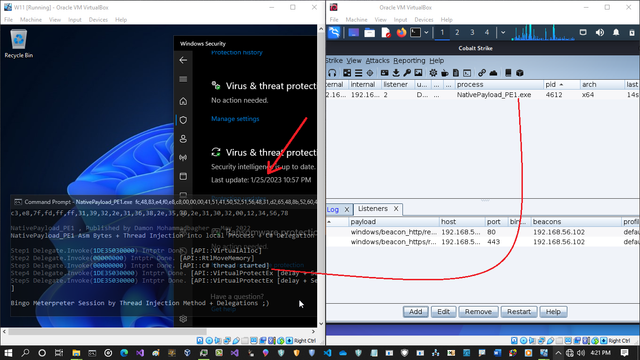
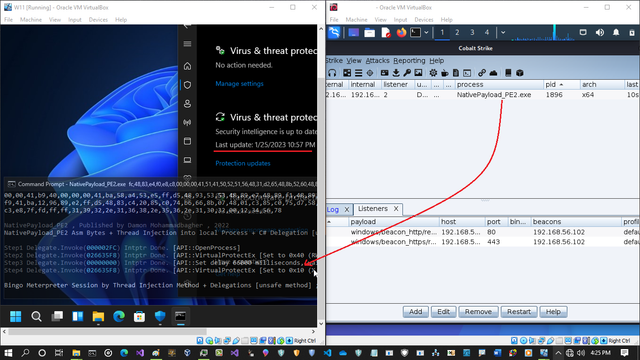
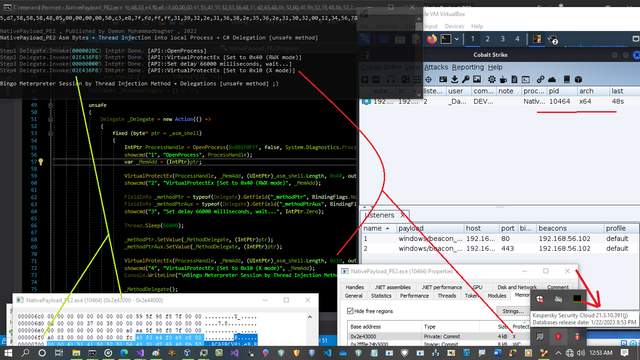
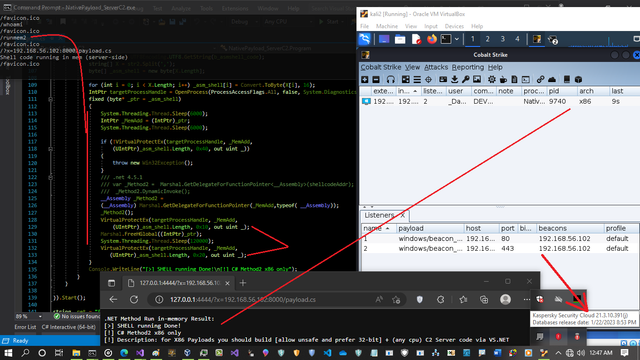
🚨 Must-Read for Cybersecurity Enthusiasts! 🚨
📘 The InfoSec Diaries 📘 – a riveting series of short stories that plunge you into the heart of real-life Information Security adventures. From the high-stakes world of Pen Testing and Blue Teaming to the meticulous detail of Digital Forensics, these tales offer an unprecedented look behind the scenes of cybersecurity's most thrilling operations.
🔍 Why Read The InfoSec Diaries?
Real-Life Scenarios: Explore authentic stories based on real incidents and challenges faced by professionals in the field.
Diverse Perspectives: Whether you’re rooting for the defenders in Blue Teaming, strategizing alongside Pen Testers, or uncovering truths with Digital Forensics, there's a story for every cybersecurity enthusiast.
Learn and Grow: Each story is not just a narrative but a lesson in cybersecurity practices, vulnerabilities, and defensive tactics.
📚 Perfect for both seasoned professionals and newcomers to the field, The InfoSec Diaries serves as both a learning resource and an exciting dive into the depths of what it means to protect the digital world.
🔗 Dive into the adventure now: https://infosecdiaries.com
#InfoSecDiaries #Cybersecurity #PenTesting #BlueTeaming #DigitalForensics #InfoSec #SecurityAwareness