Hello! It has been a little while, but #nakeddiefriday is back in town.
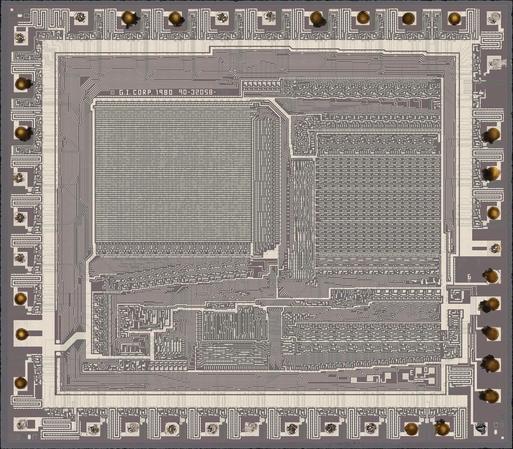
Today's exhibit is an old PIC1650A. Yes, one of *the* PIC series of microcontrollers. Note it was designed by General Instrument in 1980. It was fabbed in a single metal layer, metal-gate NMOS process. The image is about 4.3x3.8 mm.
No full-res link as SP is still borked.




![<div><img alt="" class="attachment-large size-large wp-post-image" height="385" src="https://hackaday.com/wp-content/uploads/2026/02/gas0pump-feat.png?w=800" style="margin: 0 auto; margin-bottom: 15px;" width="800" /></div><p>[Dave] over at Usagi Electric has <a href="https://www.youtube.com/watch?v=i0Qw8GrOcp0" target="_blank">a mystery on his hands</a> in the form of a computer. He picked up a Motorola 68000 based machine at a local swap meet. A few boards, a backplane, and a power supply. The only information provided is the machines original purpose: gas station pump control.</p>
<p>The computer in question is an embedded system. It uses a VME backplane, and all the cards are of the 3u variaety. The 68k and associated support chips are on one card. Memory is on another. A third card contains four serial ports. The software lives across three different EPROM chips. Time for a bit of reverse engineering!</p>
<p><span id="more-914854"></span></p>
<p>[Dave] quickly dumped the ROMs and looked for strings. Since the 68k is a big endian machine, some byte swapping was required to get things human readable. Once byte swapped, huge tables of human readable strings revealed themselves, including an OS version. The computer runs <a href="https://en.wikipedia.org/wiki/PSOS_(real-time_operating_system)" target="_blank">pSOS</a>, an older 68k based real time operating system – exactly what one would expect a machine from the 80’s to run.</p>
<p>The next step was to give](https://files.mastodon.social/cache/media_attachments/files/116/002/936/333/622/300/small/2d9eb46cd1aeca54.png)

