DATE: MAY-25-2025
TITLE: CYBERSECURITY INCIDENTS REPORT
MORE INFORMATION AT: https://thedailytechfeed.com/daily-report/cybersecurity-report-may-05-2025.html
#CyberSecurity #ThreatIntel #Ransomware #DDoS #Hacktivism #DataBreach #CyberThreats #InfoSec #CyberRisk #DarkWeb #IncidentResponse #CISO #CyberReport #APT #Malware #Phishing #ZeroDay #CyberDefense #Threat #Breaches #Infrastructure #Hacktivist #Cybercriminal #Disruption #Vulnerabilities #SCADA #IOC #ICS #Espionage #Intelligence #Security #MFA #Detection #EDR #AI #Fraud #Privacy #Exploits #Theft
#DDOS
[May-25-2025] Daily Cybersecurity Threat Report
#CyberSecurity #ThreatIntel #Ransomware #DDoS #Hacktivism #DataBreach #CyberThreats #InfoSec #CyberRisk #DarkWeb #IncidentResponse #CISO #CyberReport #APT #Malware #Phishing #ZeroDay #CyberDefense #Threat #Breaches #Infrastructure #Hacktivist #Cybercriminal #Disruption #Vulnerabilities #IOC #ICS #Defacement #Espionage #Financial #Network #Systems #Security #MFA #EDR #Darkweb #AI #Fraud #Privacy #Exploits
More Information at: https://thedailytechfeed.com/may-25-2025-daily-cybersecurity-threat-report/
Новости кибербезопасности за неделю с 19 по 25 мая 2025
Все самое интересное из мира кибербезопасности /** с моими комментариями На этой неделе в новости про: побитие рекорда DDOS в России; итоги соревнований Pwn2Own 2025; то, что Signal не доверяет ИИ Windows, аWSL выходит в Open Source и ещё немного новостей, но только самое интересное и важное!
https://habr.com/ru/articles/912316/
#информационная_безопасность #новости #wsl #signal #ddos #sudo
My #Forgejo instance is currently under attack by #LLM crawlers again.
Maybe I misconfigured #Anubis or something, but I keep getting requests from various IP addresses every seconds to expensive endpoints of my instance, all impersonating legitimate users.
I've been trying to block IP addresses manually, but the attack is so well distributed, that each request comes from a different address.
After an attempt at configuring automatic blocking of these bots, I currently have around ~1300 single IP addresses blocked, and it's expanding every minute.
[May-23-2025] Daily Cybersecurity Threat Report
#CyberSecurity #ThreatIntel #Ransomware #DDoS #Hacktivism #DataBreach #CyberThreats #InfoSec #CyberRisk #DarkWeb #IncidentResponse #CISO #CyberReport #APT #Malware #Phishing #ZeroDay #CyberDefense
https://thedailytechfeed.com/may-24-2025-daily-cybersecurity-threat-report/
KrebsOnSecurity Hit With Near-Record 6.3 Tbps #DDoS https://krebsonsecurity.com/2025/05/krebsonsecurity-hit-with-near-record-6-3-tbps-ddos/
Sicherheitsexperte #BrianKrebs Ziel von #DDoS-Attacke mit 6,3 Terabit pro Sekunde | Security https://www.heise.de/news/Sicherheitsexperte-Brian-Krebs-Ziel-von-DDoS-Attacke-mit-6-3-Terabit-pro-Sekunde-10393206.html #Aisuru #Botnet
X volta a falhar: Utilizadores relatam problemas há mais de um dia
🔗 https://tugatech.com.pt/t67082-x-volta-a-falhar-utilizadores-relatam-problemas-ha-mais-de-um-dia
#ddos #despedimentos #elonmusk #mundo #online #segurança #twitter
Operation Endgame 2.0
International law enforcement agencies have taken additional actions in Operation Endgame, targeting cybercriminal organizations, particularly those behind DanaBot. DanaBot is a powerful modular malware family written in Delphi, capable of keylogging, capturing screenshots, recording desktop videos, exfiltrating files, injecting content into web browsers, and deploying second-stage malware. It operates as a Malware-as-a-Service platform, enabling various attacks. DanaBot has been used in targeted attacks against government officials in the Middle East and Eastern Europe, and for DDoS attacks against Ukrainian servers. The malware implements a custom binary protocol encrypted with RSA and AES, and uses hardcoded C2 servers with Tor as a backup communication channel. Over 50 nicknames have been associated with DanaBot affiliates.
Pulse ID: 683046e8073360953a9307d2
Pulse Link: https://otx.alienvault.com/pulse/683046e8073360953a9307d2
Pulse Author: AlienVault
Created: 2025-05-23 09:59:04
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#Browser #CyberSecurity #DDoS #DanaBot #Delphi #DoS #EasternEurope #Europe #Government #InfoSec #LawEnforcement #Malware #MalwareAsAService #MiddleEast #OTX #OpenThreatExchange #RAT #RCE #UK #Ukr #Ukrainian #bot #AlienVault
Operation Sindoor: Anatomy of a High-Stakes Cyber Siege
Operation Sindoor, a coordinated cyber campaign targeting India's critical sectors, involved state-sponsored APT activity and hacktivist operations. The attack utilized spear phishing, malicious scripts, website defacements, and data leaks. APT36, a Pakistan-aligned threat group, employed advanced tactics including the Ares RAT for persistent access. The campaign targeted defense, government IT, healthcare, telecom, and education sectors. Multiple hacktivist groups participated in DDoS attacks and defacements. The operation showcased a convergence of cyber espionage and ideological warfare, significantly impacting national cybersecurity and trust. It underscored the need for enhanced threat intelligence and robust incident response frameworks to counter evolving hybrid threats.
Pulse ID: 683046e942d0f021c007c02b
Pulse Link: https://otx.alienvault.com/pulse/683046e942d0f021c007c02b
Pulse Author: AlienVault
Created: 2025-05-23 09:59:05
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#AresRAT #CyberSecurity #DDoS #DoS #Education #Espionage #Government #Hacktivist #Healthcare #ICS #India #InfoSec #NATO #OTX #OpenThreatExchange #Pakistan #Phishing #RAT #Rust #SpearPhishing #Telecom #bot #AlienVault
DDoS-Angriff: Périódico Noroeste #DDoS #Ausfall #TeamInfoSec #cyberangriff https://www.security-incidents.de/sicherheitsvorfaelle/ddos_angriff_périódico-noroeste-9531.php
"KrebsOnSecurity last week was hit by a near record distributed denial-of-service (DDoS) attack that clocked in at more than 6.3 terabits of data per second (a terabit is one trillion bits of data). The brief attack appears to have been a test run for a massive new Internet of Things (IoT) botnet capable of launching crippling digital assaults that few web destinations can withstand. Read on for more about the botnet, the attack, and the apparent creator of this global menace."
https://krebsonsecurity.com/2025/05/krebsonsecurity-hit-with-near-record-6-3-tbps-ddos/
Pourquoi les attaques DDoS sont-elles si fréquentes ? Motivations politiques, financières ou commerciales : décryptage d’un phénomène en forte hausse. - Article par Bearstech #DDoS #Network https://bearstech.com/societe/blog/attaques-ddos-pourquoi-tant-de-haine
🛡️ KrebsOnSecurity Hit With Near-Record 6.3 Tbps DDoS
「 The brief attack appears to have been a test run for a massive new Internet of Things (IoT) botnet capable of launching crippling digital assaults that few web destinations can withstand 」
https://krebsonsecurity.com/2025/05/krebsonsecurity-hit-with-near-record-6-3-tbps-ddos/
#CENTR #dDoS Interesting talk since it was not a talk: after a short introduction, people in the room were told to gather in small groups (with no group hving two persons from the same domain registry), discuss on one of the proposed statements, and synthetize their discussion at the end.
Everybody agrees that we should share more information (heard many times in the last 25 years at CENTR...)
Telegram Is Cooperating With Authorities, For Now - This is good news for the benign side of the cyber world. What we in the #DDoS mitigation industry observe are Telegram channels for e.g. #marketplaces for #DDoSforhire services or #threatactor coordination.
Seeing that #Telegram seizes to be the safe haven for shady, or straight up illegal activities that are a burden to the #Internet at large is really good news.
Krebs on Security: KrebsOnSecurity Hit With Near-Record 6.3 Tbps DDoS. “KrebsOnSecurity last week was hit by a near record distributed denial-of-service (DDoS) attack that clocked in at more than 6.3 terabits of data per second (a terabit is one trillion bits of data). The brief attack appears to have been a test run for a massive new Internet of Things (IoT) botnet capable of launching […]
#CENTR #DNS #dDoS "Towards a more effective strategy to deflect DDoS attacks on critical DNS anycast infrastructure"
With a DNSCON scale for problems (DNSCON 5 is all good, DNSCON 2, you start RTBH, DNSCON 1 is complete failure, see info on https://status.sidn.com).
#dDoS Ah, encore des français dans les cibles de NoName, aujourd'hui : https://social.circl.lu/@NoName57Bot/114550014260472722
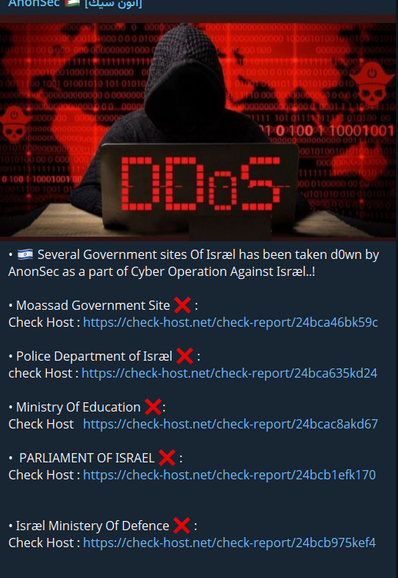
🚨DDoS Alert🚨
AnonSec claim to have taken down 5 Israeli Government websites.
The websites seem to be down at this moment.
Actor: AnonSec
Method: #DDoS
Date: April 7, 2025
#Hacktivism #CyberAttack #CyberThreat #Darkweb #AnonSec #CyberNews #News #NewsUpdate #HackerNews #SpyoSecure #SpyoSecureNews #OpIsrael

![[May-25-2025] Daily Cybersecurity Threat Report
#CyberSecurity #ThreatIntel #Ransomware #DDoS #Hacktivism #DataBreach #CyberThreats #InfoSec #CyberRisk #DarkWeb #IncidentResponse #CISO #CyberReport #APT #Malware #Phishing #ZeroDay #CyberDefense #Threat #Breaches #Infrastructure #Hacktivist #Cybercriminal #Disruption #Vulnerabilities #IOC #ICS #Defacement #Espionage #Financial #Network #Systems #Security #MFA #EDR #Darkweb #AI #Fraud #Privacy #Exploits
More Information at: https://thedailytechfeed.com/may-25-2025-daily-cybersecurity-threat-report/](https://files.mastodon.social/media_attachments/files/114/569/235/776/780/007/small/b8566d8de7d26d32.webp)