Stealthy .NET Malware: Hiding Malicious Payloads as Bitmap Resources
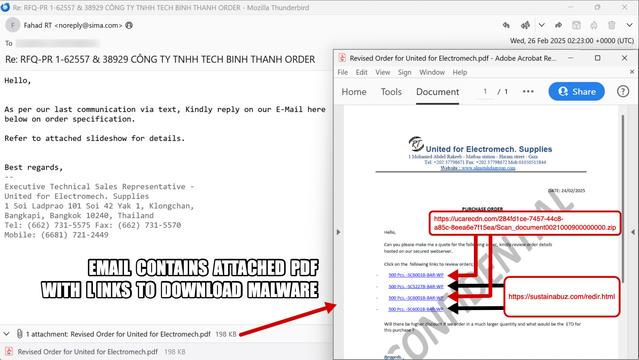
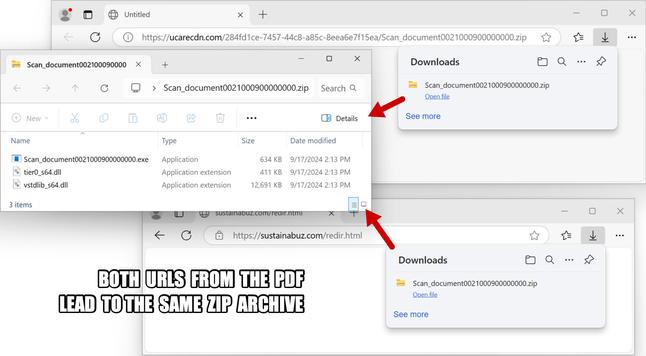
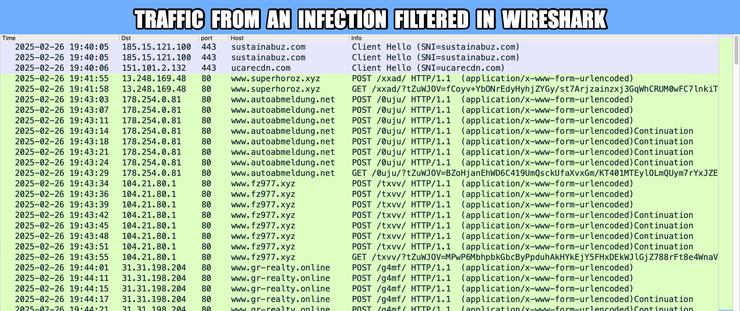
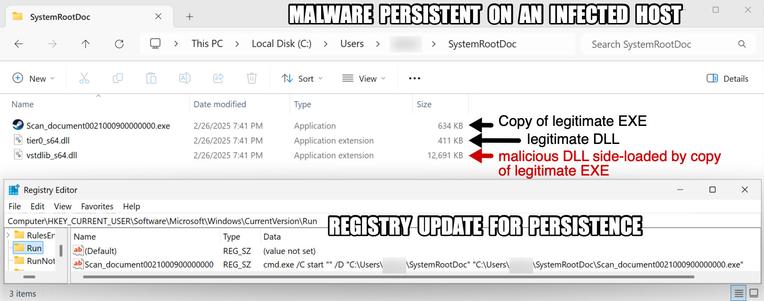
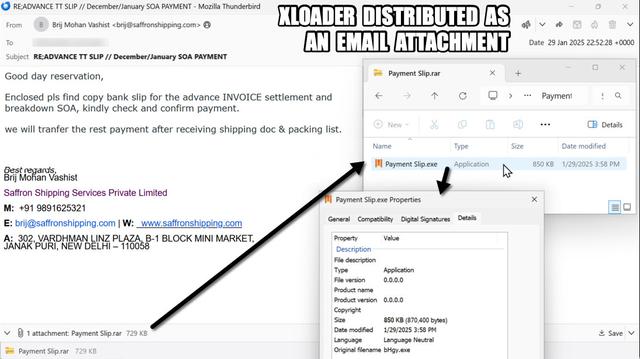
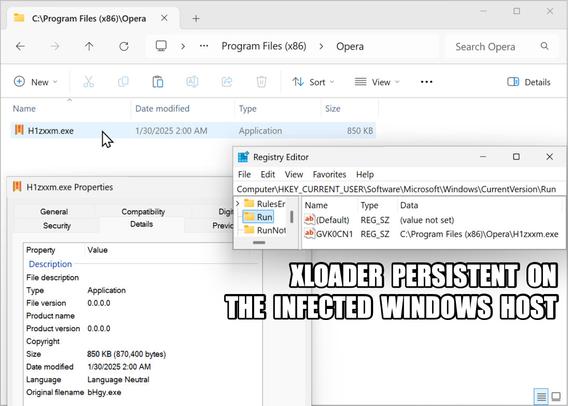
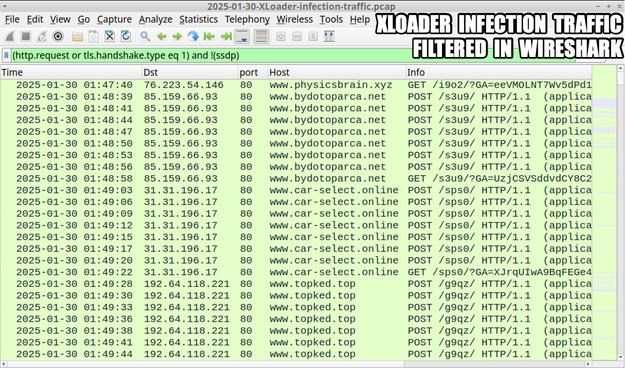
This article explores a new obfuscation technique used by threat actors to conceal malware within bitmap resources embedded in benign 32-bit .NET applications. The malware executes through a multi-stage process of extracting, deobfuscating, loading, and executing secondary payloads. The analysis focuses on a sample from recent malspam campaigns targeting financial organizations in Turkey and logistics sectors in Asia. The malware uses steganography to hide its payloads, making it challenging to detect. The article details the technical analysis of each stage, from the initial payload to the final execution of malware families like Agent Tesla, XLoader, and Remcos RAT. It also provides guidance on how to overcome this obfuscation technique using debugging methods.
Pulse ID: 681e0c16eca08864c8cd9614
Pulse Link: https://otx.alienvault.com/pulse/681e0c16eca08864c8cd9614
Pulse Author: AlienVault
Created: 2025-05-09 14:07:18
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#AgentTesla #Asia #CyberSecurity #ICS #InfoSec #MalSpam #Malware #NET #OTX #OpenThreatExchange #RAT #RCE #Remcos #RemcosRAT #Spam #Steganography #Tesla #Turkey #XLoader #bot #AlienVault