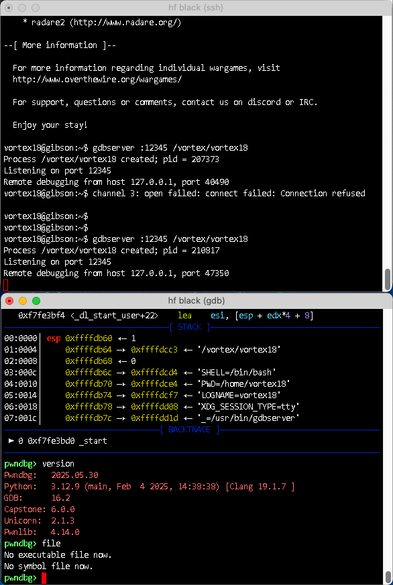
I've never tried gdb remote-debugging, but seeing that there's a new pwndbg out, I felt like trying it out. Unfortunately on MacOS it's only for remote debugging, so let's do that!
terminal 1:
local% ssh -L 12345:localhost:12345 user@remote
remote$ gdbserver :12345 /whatever
terminal 2:
local% ./bin/pwndbg whatever-localcopy
(gdb) target remote localhost:12345
works - see screenshot 🙂
#ctf #cybersecurity #pwndbg #overthewire #vortex #gdbserver #ssh