ESET Threat Report H1 2025: #ClickFix attacks surge 500%, SnakeStealer tops infostealer charts, and NFC fraud jumps 35x. Plus, chaos in the ransomware underworld and a new Android adware menace—Kaleidoscope. Dive into the full report: https://web-assets.esetstatic.com/wls/en/papers/threat-reports/eset-threat-report-h12025.pdf #ESETresearch
Security research and breaking news straight from ESET Research Labs.
#ESETresearch analyzed a campaign deployed by BladedFeline, an Iran-aligned threat actor with likely ties to #OilRig. We discovered the campaign, which targeted Kurdish and Iraqi government officials, in 2024. https://www.welivesecurity.com/en/eset-research/bladedfeline-whispering-dark/
BladedFeline, a cyberespionage group active since at least 2017, develops malware for strategic access within the Kurdistan Regional Government and the government of Iraq. We discovered BladedFeline in 2023 after it targeted Kurdish officials with the #Shahmaran backdoor.
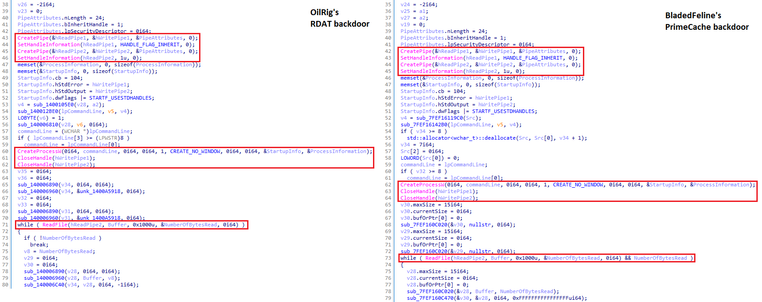
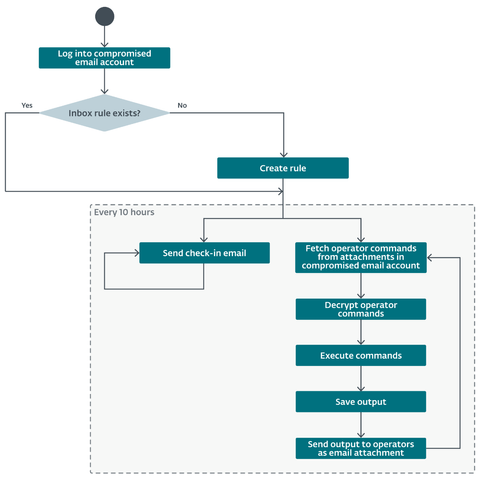
The systems compromised in the latest campaign contained the #Whisper backdoor, a malicious IIS module #PrimeCache, two reverse tunnels, and several supplementary tools. Whisper uses #MicrosoftExchange server to communicate with the attackers via email attachments.
We believe with medium confidence that BladedFeline is a subgroup of OilRig, an 🇮🇷-based APT group also known as APT34 or Hazel Sandstorm.
First, there were OilRig tools present in the systems compromised in this campaign. BladedFeline’s PrimeCache also shares code similarities with OilRig’s #RDAT backdoor. Moreover, as does OilRig, BladedFeline targets organizations in the Middle East.
IoCs will be available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/
The #FBI and #DCIS disrupted #Danabot. #ESET was one of several companies that cooperated in this effort. https://www.welivesecurity.com/en/eset-research/danabot-analyzing-fallen-empire/
#ESETresearch has been involved in this operation since 2018. Our contribution included providing technical analyses of the malware and its backend infrastructure, as well as identifying Danabot’s C&C servers. Danabot is a #MaaS #infostealer that has also been seen pushing additional malware – even #ransomware, such as #LockBit, #Buran, and #Crisis – to compromised systems.
We have analyzed Danabot campaigns all around the world and found a substantial number of distinct samples of the malware, as well as identified more than 1,000 C&Cs.
This infostealer is frequently promoted on underground forums. The affiliates are offered an administration panel application, a backconnect tool for real-time control of bots, and a proxy server application that relays the communication between the bots and the C&C server.
IoCs are available in our GitHub repo. You can expect updates with more details in the coming days. https://github.com/eset/malware-ioc/tree/master/danabot
#ESETresearch, in collaboration with #Microsoft, BitSight, Lumen, Cloudflare, CleanDNS, and GMO Registry, has helped disrupt #LummaStealer – a notorious malware-as-a-service infostealer. https://www.welivesecurity.com/en/eset-research/eset-takes-part-global-operation-disrupt-lumma-stealer
This disruption operation targeted Lumma Stealer’s C&C infrastructure, rendering much of the exfiltration network inoperative. ESET processed tens of thousands of Lumma samples to extract C&C servers and affiliate IDs. Infostealers are often precursors to major cyberattacks.
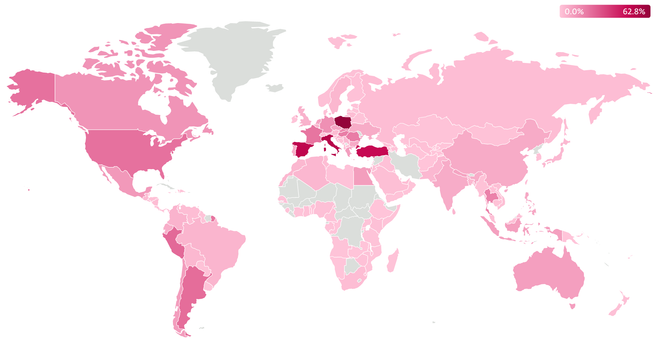
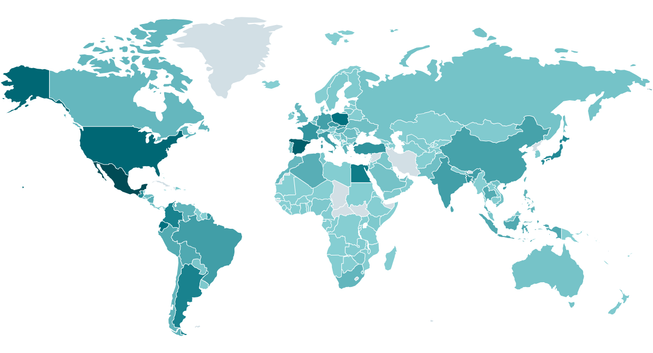
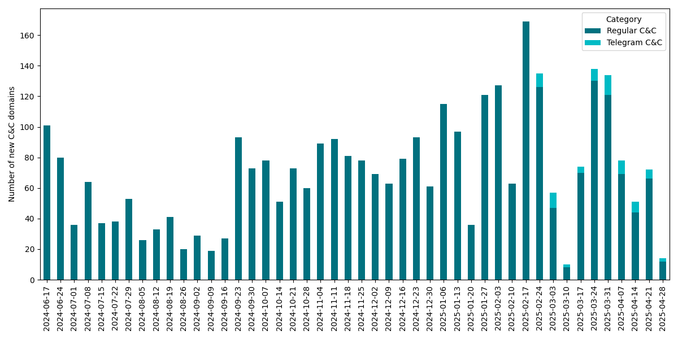
Between June 2024 and May 2025, ESET tracked 3,353 unique Lumma Stealer C&C domains, which is an average of around 74 new domains per week. The malware evolved constantly, with updates to encryption, protocols, and Steam-profile- and Telegram-based dead-drop resolvers.
#Microsoft’s Digital Crimes Unit, with the help of ESET and other partners, seized Lumma Stealer’s infrastructure and control panel. #ESET continues monitoring for possible resurgence.
IoCs available on our GitHub: https://github.com/eset/malware-ioc/tree/master/lummastealer
#ESETresearch has published its latest APT Activity Report, covering October 2024 to March 2025 (Q4 2024–Q1 2025). China-aligned groups like Mustang Panda and DigitalRecyclers continued their espionage campaigns targeting the EU government and maritime sectors.
North Korea-aligned groups, e.g., DeceptiveDevelopment, expanded their financially motivated campaigns using fake job listings and social engineering. Russian APTs intensified attacks against Ukraine and the EU, exploiting zero-day vulns. https://web-assets.esetstatic.com/wls/en/papers/threat-reports/eset-apt-activity-report-q4-2024-q1-2025.pdf
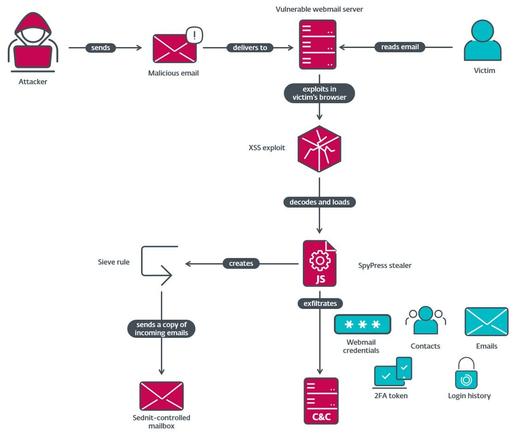
#ESETresearch publishes its investigation of Operation RoundPress, which uses XSS vulnerabilities to target high-value webmail servers. We attribute the operation to Sednit with medium confidence. https://www.welivesecurity.com/en/eset-research/operation-roundpress/
In 2023, Operation RoundPress only targeted Roundcube, but in 2024 it expanded to other webmail software including Horde, MDaemon, and Zimbra.. For MDaemon, Sednit exploited the zero-day XSS vulnerability CVE-2024-11182.
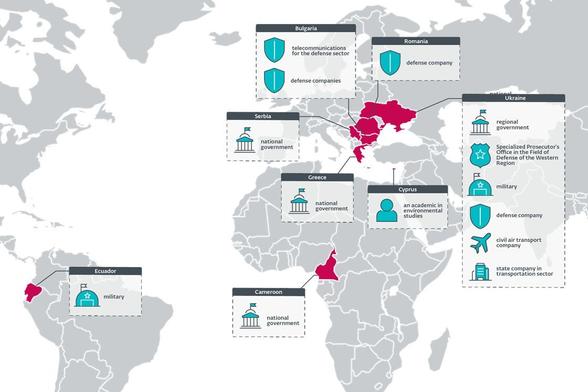
Most victims were governmental entities and defense companies in Eastern Europe, although we have observed governments in Africa, Europe, and South America being targeted as well.
Our blogpost provides an analysis of the JavaScript payloads, which we named SpyPress. They are able to steal webmail credentials, and exfiltrate contacts and email messages from the victim’s mailbox. IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/operation_roundpress 5/5
Join #ESETResearch's Damien Schaeffer at PivotCon 2025 for "Hello Zebrocy, my old friend!" on May 8 at 2pm CEST in Malaga.
Damien will discuss Zebrocy, 🇷🇺 APT group. After going silent since 2021, we discovered a 2023 attack on a 🇺🇦 governmental organization. The attack used a malicious document to download complex malware, including an obfuscated Python backdoor, keylogger, and file stealer.
By analyzing artifacts, we found similarities with older Zebrocy tools. ESET telemetry helped us attribute recent campaigns to Zebrocy, targeting Central Asia and Eastern Europe. The group uses minimal footprint tactics.
His presentation uncovers Zebrocy's multiyear espionage campaign, highlighting its evolving toolset and stealthy operations. The group's infrastructure is recalibrated for each campaign, aiming to maintain access for cyberespionage. Save the date: https://pivotcon.org/agenda-2025/
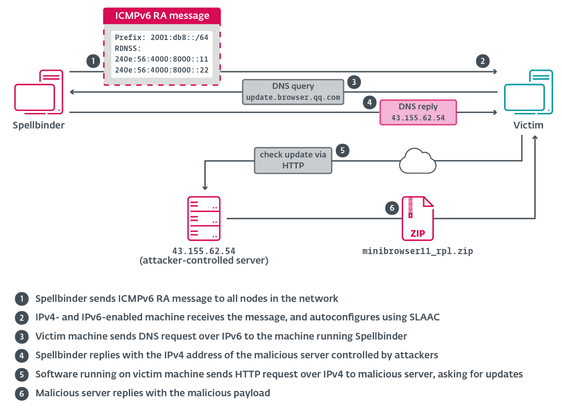
#ESETResearch analyzed the toolset of the China-aligned APT group that we have named #TheWizards. It can move laterally on compromised networks by performing adversary-in-the-middle (AitM) attacks to hijack software updates. https://www.welivesecurity.com/en/eset-research/thewizards-apt-group-slaac-spoofing-adversary-in-the-middle-attacks/
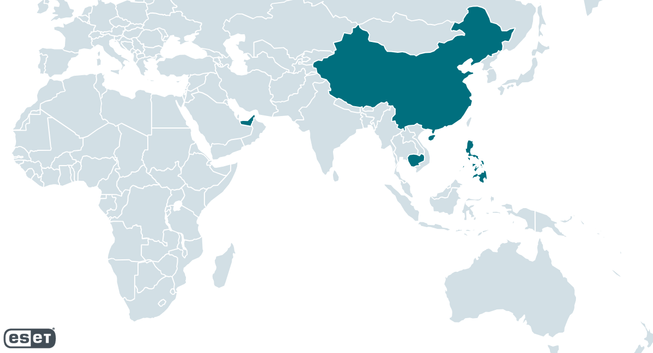
Since at least 2022, the group has targeted individuals, companies, and unknown entities in the Philippines, the United Arab Emirates, Cambodia, mainland China, and Hong Kong.
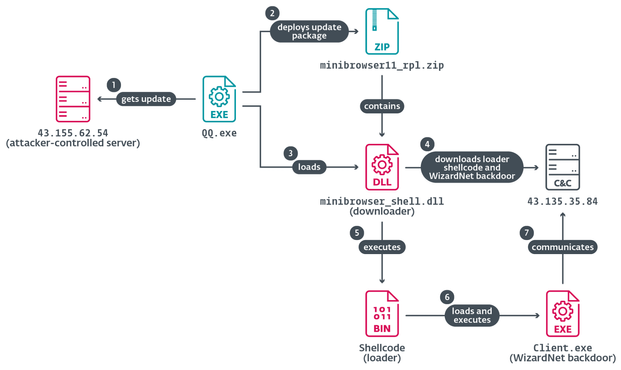
#TheWizards deploy a tool we have named #Spellbinder, which implements IPv6 SLAAC spoofing to redirect IPv6 traffic to the machine running Spellbinder, making it act as a malicious IPv6-capable router.
Spellbinder intercepts DNS queries associated with update domains for Chinese software. We focus on a recent case in which an update of Tencent QQ was hijacked to deploy TheWizards’ signature backdoor, WizardNet.
In our blogpost, we also discuss links we uncovered between #TheWizards and the Chinese company Dianke Network Security Technology, also known as UPSEC.
IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/thewizards
Join #ESETResearch's Romain Dumont at BSides Calgary for "Reverse One Zero Day, Get One Free!" on May 2 at 8pm local time.
In his talk, Romain will explore how ESET found a zero-day vulnerability in WPS Office for Windows (CVE-2024-7262) exploited by APT-C-60 for espionage. This one-click remote code execution bug targets the software suite, popular in Asia with 500M users.
Our analysis revealed weaponized MHTML-formatted spreadsheets exploiting a path traversal bug due to poor input sanitization. Developers used their knowledge of WPS Office and Windows internals to bypass constraints.
Further analysis of the patch led us to the discovery of a logic flaw introduced by the latter. We demonstrate how a single bit created an alternate path for arbitrary code execution (CVE-2024-7263). 📅 Save the date ➡️ hackertracker.app/event/?conf=BSIDESCALGARY2025&event=60453
Join #ESETresearch and our very own @matthieu_faou during #Northsec conference in Montreal for “Weaponizing XSS: Cyberespionage tactics in webmail exploitation” talk. Learn how XSS vulnerabilities let attackers inject malicious scripts into webmails.
#ESET team spent 2 years studying these vulnerabilities in webmail portals, finding zero-day flaws in Roundcube & MDaemon. Discover how Russia-aligned Sednit, GreenCube, and Belarus-aligned Winter Vivern exploited XSS flaws in Roundcube, Zimbra,MDaemon & Horde to steal emails from high-value targets.
Don't miss the presentation on May 15 at 13:45 Montreal time. #CyberSecurity #Infosec https://nsec.io/session/2025-weaponizing-xss-cyberespionage-tactics-in-webmail-exploitation.html
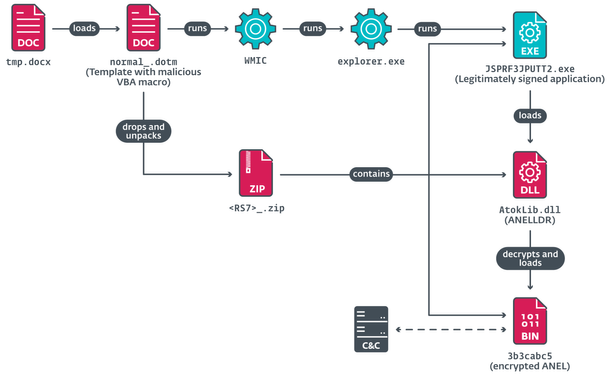
#ESETresearch noticed two #MirrorFace Excel documents, known as #ROAMINGMOUSE, were uploaded to VirusTotal from #Taiwan in March 2025. The documents contain a malicious VBA macro that deploys #ANEL backdoor on the compromised machine. @dbreitenbacher
The contents of the documents are written in traditional Chinese and the date used follows the Republic of China calendar. Based on this data and other information available to ESET, we assess with medium confidence that the target was a Taiwanese research institute.
Even though MirrorFace has been previously reported on targeting a Taiwanese entity, this is for the first time we don’t see any relation to Japan.
Our investigation indicates that both documents were used to target the same institute. MirrorFace employed a call-to-action textbox, asking targets to press “Enable editing” and then “Enable content” buttons to show the data in the worksheet.
Using multiple different malicious documents to compromise the same entity is an approach that was also observed in 2024 in “Case 1: Japanese research institute” described in our blogpost https://www.welivesecurity.com/en/eset-research/operation-akairyu-mirrorface-invites-europe-expo-2025-revives-anel-backdoor/.
The overall compromise chain, leading to the execution of #ANEL to establish the initial foothold, remained the same as some observed in 2024. In particular, the approach was described as “Case 1” in Trend Micro’s report https://www.trendmicro.com/en_us/research/24/k/return-of-anel-in-the-recent-earth-kasha-spearphishing-campaign.html.
The overall compromise chain, leading to the execution of #ANEL to establish the initial foothold, remained the same as some observed in 2024. In particular, the approach was described as “Case 1” in Trend Micro’s report https://www.trendmicro.com/en_us/research/24/k/return-of-anel-in-the-recent-earth-kasha-spearphishing-campaign.html.
Besides the documents, a sample of #ANELLDR loader and a sample of #FaceXInjector were uploaded to VirusTotal from Taiwan around the same time as well.
IoCs
1BAC9E61C0D433964972BC91A5F38F31B85558C1 (ROAMINGMOUSE)
634D52E10E168A61C8201130F44925CC497C1251 (ROAMINGMOUSE)
E5F20192DB09EA033FEDD9CCEB782321EBB9C66E (FaceXInjector)
948CA0DAC99470775523809C1E7E60740B70C0FD (ANELLDR)
C&Cs:
64.176.34[.]120 (ANEL)
192.46.215[.]56 (ANEL)
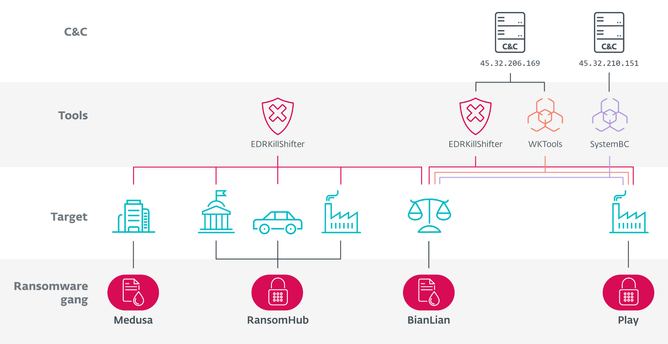
#ESETresearch discovered previously unknown links between the #RansomHub, #Medusa, #BianLian, and #Play ransomware gangs, and leveraged #EDRKillShifter to learn more about RansomHub’s affiliates. @SCrow357 https://www.welivesecurity.com/en/eset-research/shifting-sands-ransomhub-edrkillshifter/
RansomHub emerged in February 2024 and in just three months reached the top of the ransomware ladder, recruiting affiliates from disrupted #LockBit and #BlackCat. Since then, it dominated the ransomware world, showing similar growth as LockBit once did.
Previously linked to North Korea-aligned group #Andariel, Play strictly denies operating as #RaaS. We found its members utilized RansomHub’s EDR killer EDRKillShifter, multiple times during their intrusions, meaning some members likely became RansomHub affiliates.
BianLian focuses on extortion-only attacks and does not publicly recruit new affiliates. Its access to EDRKillShifter suggests a similar approach as Play – having trusted members, who are not limited to working only with them.
Medusa, same as RansomHub, is a typical RaaS gang, actively recruiting new affiliates. Since it is common knowledge that affiliates of such RaaS groups often work for multiple operators, this connection is to be expected.
Our blogpost also emphasizes the growing threat of EDR killers. We observed an increase in the number of such tools, while the set of abused drivers remains quite small. Gangs such as RansomHub and #Embargo offer their killers as part of the affiliate program.
IoCs available on our GitHub: https://github.com/eset/malware-ioc/tree/master/ransomhub
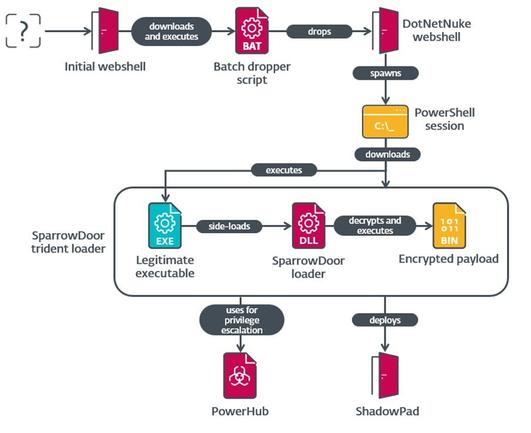
In July 2024, #ESETresearch discovered that the China-aligned #FamousSparrow APT group, thought at the time to have been inactive since 2022, compromised the network of a US trade group and a Mexican research institute. https://www.welivesecurity.com/en/eset-research/you-will-always-remember-this-as-the-day-you-finally-caught-famoussparrow/
While helping the 🇺🇸 company remediate the compromise, we discovered FamousSparrow’s toolset hidden within the network. It included two previously undocumented versions of the group’s flagship backdoor, #SparrowDoor, one of them modular.
Both of these versions are a significant improvement over the older ones, especially in terms of code quality and architecture, implementing parallelization of time-consuming commands.
This campaign is also the first documented time that FamousSparrow used #ShadowPad, a privately sold modular backdoor known to only be supplied to threat actors affiliated with China.
IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/famoussparrow
#ESETresearch published its investigation of Operation FishMedley, a global espionage operation by the China-aligned APT group FishMonger. We identified seven victims – including governments, NGOs, and think tanks – across Asia, Europe, and the US.
https://www.welivesecurity.com/en/eset-research/operation-fishmedley/
The same operation was the subject of a recent US DOJ indictment against I SOON employees and officers of China’s Ministry of Public Security. #ESETresearch independently determined that FishMonger is operated by the Chinese contractor I SOON.
https://www.justice.gov/opa/pr/justice-department-charges-12-chinese-contract-hackers-and-law-enforcement-officers-global
IoCs available in our GitHub: https://github.com/eset/malware-ioc/tree/master/fishmonger
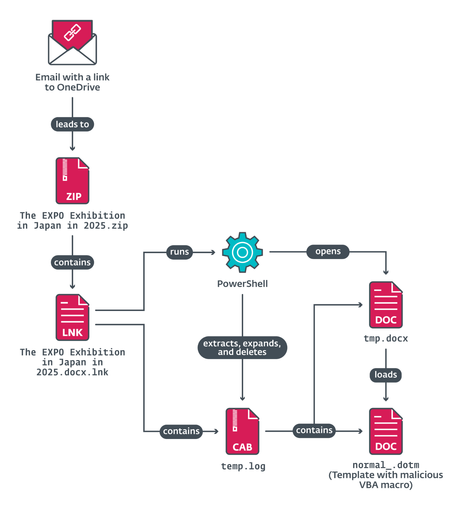
#ESETresearch has uncovered the #MirrorFace Operation AkaiRyū, which extends the group’s usual focus beyond Japan into Europe. The initial lure centered around Expo 2025 in Japan, compromising a Central European diplomatic institute.
https://www.welivesecurity.com/en/eset-research/operation-akairyu-mirrorface-invites-europe-expo-2025-revives-anel-backdoor/
Surprisingly, #MirrorFace used #ANEL – a backdoor historically linked only to #APT10 – highlighting a shift in the group’s tactics and reinforcing suspicions that MirrorFace could be part of the APT10 umbrella.
Operation AkaiRyū began with targeted spearphishing emails referencing the victim’s past correspondence and Expo 2025 , persuading recipients to download malicious attachments.
Once the files were opened, a layered compromise chain ensued . Collaborating with the victim allowed us to perform in-depth analysis, shedding light on MirrorFace’s post-compromise behavior – from credential harvesting to dropping additional tools for lateral movement.
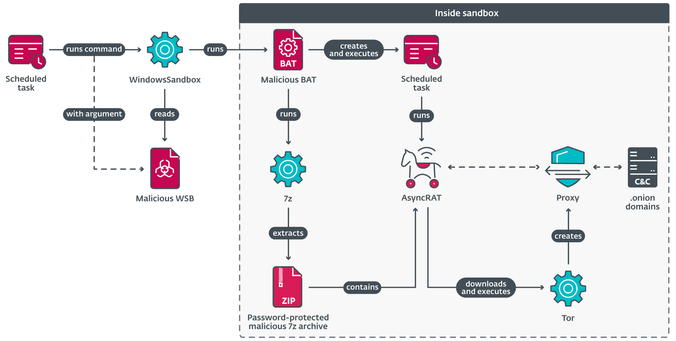
#MirrorFace used an intricate execution chain to stealthily run a highly tweaked #AsyncRAT within #WindowsSandbox, hampering detection efforts. This is the first time we’ve seen MirrorFace employ AsyncRAT.
In another twist, #MirrorFace utilized #VSCode remote tunnels, a tactic enabling covert access and command execution on compromised machines. This approach has also been seen with other China-aligned cyberespionage groups.
The group primarily leveraged #ANEL as a first-stage backdoor, #HiddenFace – MirrorFace’s flagship backdoor – was dropped later in the attack to bolster persistence . Notably absent this time was #LODEINFO, which #MirrorFace typically employs.
We presented our findings about Operation AkaiRyū conducted by #MirrorFace at @jpcert_ac on January 22, 2025: https://jsac.jpcert.or.jp.
IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/mirrorface
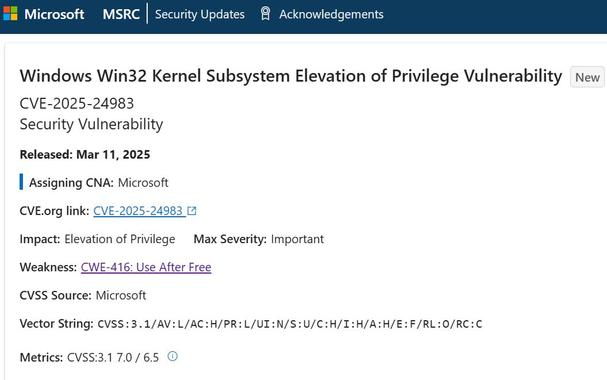
#ESETresearch has discovered a zero day exploit abusing #CVE-2025-24983 vulnerability in the Windows kernel 🪟 to elevate privileges (#LPE). First seen in the wild in March 2023, the exploit was deployed through #PipeMagic backdoor on the compromised machines.
The exploit targets Windows 8.1 and Server 2012 R2. The vulnerability affects OSes released before Windows 10 build 1809, including still supported Windows Server 2016. It does not affect more recent Windows OSes such as Windows 11.
The vulnerability is a use after free in Win32k driver. In a certain scenario achieved using the #WaitForInputIdle API, the #W32PROCESS structure gets dereferenced one more time than it should, causing UAF. To reach the vulnerability, a race condition must be won.
The patches were released today. Microsoft advisory with security update details is available here:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24983
#ESETresearch has released DelphiHelper, a plugin 🔌 for #IDAPro that aids in analyzing Delphi binaries.
Check it out on ESET’s GitHub at https://github.com/eset/DelphiHelper
Proud to be recognized among the notable submissions of the 2024 https://x.com/HexRaysSA Plugin Contest: https://hex-rays.com/blog/2024-plugin-contest-winners
#ESETresearch analyzed a campaign by #DeceptiveDevelopment targeting developers with trojanized coding tests. Posing as recruiters, the operators approach their targets on job-hunting platforms, aiming to steal their cryptocurrency wallets and more.
https://www.welivesecurity.com/en/eset-research/deceptivedevelopment-targets-freelance-developers/
DeceptiveDevelopment is a 🇰🇵-aligned activity cluster. The attackers target software developers on 🪟 Windows, 🐧Linux, and 🍎 macOS, regardless of geographical location, in order to maximize profits.
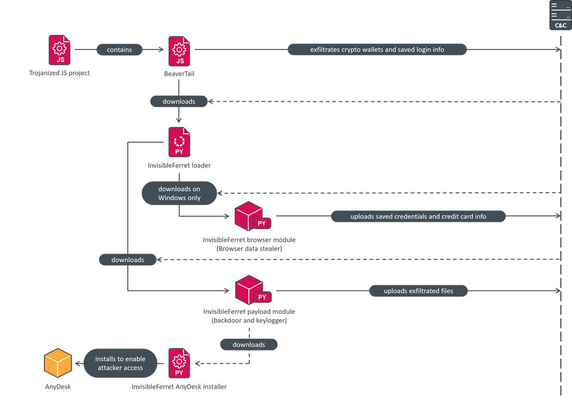
The campaign primarily uses two malware families – the first, 🦫 BeaverTail, acts as a simple login stealer, extracting browser databases containing saved logins, and is a downloader for the second stage, InvisibleFerret.
InvisibleFerret is modular 🐍 Python-based malware that includes spyware and backdoor components, and is also capable of downloading the legitimate AnyDesk remote management and monitoring software for post-compromise activities.
While DeceptiveDevelopment’s toolset has already been analyzed by https://x.com/Unit42_Intel and https://x.com/GroupIB_TI, our analysis contains details that have not been publicly reported before.
You can find the IoCs in our GitHub repo:
https://github.com/eset/malware-ioc/tree/master/deceptivedevelopment
𝗨𝗣𝗗𝗔𝗧𝗘: The threat was first reported by Polish CSIRT 🇵🇱
https://x.com/CSIRT_KNF/status/1887474108323037617
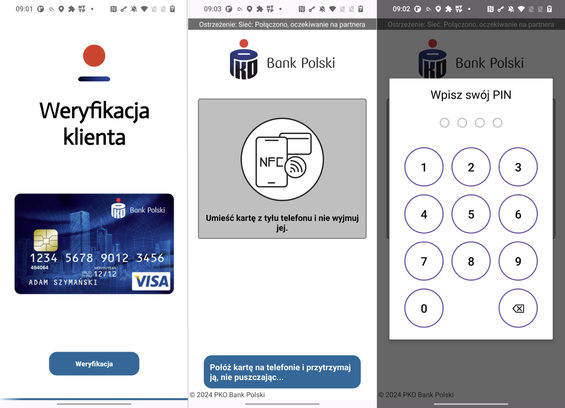
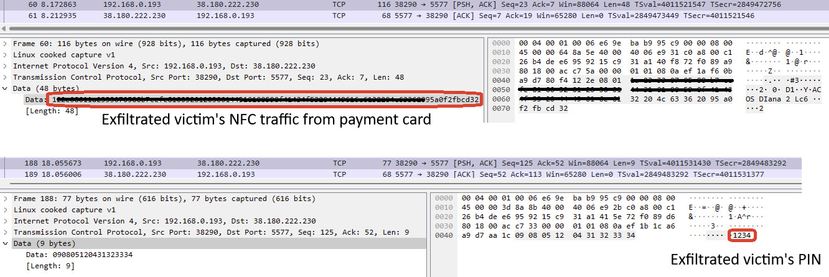
#BREAKING #ESETresearch NFC Android malware impersonates banking app in 🇵🇱 Poland. #NGate malware impersonates a banking verification application to steal NFC data and PIN from victims’ physical payment card. x.com/LukasStefanko
TThe threat actor can then use it to withdraw money from ATM via contactless terminal without having payment card.
More information about NGate malware: https://www.welivesecurity.com/en/eset-research/ngate-android-malware-relays-nfc-traffic-to-steal-cash/
IoCs:
C&C: 38.180.222[.]230:5577
Sample: 6A41008744498A3EDDA0BDF763ADC7F157441E1D
Detection name: Android/Spy.NGate.L