down of 3G across Scotland.
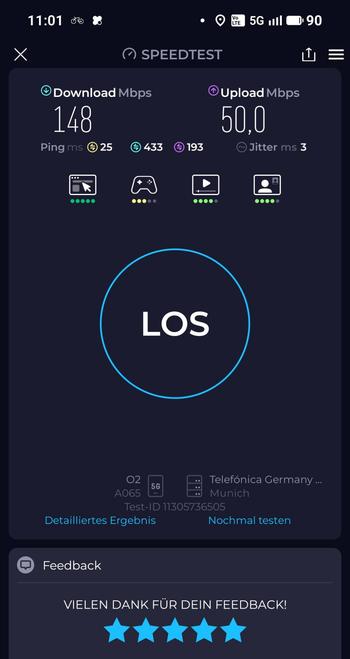
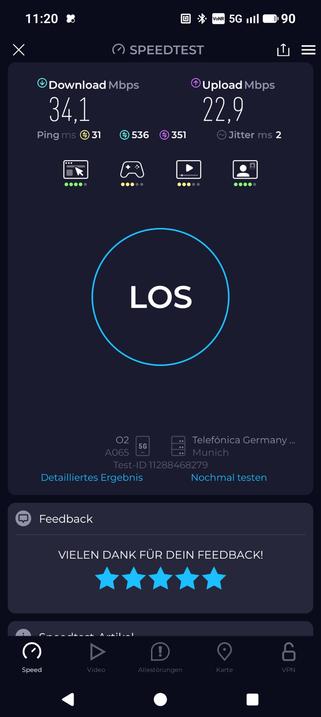
LieferTour mit AusBlick 🌳🌲🎄 #newWork unterwegs Arbeiten passt uff'm #Hotzenwald #5G #Mobilfunk #o2 can do.
New UK mobile network rivals EE and Vodafone with very cheap data and roaming perks
https://fed.brid.gy/r/https://www.mirror.co.uk/tech/uk-mobile-network-revolut-36411970
O2 Telefónica lanciert KI-Oma Hilde: Die smarte Assistentin schützt vor Telefon- und Online-Betrug durch praxisnahe Tipps in Videocalls. Sie erkennt Maschen wie Phishing oder Fake-Anrufe und hilft Nutzern, sicher im Netz zu surfen – charmant und direkt! 👵🛡️ https://www.golem.de/news/telefonica-o2-ki-oma-hilde-soll-vor-telefon-und-onlinebetrug-schuetzen-2512-203191.html #KI #CyberSicherheit #O2 #Newz 🤣🤣🤣 Hahahahah
Just had to phone #O2, now, I'm not racist in any way, but an Indian or Pakistani answered the call and I really couldn't understand him
Had to end the call as I wasn't getting anywhere
Broadband suppliers hand out £300 to UK consumers looking to switch
https://fed.brid.gy/r/https://www.mirror.co.uk/money/shopping-deals/best-broadband-deals-36370445
#o2 is ja schon krass. Also die Webseite bzw. Online-Dienste. Permanent 502er, 503er, nix lädt, „steht momentan nicht zur Verfügung“…
#5G standAlone 📱 #mobilfunk #o2 can do uff'm #Hotzenwald