@micahflee See what you've done?
"the collection of mobile device data from some custodians [including "two cabinet-level secretaries" and other "senior White House officials"] has encountered logistical challenges, and Defendants are working with relevant IT personnel to understand the scope of those challenges and predict a likely timeline for resolution."
https://storage.courtlistener.com/recap/gov.uscourts.mdd.578815/gov.uscourts.mdd.578815.167.0.pdf
#telemessage #abregogarcia
#TeleMessage
🚨 BREAKING NEWS: #TeleMessage is used by everyone from DC's finest to Silicon Valley's finest—because who doesn't love a good security breach? 🤦♂️ Congrats, your secrets are now open source #research tools! 🎉🔓
https://micahflee.com/telemessage-customers-include-dc-police-andreesen-horowitz-jp-morgan-and-hundreds-more/ #SecurityBreach #OpenSource #DC #SiliconValley #HackerNews #ngated
TeleMessage Customers Include DC Police, Andreessen Horowitz, JP Morgan,Hundreds
#HackerNews #TeleMessage #DC #Police #AndreessenHorowitz #JPMorgan #Customers #News
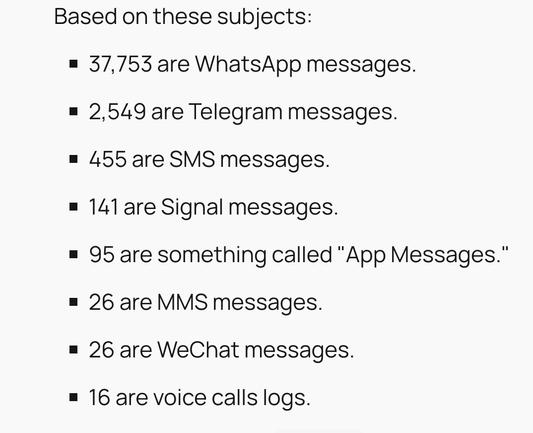
🎉 Behold, the latest gift to the #open-source world: a tool that helps you make sense of the #TeleMessage data leak, because who wouldn't want to dive into the dumpster fire 🔥 that is yet another insecure messaging app? 🤡 Just don't forget to bring your own data—after all, that's half the fun! 🎁
https://micahflee.com/telemessage-explorer-a-new-open-source-research-tool/ #data-leak #insecure-messaging #app-security #data-analysis #HackerNews #ngated
TeleMessage Explorer: a new open-source research tool
https://micahflee.com/telemessage-explorer-a-new-open-source-research-tool/
#HackerNews #TeleMessage #Explorer #open-source #research #tool #technology #innovation #HackerNews
»How the #Signal Knockoff App #TeleMessage Got #Hacked in 20 Minutes.« https://www.wired.com/story/how-the-signal-knock-off-app-telemessage-got-hacked-in-20-minutes/?eicker.news #tech #media #news
#TeleMessage, der obskure Anbieter, der Nachrichten von #WhatsApp #Signal #SMS #SGNL #WeChat und auch #Telegram archivierte hat KEINE Nachrichten von #Threema abgreifen können! Soviel also zur "Sicherheit" von US #Messenger.... micahflee.com/telemessage-... #Datenschutz #MetaAI #Privatsphäre
The recent hack of TeleMessage covers a broader spectrum of government officials than previously thought.
A hacker intercepted communications data from over 60 government officials, including disaster responders, diplomatic staff, and White House personnel.
The stolen data included messages from May 4, 2025, and some of them were confirmed authentic by the recipients.
Ever wonder how easy it would be for proprietary software like #WhatsApp to get around the end-to-end encryption? #TeleMessage provides a real world example. This is why there is no replacement for Free Software when it comes to privacy.
More on the #telemessage DUMP!
"... found a message sent to a Signal group called "US / China AI Race." The Signal group had 100 people in it. [... ] many of the group members hold prominent positions at major universities, the defense industry, and the military, [...]. "
#signalgate #ai
RE: https://bsky.app/profile/did:plc:uzucgmkg2y5vbkqnbv2on7g3/post/3lpq5aykczs2m
Hack of Signal App Clone Telemessage Hits US Responders, Diplomats; Data Stolen Across US Government
#CyberSecurity #DataBreach #USGovt #TeleMessage #SignalApp #NationalSecurity #CISA #Hacking #Privacy #InfoSec #GovTech #Signalgate #Signal
A week after that #hack, the #CISA recommended that users "discontinue use of the product" barring any mitigating instructions about how to use the app from #Smarsh.
Jake Williams, a fmr #NationalSecurity Agency #cyber specialist, said that, even if the intercepted text messages were innocuous, the wealth of #metadata - the who & when of the #leaked conversations & chat groups - posed a #counterintelligence risk.
A #CBP spox repeated a past stmnt noting that it had disabled #TeleMessage & was investigating.
Federal contracting data shows that #State & #DHS have had contracts w/TeleMessage in recent years, as has the #CDC. A CDC spox told Reuters in an email that the agency piloted the software in 2024 to assess its potential for records management requirements "but found it did not fit our needs." The status of the other contracts wasn't clear.
The White House said in a stmnt that it was "aware of the cyber security incident at #Smarsh" but didn't offer comment on its use of the platform. #State didn't respond. The #SecretService said #TeleMessage products had been used "by a small subset of Secret Service employees" & that it was reviewing the situation. #FEMA said in an email that it had "no evidence" that its info had been compromised. It didn't respond when sent copies of internal FEMA msgs.
Reuters could not ascertain how #TeleMessage had been used by each agency. The service - which takes versions of popular apps & allows their messages to be archived in line w/government rules - has been suspended since May 5, when it went offline "out of an abundance of caution." TeleMessage's owner, the Portland, Oregon-based digital communications firm #Smarsh, did not respond to requests for comments about the #leaked #data.
#Trump #NationalSecurity #Signalgate #Signal #InfoSec #idiocracy
One of the intercepted texts' recipients - an applicant for aid from #FEMA confirmed to Reuters that the #leaked message was authentic; a financial services firm whose messages were similarly intercepted also confirmed their authenticity.
Based on its limited review, Reuters uncovered nothing that seemed clearly sensitive & did not uncover chats by #MikeWaltz or other cabinet ofcls.
#Trump #NationalSecurity #Signalgate #Signal #Telemessage #InfoSec #idiocracy
Once little known outside government and finance circles, #TeleMessage drew media attention after an April 30 Reuters photograph showed #MikeWaltz checking TeleMessage's version of the privacy-focused app #Signal during a cabinet meeting.
While Reuters could not verify the entire contents of the TeleMessage trove, in more than half a dozen cases the news agency was able to establish that the phone numbers in the #leaked #data were correctly attributed to their owners.
Reuters identified >60 unique govt users of the messaging platform #TeleMessage in a cache of #leaked #data provided by Distributed Denial of Secrets, a US nonprofit whose mission is to archive #hacked & leaked documents in the public interest. The trove included material from disaster responders, #customs ofcls, several US diplomatic staffers, at least 1 #WhiteHouse staffer & members of the #SecretService.
Exclusive: Hacker who breached communications app used by #Trump aide stole data across US govt
A #hacker who breached the comms service used by fmr Trump #NationalSecurity adviser [& current UN ambassador] #MikeWaltz earlier this month intercepted messages from a broader swath of ofcls than previously reported, potentially raising the stakes of a breach that has already drawn questions about #DataSecurity in the Trump admin.
#TeleMessage #Signalgate #InfoSec #idiocracy
https://www.reuters.com/world/us/hacker-who-breached-communications-app-used-by-trump-aide-stole-data-across-us-2025-05-21/