I am here only so you don't take me by mistake. Don't be too persistent, please. #threatmodel #bike
#threatModel
🎯 FINAL Pre-Event Interview Alert! Next Stop: Las Vegas!
This is it—our last #BlackHat USA 2025 conversation before we hit the road to Vegas (and who knows, maybe we'll broadcast from a desert pit stop along the way! 🚗)
But what a way to close out our pre-event coverage...
When Constitutional Law Meets #Cybersecurity: A Critical Conversation We All Need to Hear
What happens when we stop seeing government surveillance as a necessary evil and start recognizing it as a primary threat to privacy?
Jennifer Granick, ACLU's Surveillance and Cybersecurity Counsel, challenges us to rethink everything we assume about digital #privacy in her upcoming #BlackHatUSA 2025 keynote.
In this preview conversation with Marco Ciappelli, Jennifer makes a compelling case:
✅ The Fourth Amendment hasn't kept pace with technology
✅ Legal reform is too slow—so technologists must lead
✅ Privacy isn't just a legal problem—it's a design challenge
✅ We need a new #threatmodel that puts unchecked surveillance at the center
From defending hackers since #DEFCON 3 to fighting surveillance overreach at the ACLU, Jennifer brings decades of frontline experience to this critical discussion.
The key takeaway? While lawmakers debate, engineers and designers hold the power to protect civil liberties through encryption, data minimization, and privacy-first architecture.
This isn't just another privacy talk—it's a call to action for every technologist, policymaker, and privacy advocate.
🎥 Watch: https://youtu.be/dPCvsBqu6Uc
📍 Follow our complete Black Hat USA 2025 coverage: https://www.itspmagazine.com/bhusa25
See you in Vegas! 🎰 Feeling lucky, Sean Martin, CISSP?
#BlackHatUSA #Privacy #Cybersecurity #CivilLiberties #Surveillance #InfoSec #BHUSA25 #ThreatModeling #ACLU #PrivacyByDesign
I just realized I've been building a "threat model" of capitalism, informed by the idea that market systems are open networks that depend on trust. Kind of happy that I've somehow got my passion for cybersecurity and political philosophy to synergize so well.
My latest writing has me explore "four paradoxes" of capitalism which define the threat landscape for abuse in the system. https://misaligned.markets/tension-market-capitalism/
#FediHelp
I need to talk with someone skilled about #threatModel (digital side) specifically about 'downloads' / archiving / wget (mirroring) and online/offline for field activities (logistics / investigation ) and activist groups (water, mud, soil investigation within sampling and DIY analysis & data production)
I need to talk so do not point me any NGOs (I already now them). And I've been there too.
It's about holistic security approach in this very specific nudge.
Downloading things, offline access first, sharing (see Kiwix and kiwix itw at APC.org)
Being up to a mountain or down to a river or sewers system or so.
Or around floods in streets / towns / cities / lands.
Radio (SDR) scanning in the field and emergency data transmission / copy.
If it's not a clear and not understandable claim, I'm so sorry and please feel free to bake he with your asking and thoughts.
Very very important: carbon-mascu-male alpha-stupid-surviving-boyz are not welcome in this discussion and I'm sure you get the point my dear fedizens (no techbro / no cryptobro and more away)
cc @DigiDefenders @rysiek @onepict
@APC
@iffybooks @hackstub @lacontrevoie
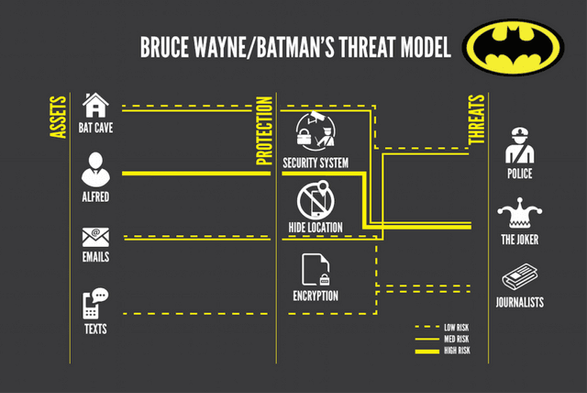
Batman's threat model.
Be like Batman and make a threat model.
#threatmodel
Time to update your threat models people: AI's the end of the Shell as we know it and I feel fine | @mpesce is scaring us all
https://www.theregister.com/2025/06/11/opinion_column_mcp_von_neumann_machine/
Looking at some #AI generated #threatmodel output and it listed stealing a user's credentials and using them in the "Spoofing" category. I was uncertain. Is that spoofing or elevation of privilege. So I wander over to a #microsoft page on #stride.
They say it's spoofing, which is fine. It's reasonable. I don't care as long as we all agree.
But in that table, that's literally the only example of spoofing. There are a LOT of other kinds of things that could be called spoofing. If you're gonna have only one example of spoofing, I don't think stealing credentials is the best example.
Keynote von Martin Haunschmid: Security ist so schlimm wie vor 20 Jahren
Die Keynote von Martin Haunschmid zeigt drastisch, wie wichtig es ist, Cybersecurity frühzeitig in der Entwicklung zu berücksichtigen.
https://www.se-trends.de/keynote-martin-haunschmid-security/
#Anforderungen #Veranstaltungen #Angriffssicherheit #DSGVO #MartinHaunschmid #OWASP #ReConf #ShiftLeft #ThreatModel
Lastly, there's the training data. I work for #AWS (so these are strictly my personal opinions). We are opinionated about the platform. We think that there are things you should do and things you shouldn't. If you have deep knowledge of anything (Microsoft, Google, NodeJS, SAP, whatever) you will have informed opinions.
The threat models that I have seen, that use general purpose models like Claude Sonnet, include advice that I think is stupid because I am opinionated about the platform. There's training data about AWS in the model that was authored by not-AWS. And there's training data in the model that was authored by AWS. The former massively outweighs the latter in a general-purpose, trained-on-the-Internet model.
So internal users (who are expected to do things the AWS way) are getting threats that (a) don't match our way of working, and (b) they can't mitigate anyway. Like I saw an AI-generated threat of brute-forcing a cognito token. While the possiblity of that happening (much like buying a winning lottery ticket) is non-zero, that is not a threat that a software developer can mitigate. There's nothing you can do in your application stack to prevent, detect, or respond to that. You're accepting that risk, like it or not, and I think we're wasting brain cells and disk sectors thinking about it and writing it down.
The other one I hate is when it tells you to encrypt your data at rest in S3. Try not to. There's no action for you to take. The thing you control is which key does it and who can use that key.
So if you have an area of expertise, the majority of the training data in any consumer model is worse than your knowledge. It is going to generate threats and risks that will irritate you.
4/fin
Threat models evolve over time, the same as your software does. Nobody is building a save/load feature into their AI powered threat model. Getting deterministic output from consumer-grade LLMs is not a given. So even if you DO create save/reload capability, it's imperfect.
All the tools I've seen start every session from a blank sheet of paper. So If you're revisiting an app that you threat modeled before, because you want to update your model, you're going to start from scratch.
3/n
Related to this, nobody seems to account for the fact that LLMs bullshit sometimes. If you pin someone down and say "the user of your AI-powered threat modeller: do they know how to do a threat model without AI?" Many people will say "yes." Because to say "no" is to admit that the people will be blindly following LLM output that might be total bullshit.
The goal, however, of many of these systems is to make threat modeling more accessible to people who don't know how to do it. To do that, though, you'd have to be more skeptical about your user, and spend some time educating them. Otherwise, they leave the process no smarter than they began.
Honestly, I think a lot of people think the threat model is going to be done entirely by the AI and they want to build a system where the human just consumes and uses it.
2/n
I have seen a lot of efforts to use an #LLM to create a #ThreatModel. I have some insights.
Attempts at #AI #ThreatModeling tend to do 3 things wrong:
- They assume that the user's input is both complete and correct. The LLM (in the implementations I've seen) never questions "are you sure?" and it never prompts the user like "you haven't told me X, what about X?"
- Lots of teams treat a threat model as a deliverable. Like we go build our code, get ready to ship, and then "oh, shit! Security wants a threat model. Quick, go make one." So it's not this thing that informs any development choices during development. It's an afterthought that gets built just prior to #AppSec review.
- Lots of people think you can do an adequate threat model with only technical artifacts (code, architectuer, data flow, documentation, etc.). There's business context that needs to be part of every decision, and teams are just ignoring that.
1/n
Your TOTP is Not a Second Factor—If You Store It Wrong #OPSEC #Cybersecurity #Infosec #2FA #TOTP #PasswordSecurity #ThreatModel #DataBreach #SecureHabits #OnlineSecurity #DigitalAnonymity #CyberGhost #DeadSwitch #CyberHygiene
http://tomsitcafe.com/2025/04/28/your-totp-is-not-a-second-factor-if-you-store-it-wrong/
but seriously would #Crowdstrike's lawyers come after me if i publish findings from a public threat model where i might write up findings for airlines and hotels for lacking vendor diversity and failing open on connected systems (e.g. you could book and pay for hotels that were offline, but Bookings.com and some others didn't give a fuck and sent people to hotels not expecting them for days?)
another finding for not having a plan or procedure. etc.
The #encryption topic in #InstantMesaging is popular again recently. As usual there's a lot of misunderstanding and little discussion of a #ThreatModel when giving recommendations.
If the private key is backed up with Apple or Google from your phone, then your messages may as well not be encrypted 🙈 I've again seen this indirectly with contacts changing phones and their keys are the same as on their old device. Due to automatic backups I guess.
Doesn't matter if it's #WhatsApp, #Signal or #XMPP
Here, in .de, we tend to have cellars (basements), subterranean storage closets; that's where i keep my "Off-Site" #backup.
I know, i know; I deem it good enough, for my personal #HomeLab #ThreatModel - i'm not keeping billable customer data safe. 😉
#Privacy is taken care of inside the VMs - #LUKS inside the VM - makes things more convenient - all the NAS/VM host knows is text/plain ZVOLs - helps with quick (non-interactive) reboots.
Julie Angwin is working on a #privacy #threatmodel for authoritarianism.
https://buttondown.com/JuliaAngwin/archive/a-threat-model-for-opposing-authoritarianism/
Julie Angwin is working on a #privacy #threatmodel for authoritarianism.
https://buttondown.com/JuliaAngwin/archive/a-threat-model-for-opposing-authoritarianism/
🩹 You Can Have the Best Security, If Your Habits Are Trash #OPSEC #Cybersecurity #PrivacyMatters #Infosec #ThreatModel #Surveillance #Metadata #DigitalAnonymity #CyberGhost #Encryption #DataLeaks #CyberHygiene #OnlineSecurity #SecureHabits #DeadSwitch