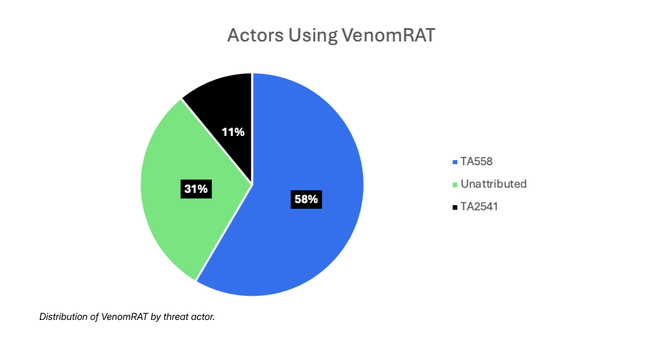
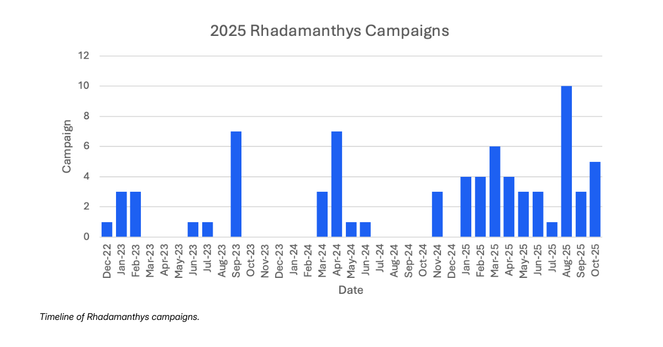
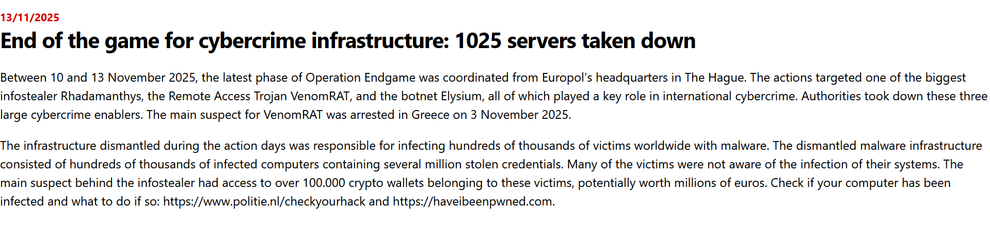
Proofpoint is proud to have assisted law enforcement in the #OperationEndgame investigation that led to the November 13, 2025 disruption of #Rhadamanthys and #VenomRAT, both #malware used by multiple cybercriminals.
• Rhadamanthys: https://brnw.ch/21wXs1N
• VenomRAT: https://brnw.ch/21wXs1O
---
Since May 2024, Operation Endgame—a global law enforcement and private sector effort that includes Proofpoint—has significantly disrupted the #malware and #botnet ecosystem.
👉 #Europol called the May 2024 Operation Endgame actions “the largest ever operation against botnets.”
👉 In May 2025, additional malware families and their creators, including #DanaBot, were taken down.
---
Each disruption forces threat actors to adapt and invest time and resources to retool their attack chains.
With our unique visibility and leading detection capabilities, Proofpoint researchers will continue monitoring the threat landscape and provide insight into the biggest cyber threats to society.